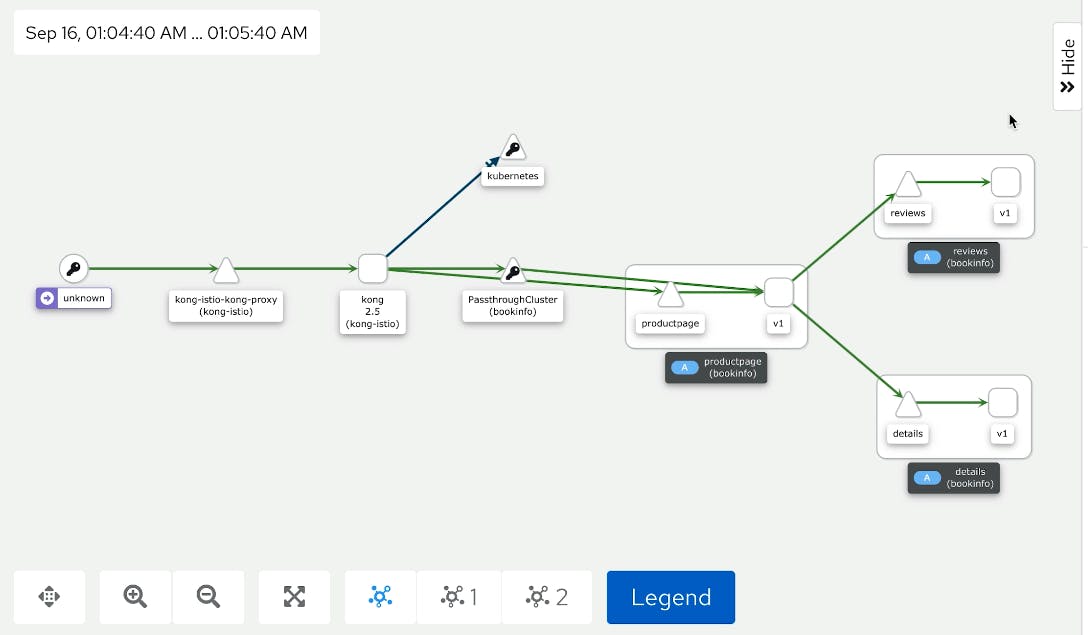
Have you ever found yourself in a situation where all your service mesh services are running in Kubernetes, and now you need to expose them to the outside world securely and reliably?
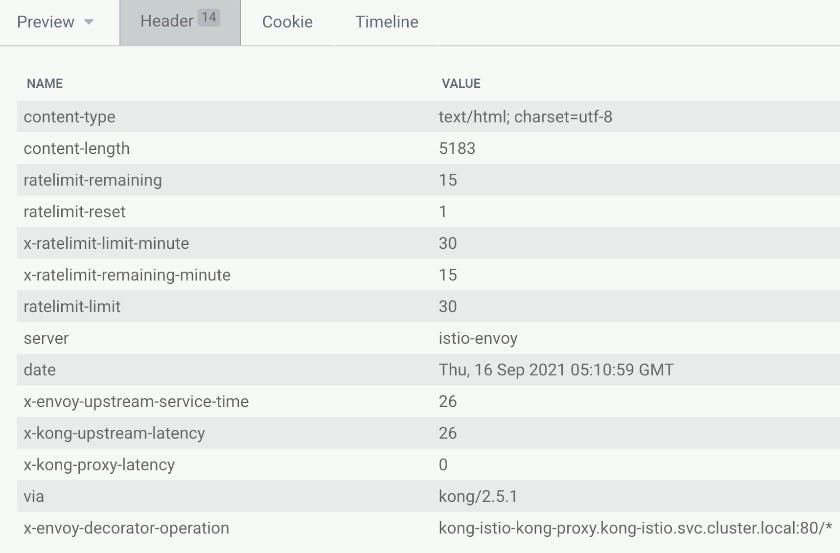
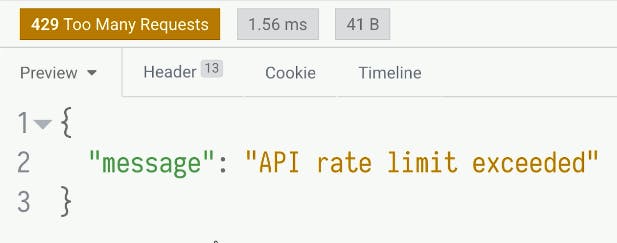
Ingress management is essential for your configuration and operations when exposing services outside of a cluster. You need to take care of the authentication, observability, encryption and integration with other third-party vendors alongside other policies.
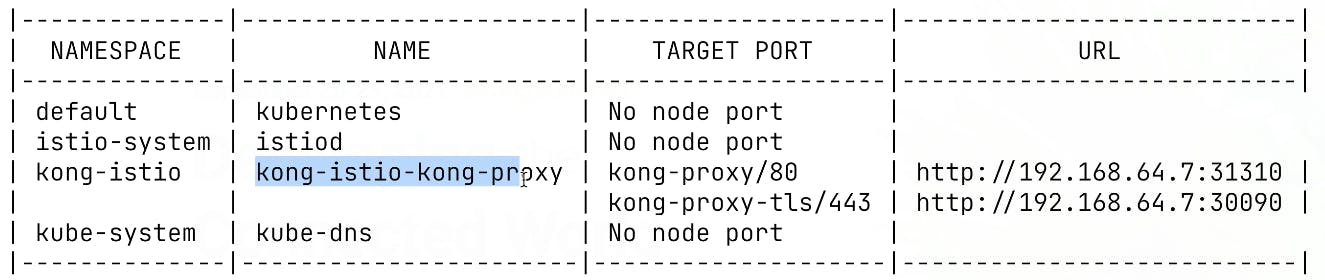
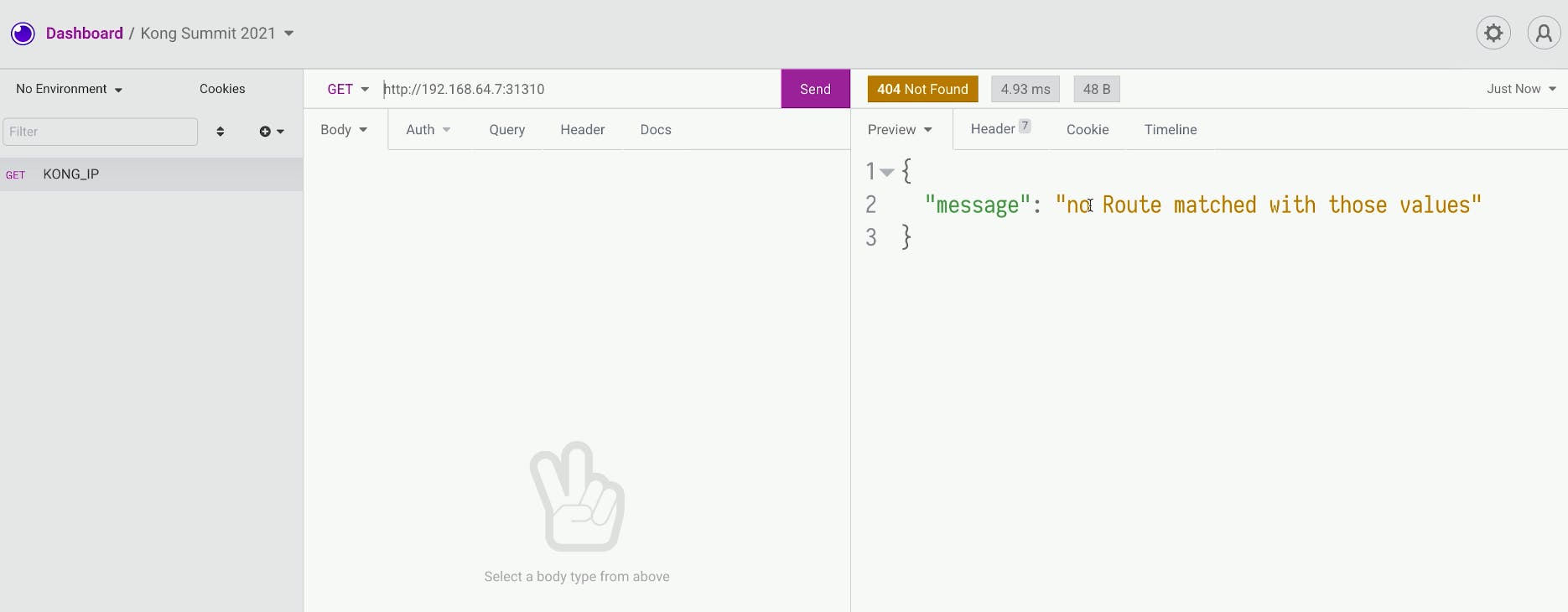
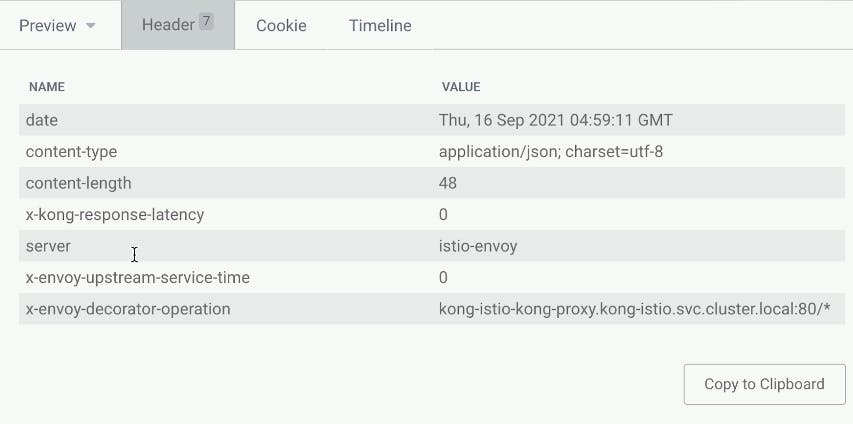
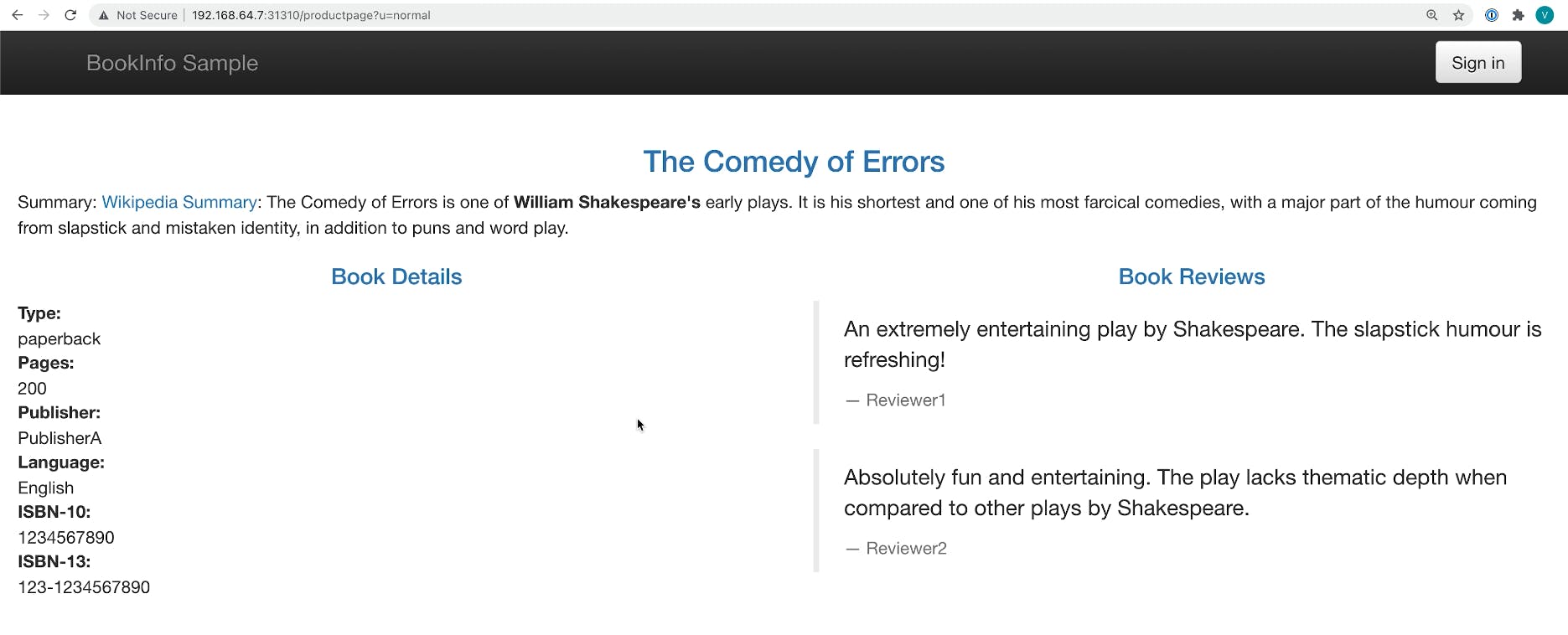
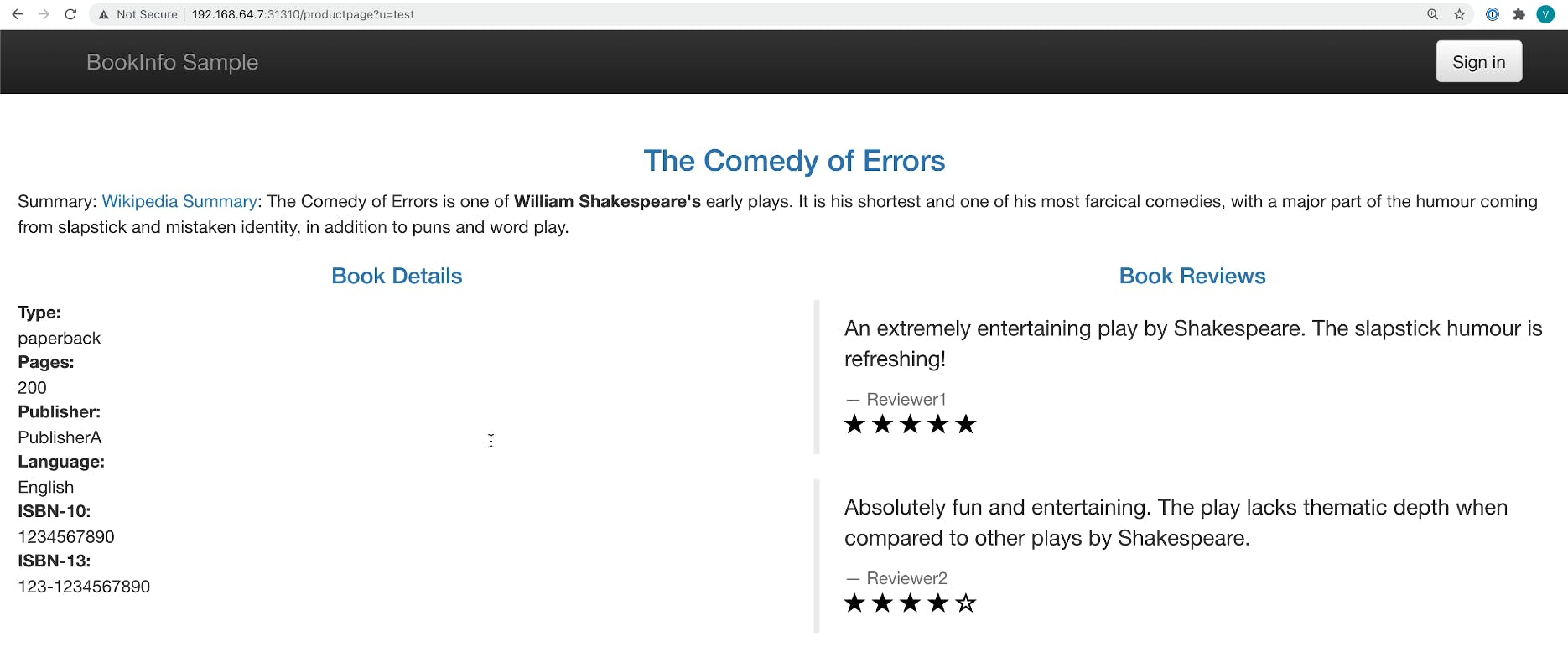
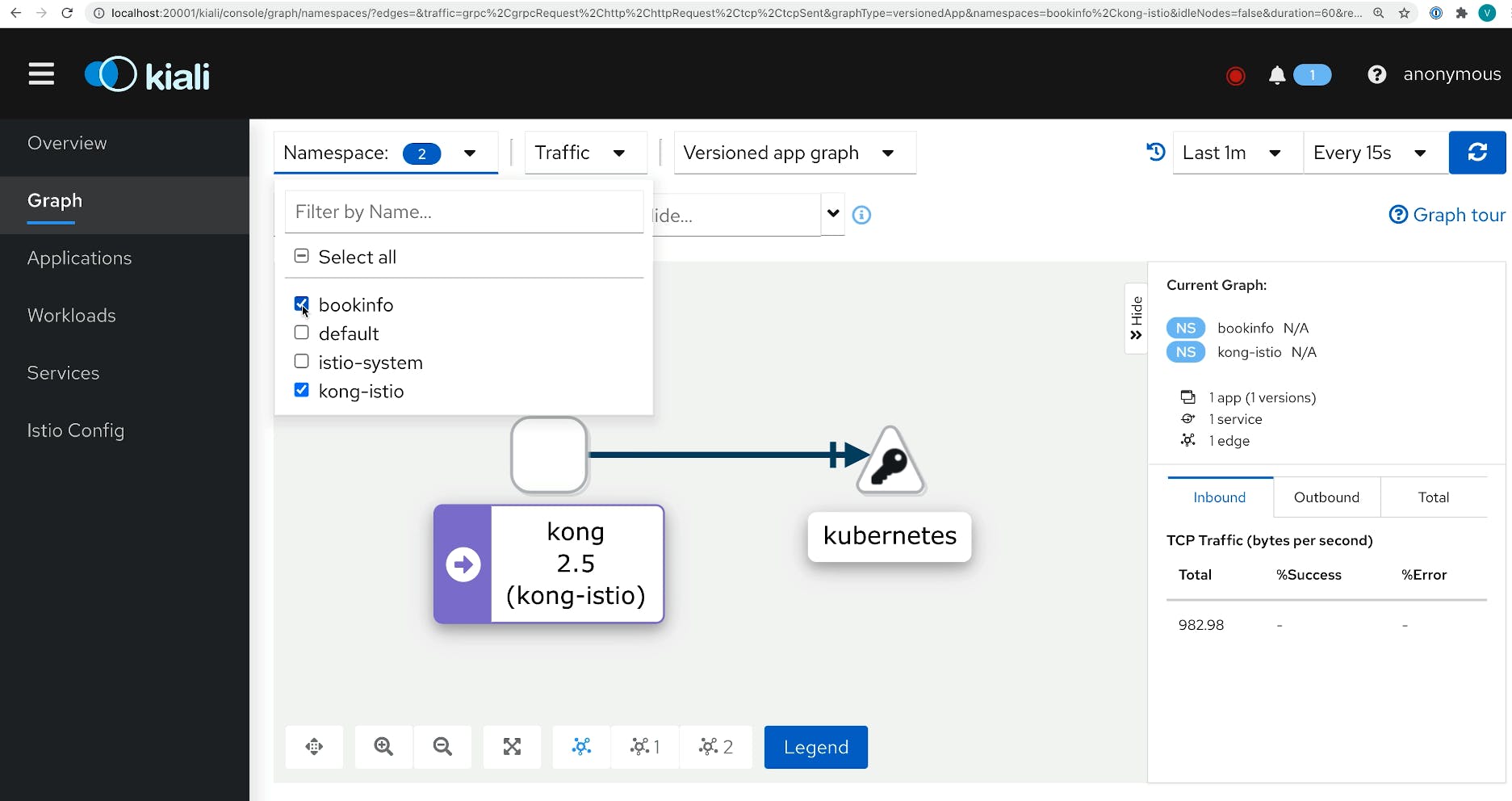
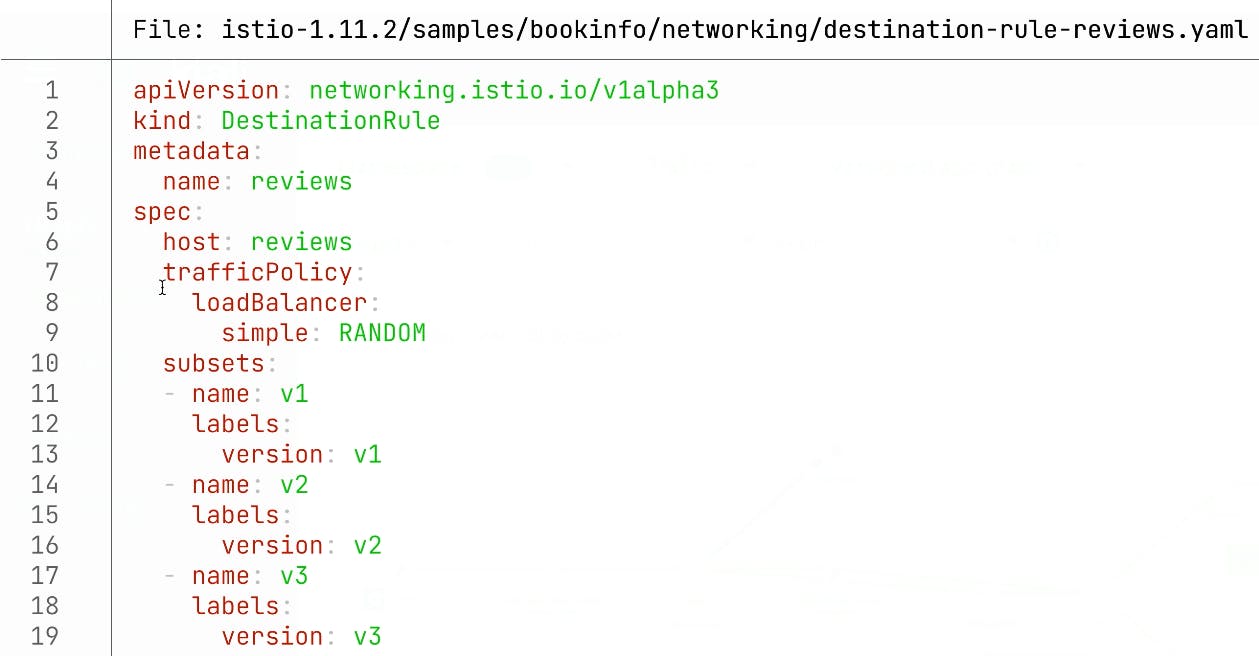
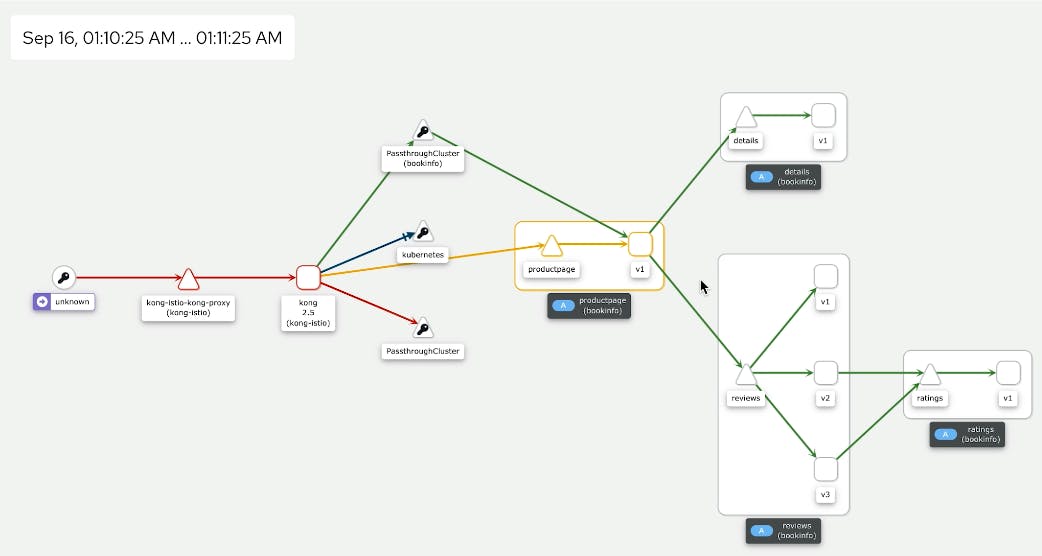
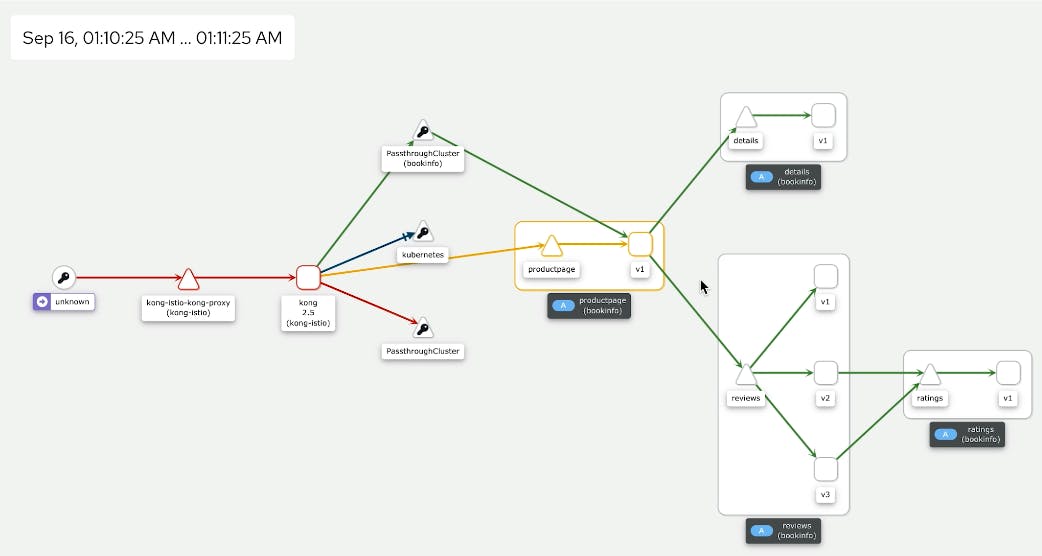
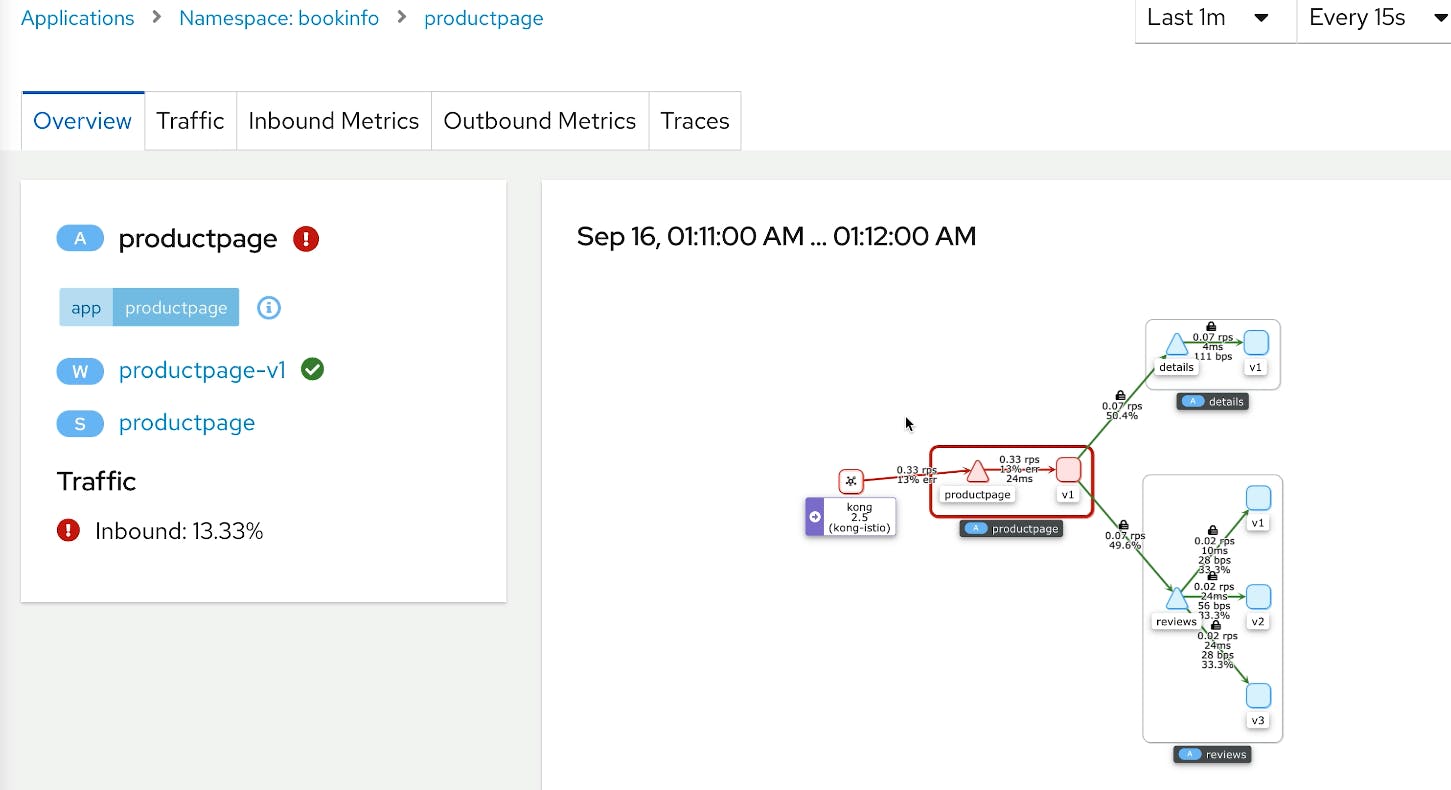
In this demo from Kong Summit, we'll use Istio service mesh and Kong Istio API Gateway (Kong Gateway + Kong Ingress Controller) to provide external access to the services that run inside the service mesh-enabled Kubernetes cluster.
For more information on Kong Istio Gateway, view our solutions page and the Kong Summit presentation from our CTO and Co-Founder, Marco Palladino.
What You'll Need
I used Minikube to run a local installation for this tutorial, but everything shown should still apply to any Kubernetes installation. For more information, view our documentation.
For the automated demo scripts, check out the demo-scene project on GitHub.