AWS Lambda as the AppSync Authorization Method
We’re going to explore another AppSync Authorization Method, replacing the existing one based on API Key to another using an AWS Lambda Function. With this, we’re able to remove the x-api-key header from the request, leaving both AppSync and Konnect Control Plane to check the Bearer token with the PAT instead.
The AWS Lambda Function
First of all, create an IAM role to be used by the Lambda function. Create a role.json file with:
Create the IAM Role with the following command:
AWS Lambda Function
Create another file, named isauthorized.py, with the actual function code written in Python. Notice the function is extremely simple, just checking if the request has a Bearer token injected. Please, bear in mind the Authorization logic can go as complex as we want.
Zip the file:
Create the konnectIsAuthorized Lambda function:
You can invoke the function to test it:
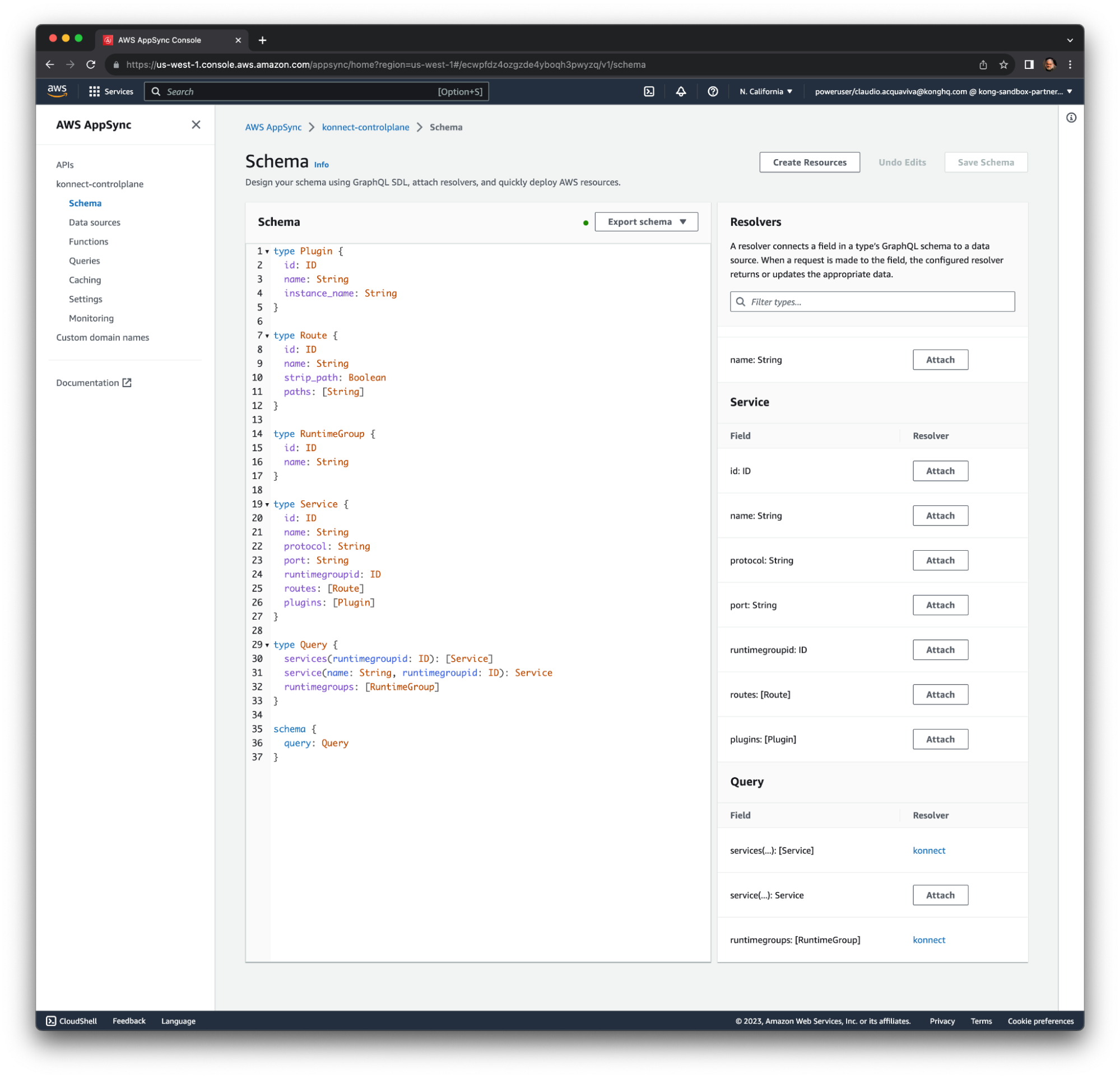
Change the GraphQL API Authorization Mode
Now we’re ready to replace the existing authorization mode with the Lambda function based one:
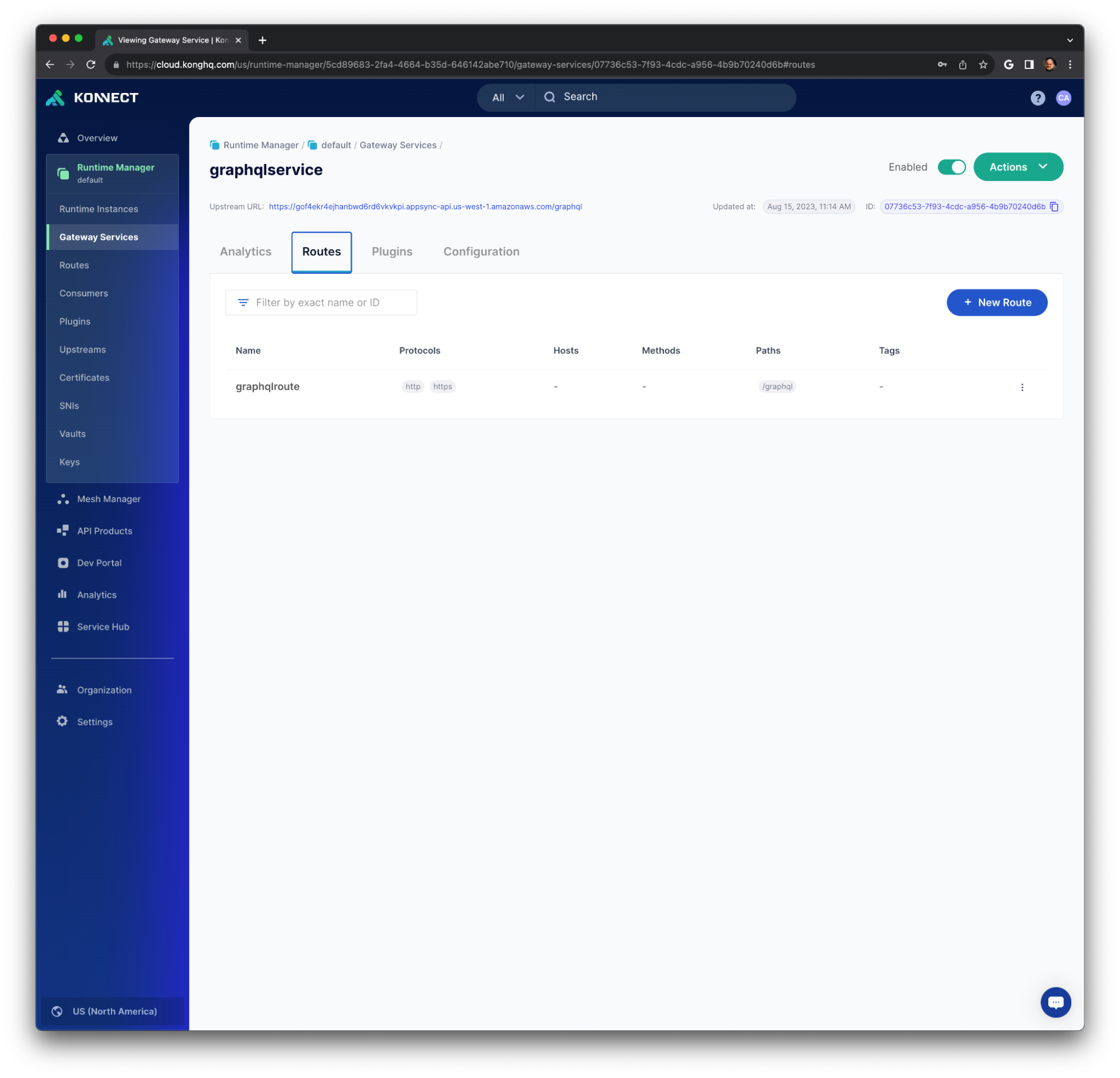
Send new Requests to the Konnect Runtime Instance
We should get a similar response if we send a request to the Runtime Instance. For a simple test, the curl command uses the -k option to accept the Konnect Self-Signed Digital Certificate. Moreover, we don't need to inject the x-api-key AppSync Header, since our Lambda function is responsible for the AppSync Authorization mode.
GraphQL Rate Limiting Advanced Plugin
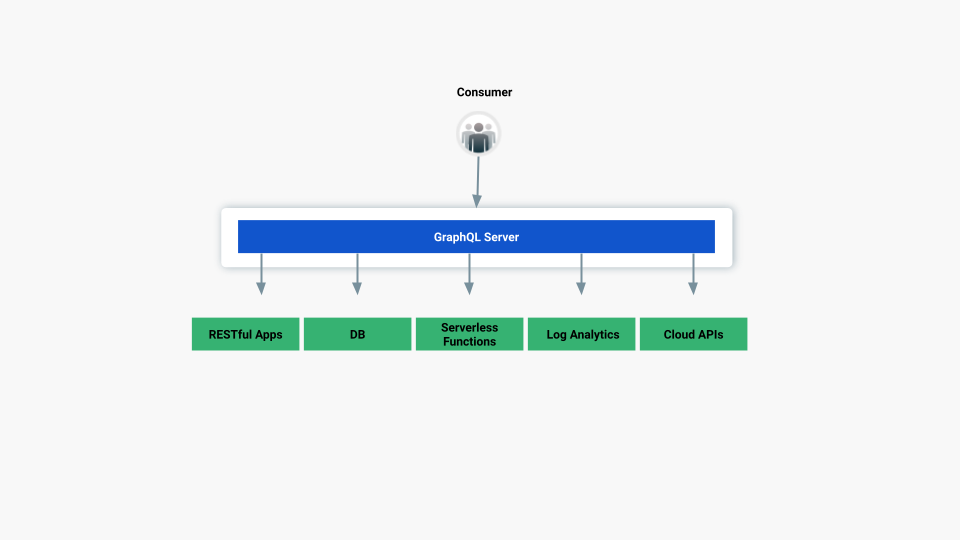
So far, we have deployed the Konnect Runtime Instance in front of the AWS AppSync API. However, there's no policy controlling how the GraphQL API has been consumed. Now, it’s time to enable the GraphQL Rate Limiting Advanced Plugin to our Kong Service.
The GraphQL Rate Limiting Advanced plugin provides rate limiting for GraphQL queries. The GraphQL Rate Limiting plugin extends the Rate Limiting Advanced plugin.
Due to the nature of client-specified GraphQL queries, the same HTTP request to the same URL with the same method can vary greatly in cost depending on the semantics of the GraphQL operation in the body. A common pattern to protect your GraphQL API is then to analyze and assign costs to incoming GraphQL queries and rate limit the consumer’s cost for a given time window.
GraphQL query costs are evaluated by introspecting the endpoint’s GraphQL schema and applying cost decoration to parts of the schema tree. Learn more about GraphQL Queries Cost Management on the specific GraphQL Rate Limiting Advanced Plugin documentation page.
Install Redis
As a best practice for Runtime Instance deployments, we should externalize the limits to an external Redis infrastructure. In this sense, all Kubernetes replicas of the deployment will rely on the same limits. To support a configuration like this, the GraphQL Rate Limiting Advanced Plugin provides multiple strategies, including Redis.
You can have your Redis infrastructure running on a totally and independent environment, for example, leveraging the AWS ElastiCache for Redis. To have a simpler deployment, you can run Redis in the same EKS Cluster with this declaration.
Apply GraphQL Rate Limiting Advanced plugin to the Service
Finally, let's enable the plugin to our Service. Notice we’re using a simple limit and window_size to exercise the rate-limiting policy. Also, we can tell where the Redis endpoint is using the Kubernetes Service FQDN, redis.redis.svc.cluster.local.
Send new Requests to the Runtime Instance
This time we’re using the -v option for curl to see the Rate Limiting related Headers: X-Gql-Query-Cost, X-RateLimit-Limit-30 and X-RateLimit-Remaining-30.
If you keep on sending requests to Konnect Runtime Instance you'll get a 429 error code:
Conclusion
Kong Konnect simplifies API management and improves security for all services including GraphQL infrastructure. Try it for free today!
This blog post described Kong Konnect’s capabilities to:
- Embedded its RESTful Admin API to support GraphQL for the Konnect Control Plane administration.
- Expose and protect an AWS AppSync API with enterprise-wide policies implemented by the Konnect Runtime Instance.
The next blog post of this series will describe how to implement other GraphQL operations: Mutations and Subscriptions. Stay tuned!