The Neosec platform integrates with Kong Gateway Enterprise, an API Management Solution, to provide automated and continuous API discovery, API risk posture alerting and API protection through behavioral analytics and response automation. And it does all that while being out of band, using the logs shipped from Kong to Neosec.
API Security
APIs, by definition, expose your applications to an open and to a large extent, a hostile environment. Malicious actors can breach your systems and data from many different perspectives: exuberant mechanisms like brute force attacks to DDoS, SQL injection, CSS and subtle phishing messages.
From the API consumption perspective, we could classify security policies in two main levels of abstraction:
- Request-based policies: analyzes each request to make sure it’s reliable to route to upstream services sitting behind the API gateway
- Behavioral-state policies: based on collections of requests to make sure there’s no anomalous consumption pattern
Request-Based Policies With Kong Gateway Enterprise Plugins
Kong plugins are available to implement security mechanisms for the request-based policies, including:
- OpenID Connect: Implement enterprise-wide authentication, SSO and MFA processes based on best-of-breed Identity Providers
- JWT: Verify requests containing signed JSON Web Tokens
- Mutual TLS (mTLS): Build encrypted tunnels for consumer and Kong Gateway traffic based on digital certificate exchange
- OPA: Implement access control policies along with the Open Policy Agent
- KeyAuth: Add Key Authentication to Kong Services, Routes and Consumers
- Basic Authentication: Add Basic Authentication with username and password protection
- LDAP-Based Authentication: Integrate Kong with LDAP Servers
Behavioral-State Policies With Neosec
The Neosec platform sanitizes and enriches all API activity data, performs big data behavioral analytics and stores it in a data lake. This allows you to immediately understand your API risk posture and get alerted on API attacks, as well as to query, investigate bugs and support cases, and hunt for threats.
You can create response policies in the Neosec platform to automatically respond to behavioral analytics alerts at the logical entity level.
In this blog post, we'll show how you can easily integrate Kong and Neosec and create automated response policies that respond to behavioral analytics alerts by performing actions on Kong consumers.
Kong + Neosec Architecture
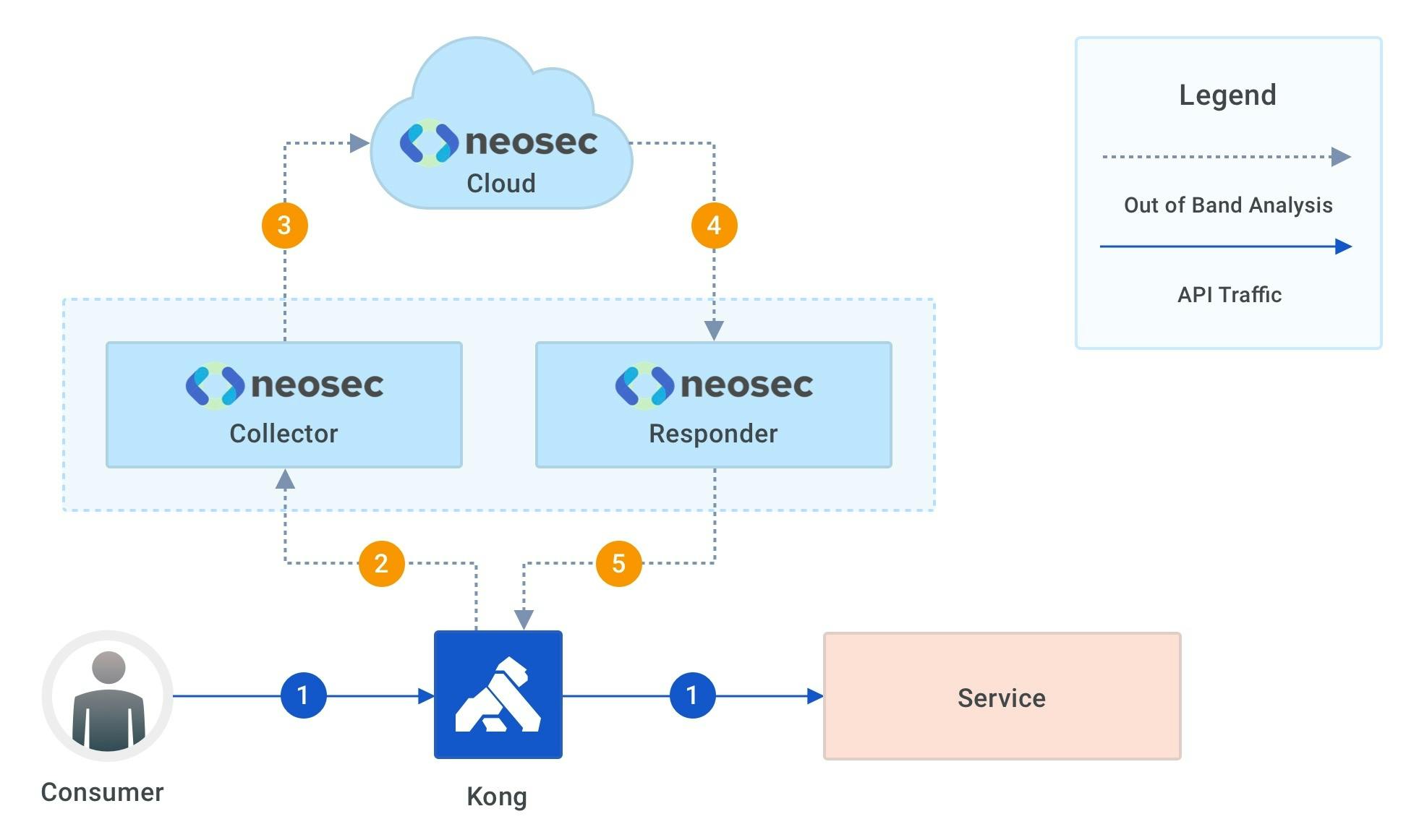
Diagram 1. Flow
Here's the flow of events in the environment:
- API traffic flows directly into the APIs via the Kong data plane (Kong Gateway or Kubernetes Ingress Controller). There are no inline components to potentially obstruct that flow.
- The Kong data plane sends logs using the standard TCP Log plugin to the Neosec Collector running on the customer premises.
- The Neosec Collector normalizes, sanitizes, micro-batches and sends the logs for processing to Neosec Cloud.
- If Neosec detects malicious traffic (e.g., a credential stuffing attack, data scraping), the Neosec analytics and alerting engines trigger an alert. Given that the triggered alert matches an automated response policy previously configured by the user, said response policy is sent to the Neosec Responder to enact.
- The Neosec Responder applies the response policy to the API gateway configuration through the Kong Manager Admin API, using standard Kong plugins such as Request Termination and Rate Limiting.
Sending API Activity Data
Setting up a Neosec Collector to consume logs from Kong Gateway is trivial, as the Collector can run as a container, a serverless function or a system service. You only need to configure the in-built Kong TCP Log plugin to send data to it.
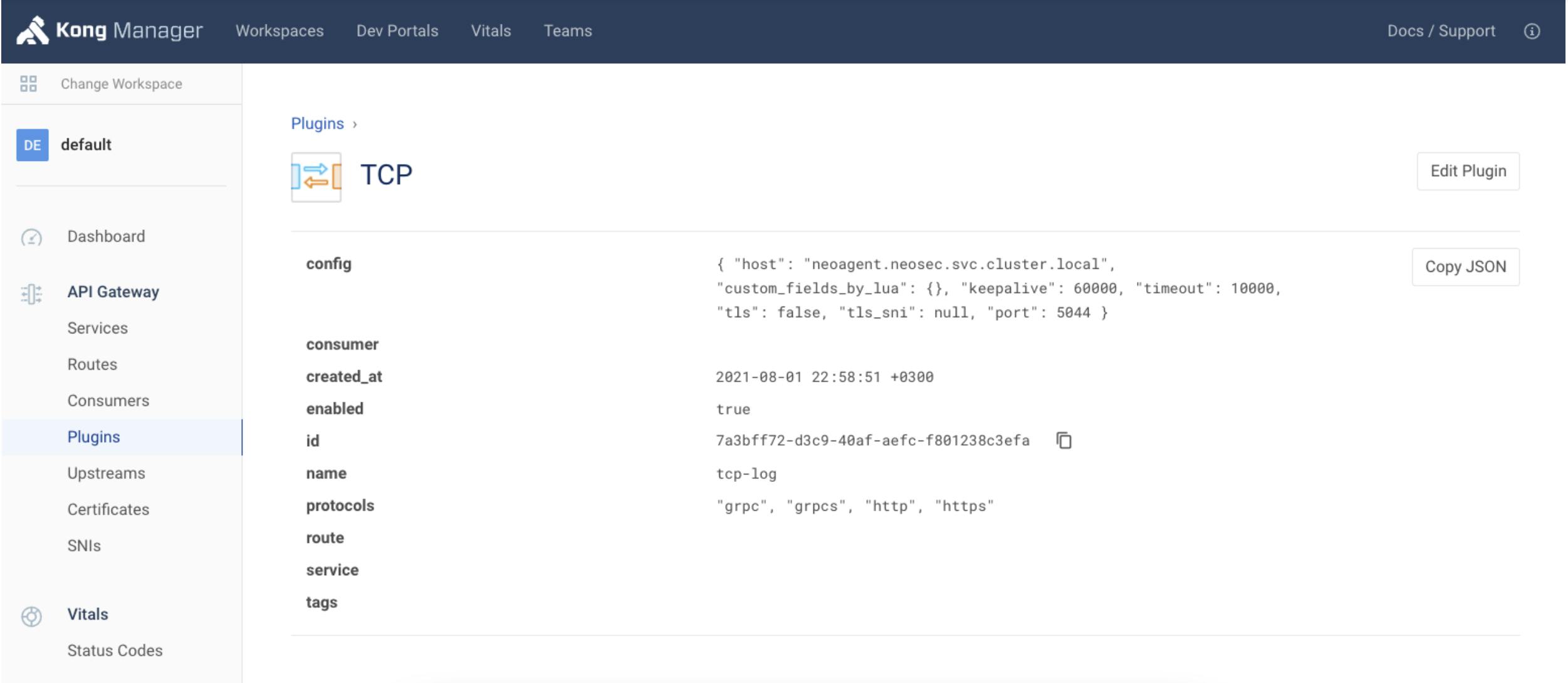
Diagram 2. TCP Log Plugin Configuration
All you need to do is:
- Create a new TCP plugin in Kong Manager.
- Enter the Collector's URL and port in Config.Host and Config.Port.
- Optionally. enable Config.Tls and enter the SNI.
Now that data flows from the Kong data plane to the Neosec Cloud, the Neosec platform goes into action by automatically discovering all APIs and establishing baselines of activity and behavior.
Now that data flows from the Kong dataplane to Neosec; the Neosec will automatically discover all APIs and establish baselines of activity and behavior for each.
Since you are most likely managing authentication using Kong security plugins like the ones listed above, the logs from the Kong dataplane already contain essential information about API consumers.
Discover Your APIs
The Neosec Discovery page shows you all you need to know about the various services and endpoints discovered, including statistical data, classification of the data flowing over them, their risk posture, etc.
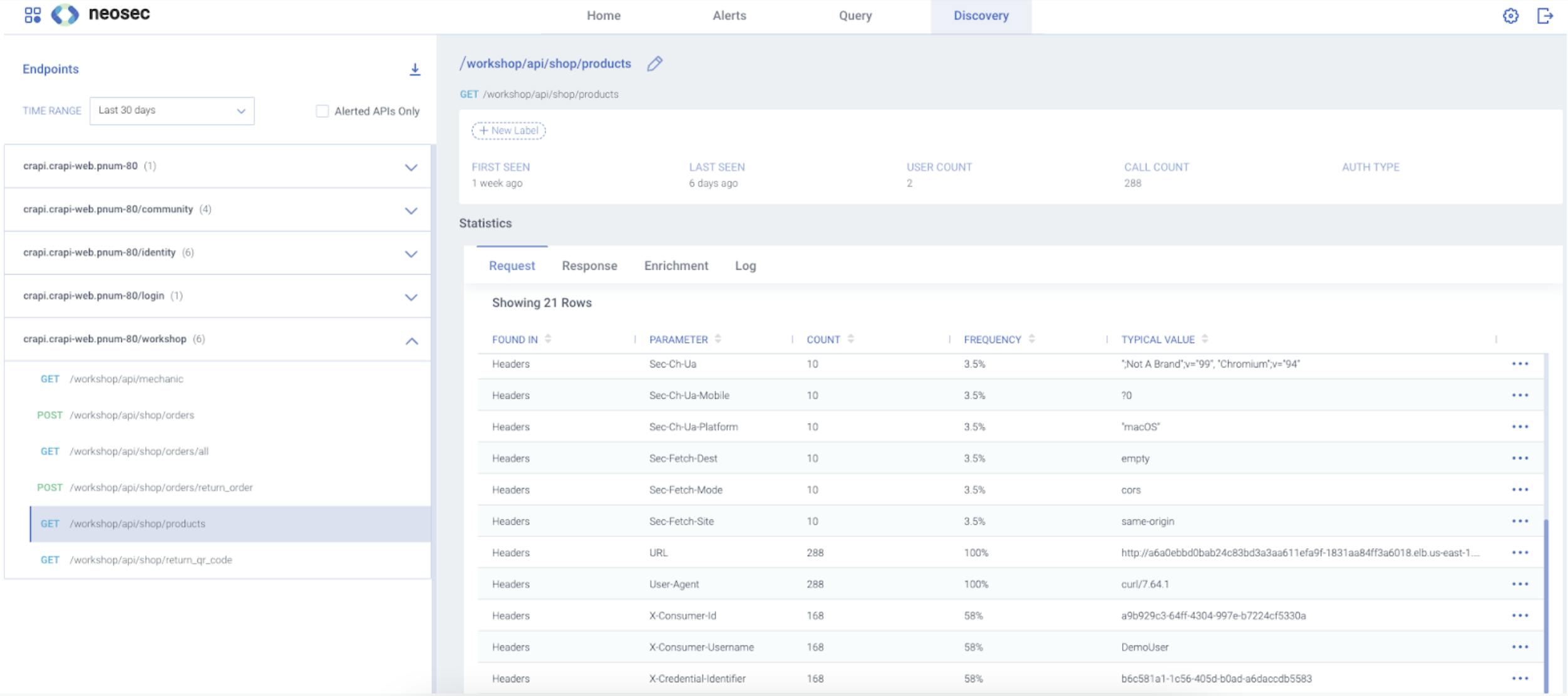
Diagram 3. Discovered APIs and Endpoints
Alerting on API Abuse
The Neosec platform is now monitoring API activity for any sign of malicious activity. For example:
- Credential stuffing attacks, credential sharing and "impossible time travel"
- Suspicious data access patterns
- Abnormal parameter values
And while you can easily send these alerts to your SIEM or SOAR tools, the real trick is shutting down attacks as they happen. To do this, we turn to the other side of the Kong + Neosec integration: automated response policies.
Automated Response
The move from passive API analytics to taking a security counteraction is seamless and straightforward using Neosec automated response policies. The Neosec platform enables you to create detailed response policies, all the way down to specifying the services, endpoints and consumers involved.
In the Neosec platform, we set up an automated response policy to permanently block a consumer that triggers a request spike alert in the following example. The condition can be as detailed as you want it to be, and include references to consumer IDs or other alerted entities, APIs, endpoints, and so on.
In the action portion of the policy, we choose to block the consumer using the standard Kong Request Termination plugin. We could set a timeout for that block, or we could decide to rate-limit the consumer.
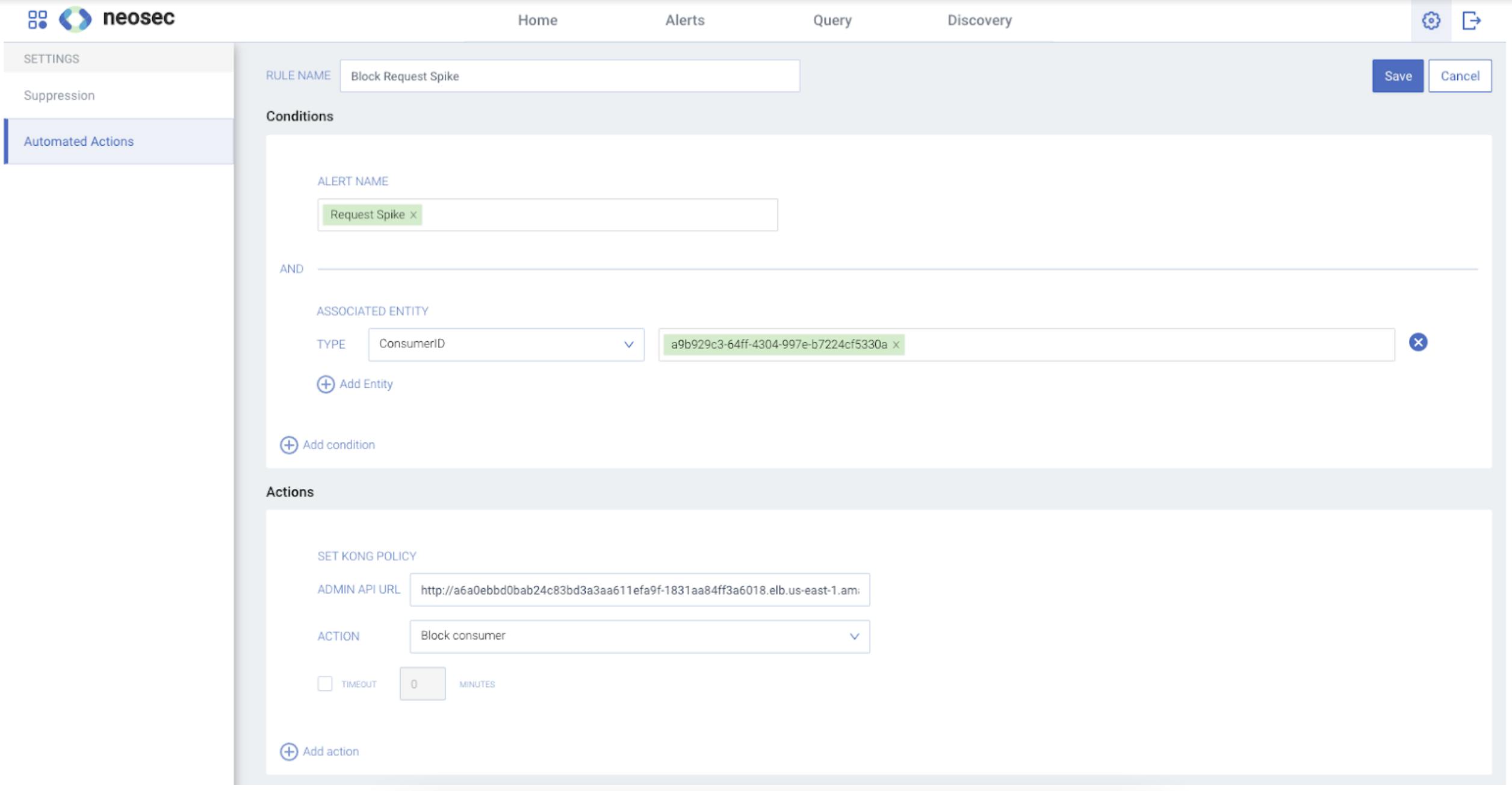
Diagram 4. A Kong Automated Response Policy
Seeing It in Action
Let's bombard an endpoint in a loop and wait for the Request Spike alert to trigger.

Diagram 5. API Call Loop Progressing and Getting Blocked
The instant the Request Spike alert triggered, the automated response policy shot into action. We can see this Request Spike alert in the Neosec UI:
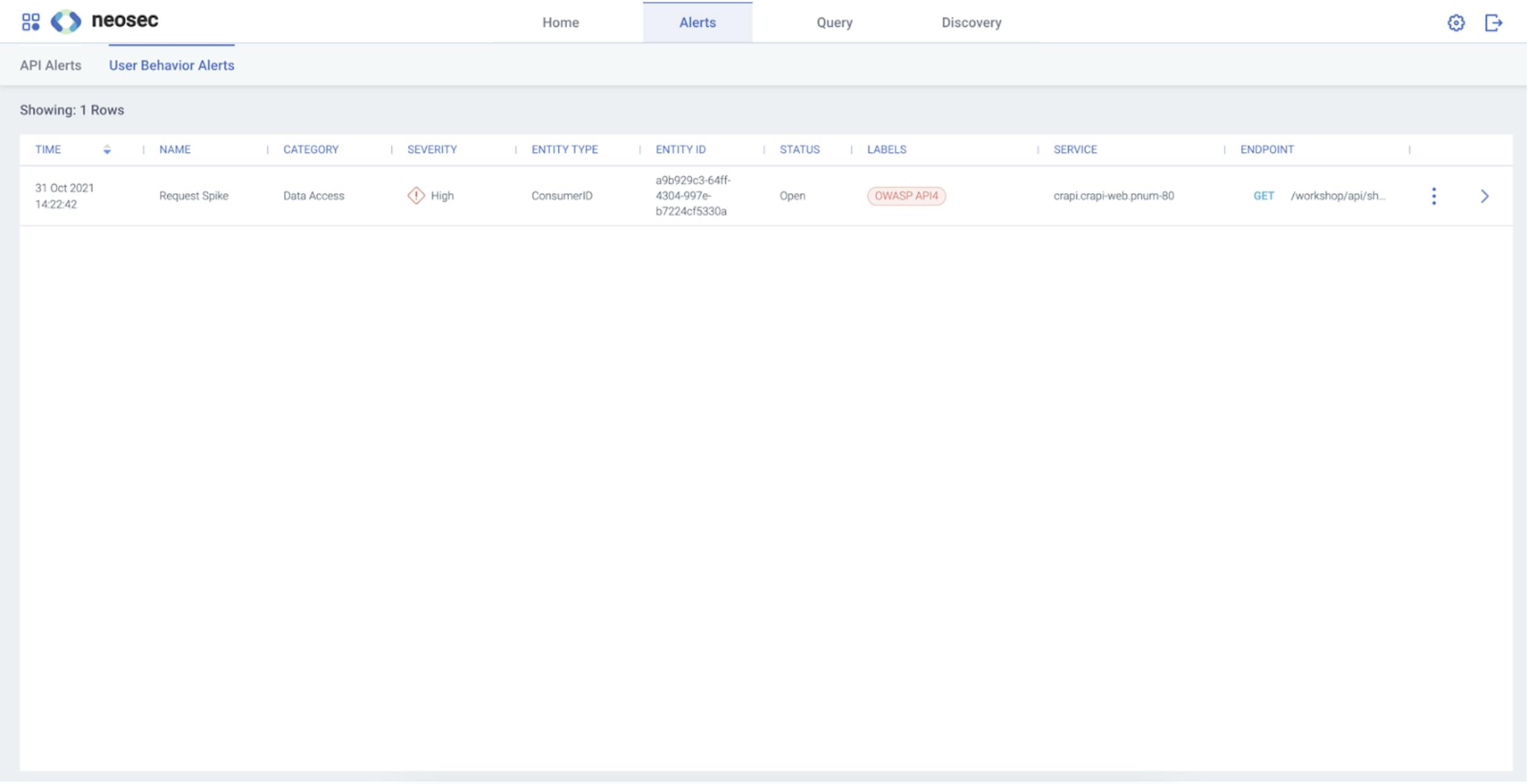
Diagram 6. Request Spike Alert
We can also see the policy applied automatically in Kong to the malicious consumer in the Kong Manager:
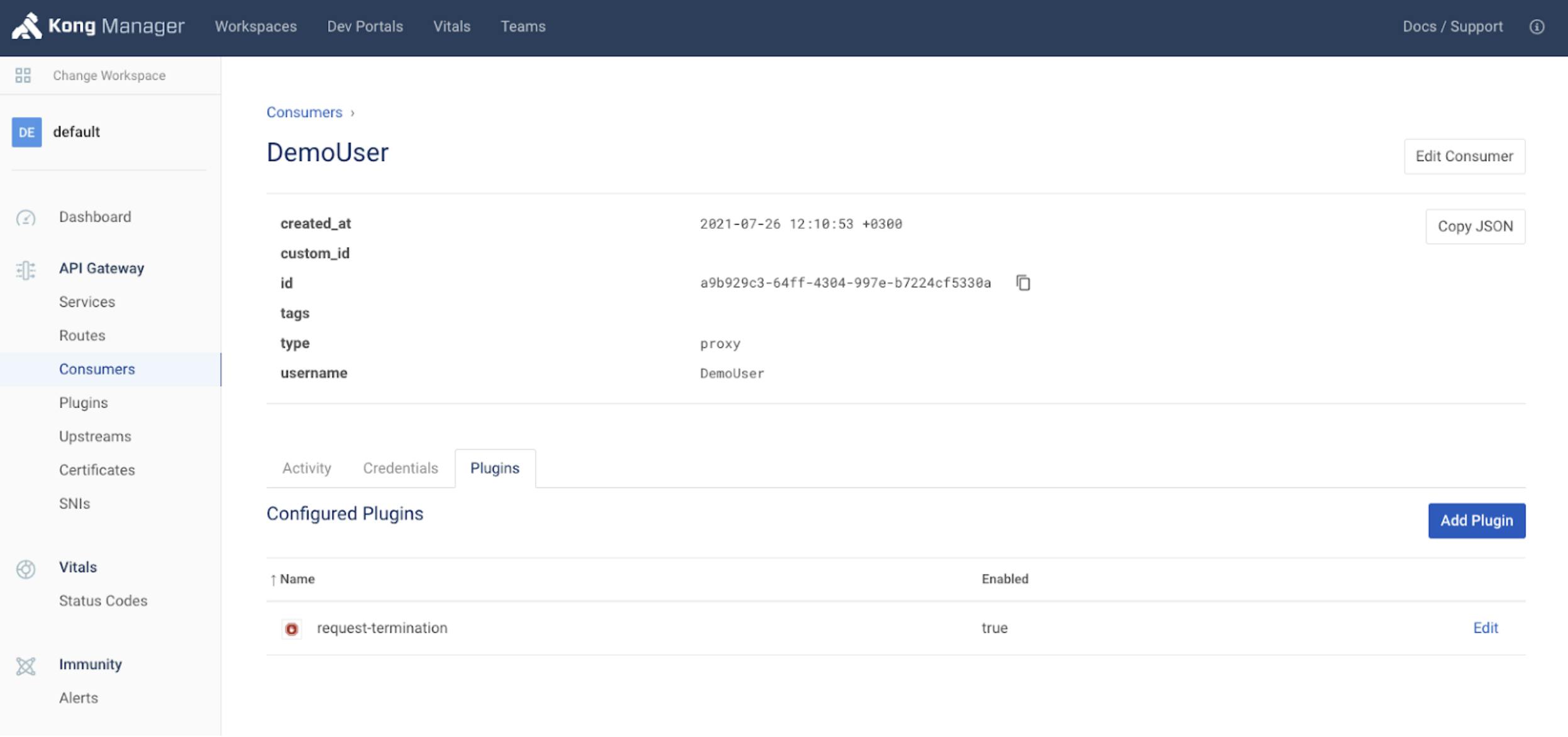
Diagram 7. Kong Request Termination Plugin Set For Consumer
One of the benefits of having an enriched data lake in the Neosec Cloud is that you can pivot to any consumer's timeline (or any other entity's timeline) to see everything they did. When we investigate the Request Spike alert from Diagram 5, we see all the consumer's activity leading up to the alert triggering.
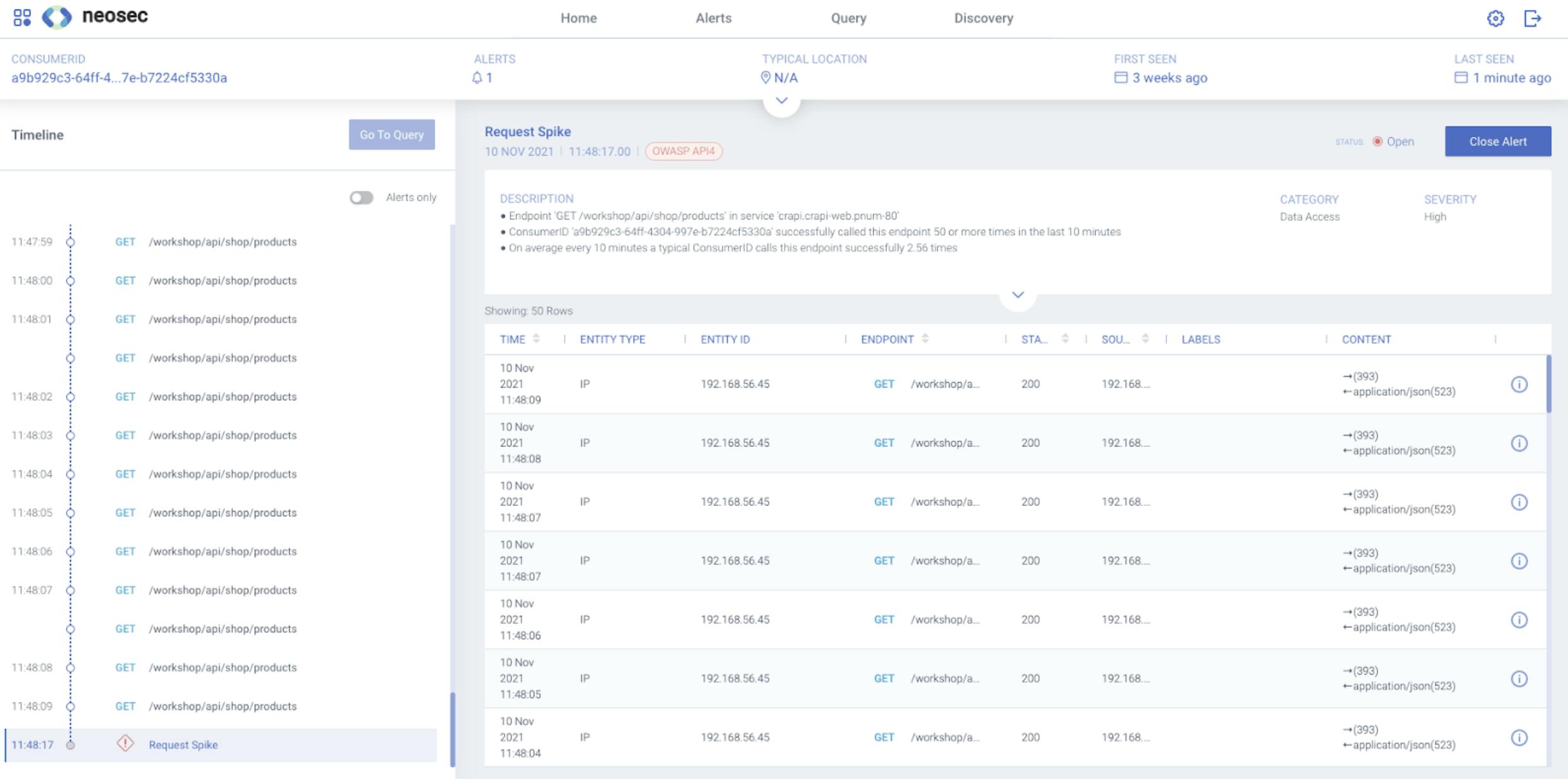
Diagram 8. The Offending Consumer's Timeline
The Power of Partnership
The Neosec + Kong partnership adds an innovative API security platform to help Kong customers discover and protect their APIs. The SaaS platform from Neosec performs enterprise-wide discovery of the entire API estate and audits the risks found in each API. But the true power of Neosec is the ability to understand the behavior within each API.
To differentiate normal from abnormal behavior gives Kong customers unparalleled insight into their API traffic. Visibility is the first step, but automatically responding to bad behavior and enforcing remediation through the Kong API gateway brings Kong customers real control.
Getting started is easy; you can request a free trial from both Kong and Neosec and follow the instructions above.