Zero Trust Security: The What, Why, and How
Learn more about the principles and benefits of zero trust, one of the best models for API security.
Built-in security features and a rich plugin ecosystem make it easy for you to customize and apply granular security policies for your APIs.
Implementing robust, layered API security measures helps prevent unauthorized access to your APIs and safeguards against API attacks.
Learn how League, a healthcare technology company, uses Kong’s extensibility to strengthen the security of their applications.
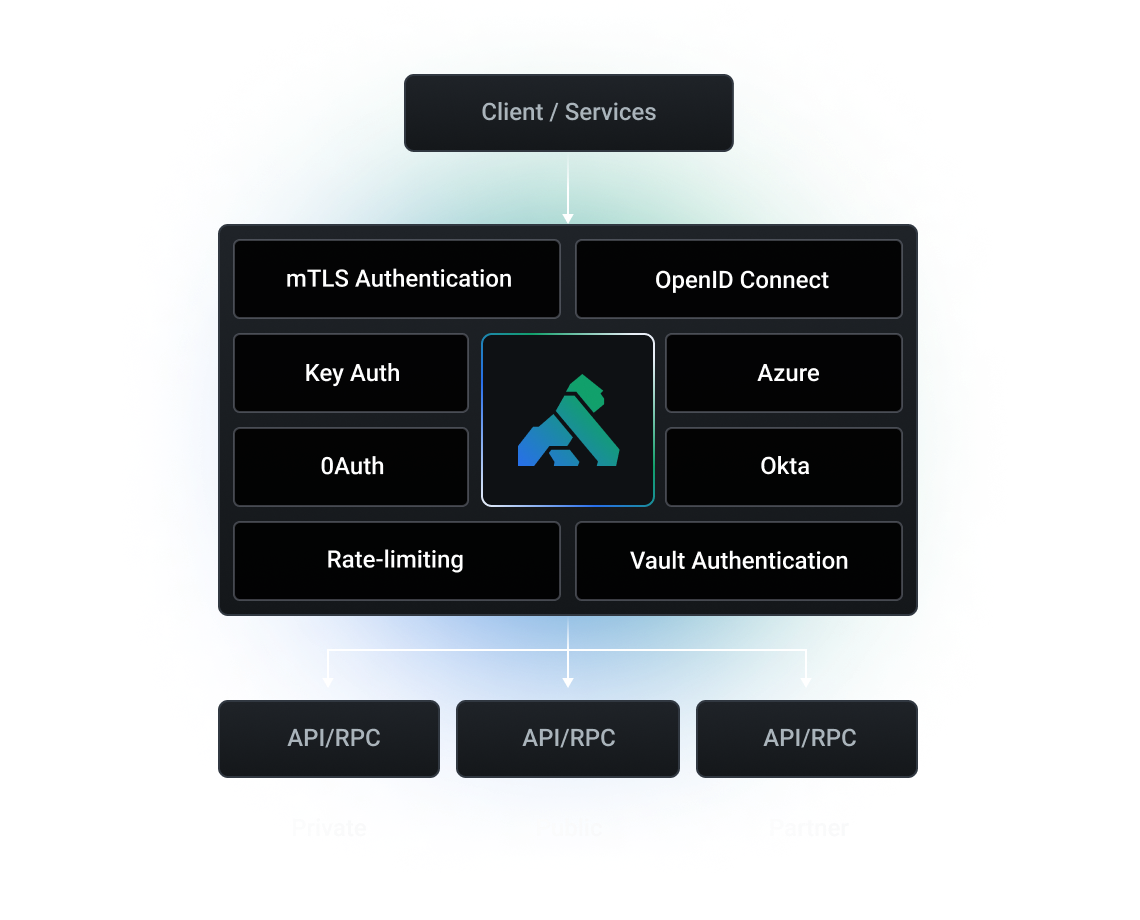
Create granular authentication and authorization policies using built-in and customizable security features.
Safeguard and manage your secrets from a single place with built-in and third-party secrets management and vault support.
Define and enforce your zero-trust security strategy consistently across different teams and applications through a single unified platform.

Program Kong Gateway declaratively to automate security policies. Customize security measures to address your specific requirements with Kong’s extensible security plugins that apply top-tier solutions for authentication, authorization, encryption, and more to your gateways.
Learn how Mercado Bitcoin leveraged Kong’s flexible plugin architecture and gained a 40% increase in mission-critical service performance.
Store and manage your keys, passwords, and tokens with Kong’s pre-built support for leading secrets management solutions, including AWS Secrets Manager and Hashicorp Vault. Protect your secrets whether you are running your applications on-premises, hybrid, in the cloud, or all the above. With Kong’s out-of-box solutions, there’s no integration work required.
Learn how PEXA swiftly improved their security posture and reclaimed developer productivity with Kong’s out-of-box solutions for standardized security.
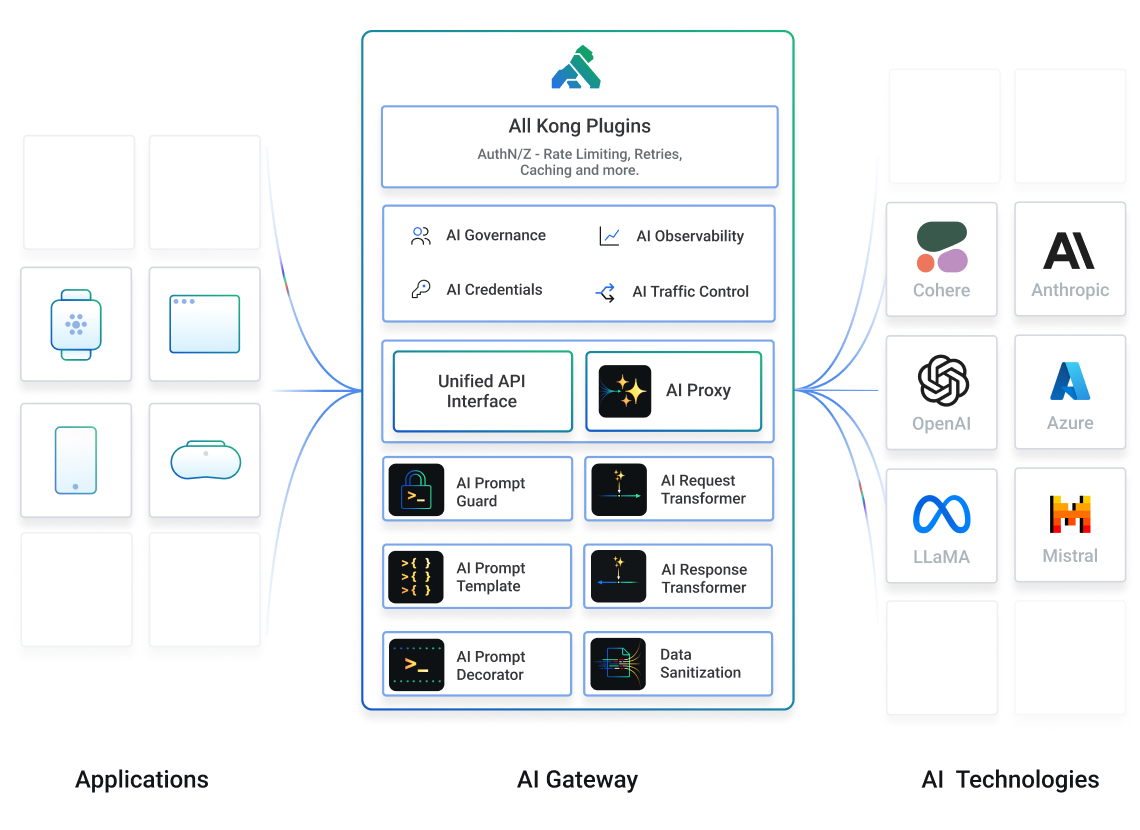
Transform any Kong Gateway into an AI Gateway. Securely manage all AI-related traffic, credentials, prompts, abuse prevention, observability, compliance, and governance across your organization for accelerated multi-AI application development.
Manage, govern, and apply zero-trust security to your meshes and gateways from a single unified platform. Kong offers an industry standard approach to zero-trust security with low operational complexity; Kong Mesh can be implemented in as little as a day and comes with out-of-the-box service connectivity and discovery.
Learn how Kong Mesh helped MS3 reduce complexity at scale without sacrificing end customer security and performance.
Kong named a Magic Quadrant™ leader for API Management, plus positioned furthest for Completeness of Vision.
Learn more about the principles and benefits of zero trust, one of the best models for API security.
Learn how an APIOps and automation approach to security can improve your organization’s security posture, retention of customer trust, and cost savings.
Learn about how to define, apply, and enforce governance policies consistently across API gateways, ingress controllers, and meshes.
Contact us today and tell us more about your configuration and we can offer details about features, support, plans, and consulting.