Access tokens
In token-based architecture, tokens represent the client’s entitlement to access protected resources. Access tokens (or bearer tokens as they're commonly known) are issued by authorization servers after successful user authentication. The tokens are passed as credentials in the request to the target APIs which inform the API that the bearer of the token is authorized to access the API and perform certain actions.
Challenges with access/bearer tokens
In the flows where access tokens grant access to protected resources, the legitimacy of the token bearer is assumed. Access is granted based on the validity of the token. There is no validation that the bearer is in fact the legitimate owner of the token. This is one of the main vulnerabilities of a bearer token.
If the tokens fall into the hands of bad actors, they can be misused. With the stolen or leaked tokens, bad actors can easily impersonate the user and obtain unauthorized access to protected resources.
For any average API provider, this is a major concern. Recently, Sourcegraph experienced a security incident with leaked admin tokens. The malicious users used their privileges to increase API rate limits for a small number of users. For environments with heightened security needs, stolen or leaked tokens are a serious security risk.
A solution to secure access tokens
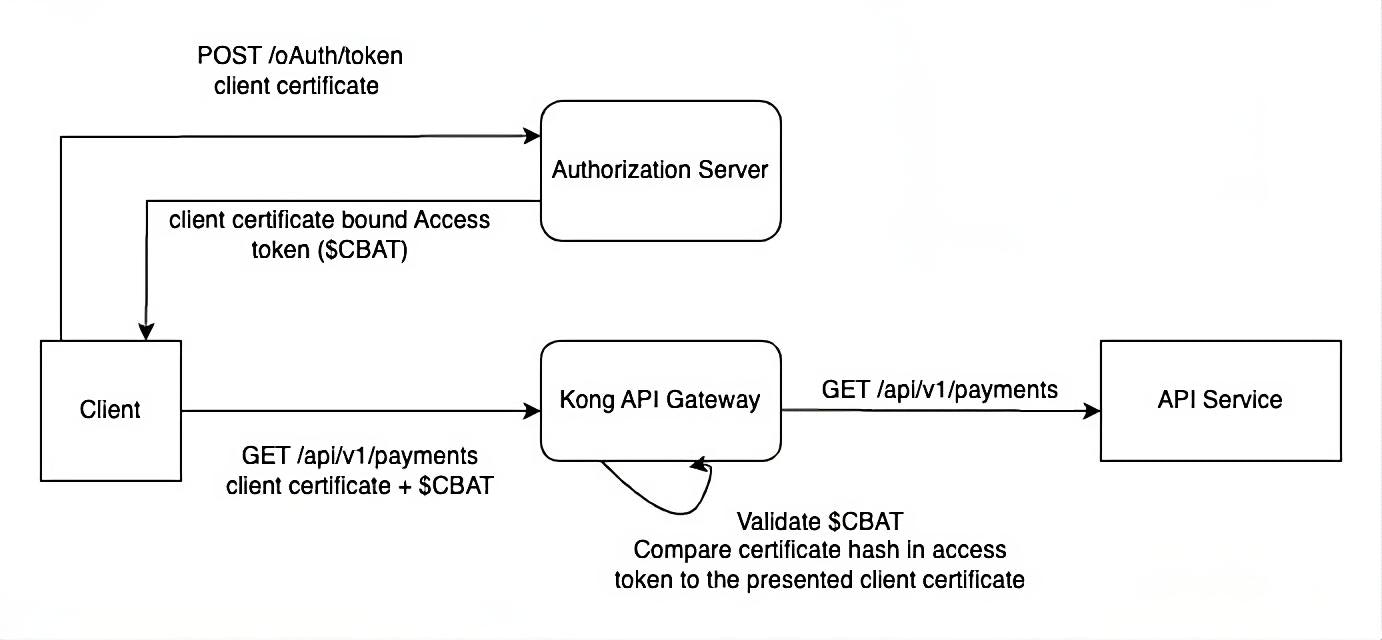
A solution to this problem is constraining the tokens issued by authorization server to clients (sender-constrained tokens) so only the entity/client to whom a token was issued can use the token to access resources. This approach is also known as holder of key or proof of possession tokens.
The client presenting the access token has to prove that they are authorized to use the token. To achieve this, the authorization servers bind the tokens to the client's cryptographic keys. Resource servers can then validate the clients are in possession of those keys and grant/deny access accordingly.
Advantages of sender-constrained tokens
The primary security vulnerability of standard bearer tokens is remediated, as the legitimacy of the bearer is verified. Access to the protected resource is granted after successful validation of
- The client certificate used in the connection
- The thumbprint of the client certificate in the token matching the client certificate in the underlying connection
- Token validity
For environments with high security requirements such as financial services, e-health, and e-gov, this added layer of token security mitigates the risk of misuse of tokens as sender-constrained tokens simply cannot be replayed or redirected by an unauthorized party.
Moreover, usage of sender-constrained tokens is a must in open banking. One of the requirements of financial API (FAPI 2.0) is for the resource servers to support and verify sender-constrained access tokens using either of the methods.
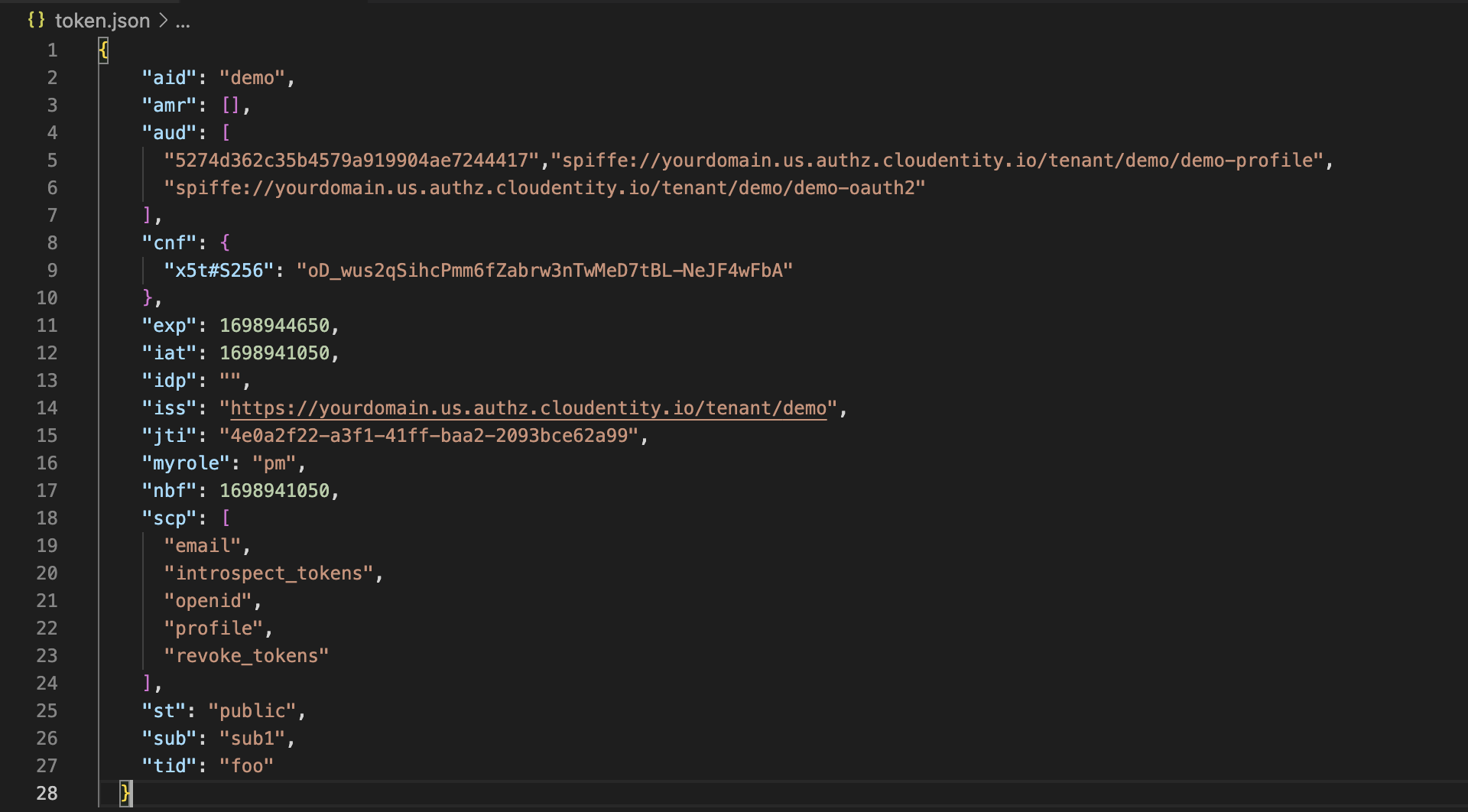
Example of an access token with certificate thumbprint