Recent leaks have once again brought API and data security concerns into the spotlight. Specifically, the leaks pointed at the following as major areas to consider when thinking through your API and data security strategies:
- Collection governance and access control
- Data storage and syncing
- Role-based access control and automated enforcement of access control best practices
- Encryption and location of encryption logic
When considering the above, it’s critical to think about best practices across every stage of the API lifecycle, starting with the initial phases of API design and testing. To help organizations strengthen and properly manage their API and data security postures, we built Kong Insomnia into the larger API platform offering here at Kong. Compared to a tool like Postman, Insomnia was built from the ground up to support advanced security use cases and sensitive data environments.
In this blog, we’ll cover how to leverage some of Insomnia’s security-oriented differentiators to address concerns related to the recent data leak.
Prevent data leaks with collection governance and RBAC
Collection governance is the process of implementing access controls around API collections to prevent data leakage. This is especially crucial when sharing APIs with external collaborators, as improper API access control could invite malicious actors to easily obtain and misuse sensitive business data.
Insomnia prioritizes collection governance by ensuring collections are never publicly available by default — only explicitly authorized users can access them. With RBAC (role-based access control), admins can assign permissions, enforce strict access controls, and manage whether collections are allowed to be synced to the cloud. Private environments add another layer of protection by ensuring that sensitive data, like API keys, are never synced and always remain local.
Insomnia also integrates with popular third-party vaults like AWS Secrets Manager, Azure Key Vault, GCP Secret Manager, and HashiCorp Vault — enabling streamlined secrets management and removing the need for plain-text storage. This is available out-of-the-box, with no additional add-on fee.
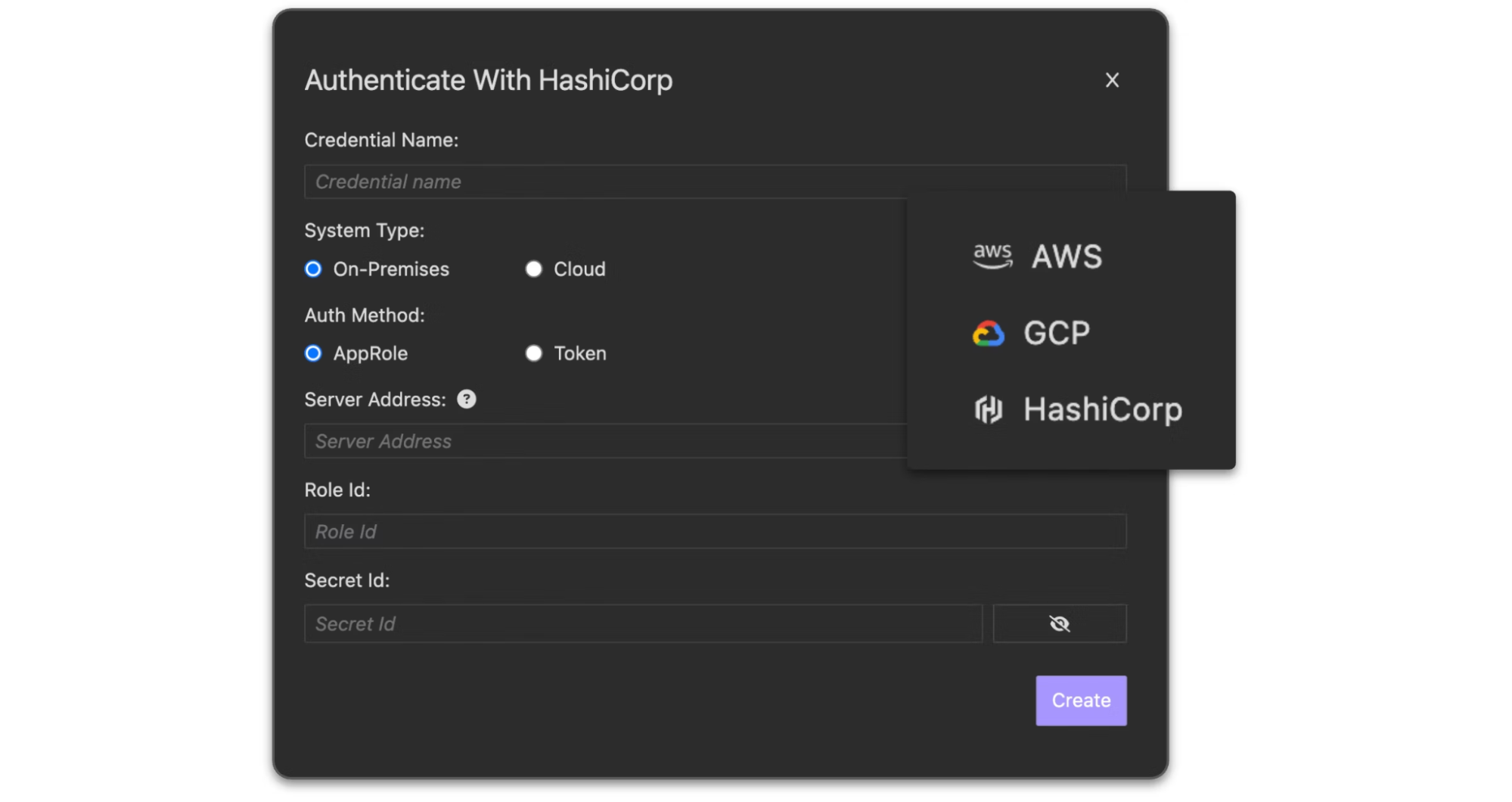
Integrate with your external vault of choice for streamlined secrets management.
Store data locally, via Git, or in the cloud
Data security and data locality go hand in hand. Many organizations, especially those operating in highly regulated industries, may prefer to not store their data in the cloud for security and compliance reasons.
Insomnia provides organizations with the flexibility to store their data where they want to: 100% locally, via Git, or in the cloud. We understand that flexibility is of the utmost importance to our users, and so we offer various storage options to cater to the data compliance needs of each individual organization.
In addition to having multiple storage options available, storage control in the Insomnia enterprise offering allows admins to mandate a specific storage location (cloud or local + Git) as the single source of truth for every user in the Insomnia project. This provides an extra layer of control to help drive compliance across every team and line of business using Insomnia.
This helps avoid proven risks associated with syncing with publicly available GitHub repos. As called out in the recent data leak coverage, there have been leaks when, “...collections and environment files are synced or exported and stored in public repositories like GitHub. If sensitive data isn’t masked or sanitized before these files are uploaded, it becomes accessible to anyone with access to the repository. This is a common vulnerability, as developers may inadvertently publish tokens or secrets without realizing the impact.”
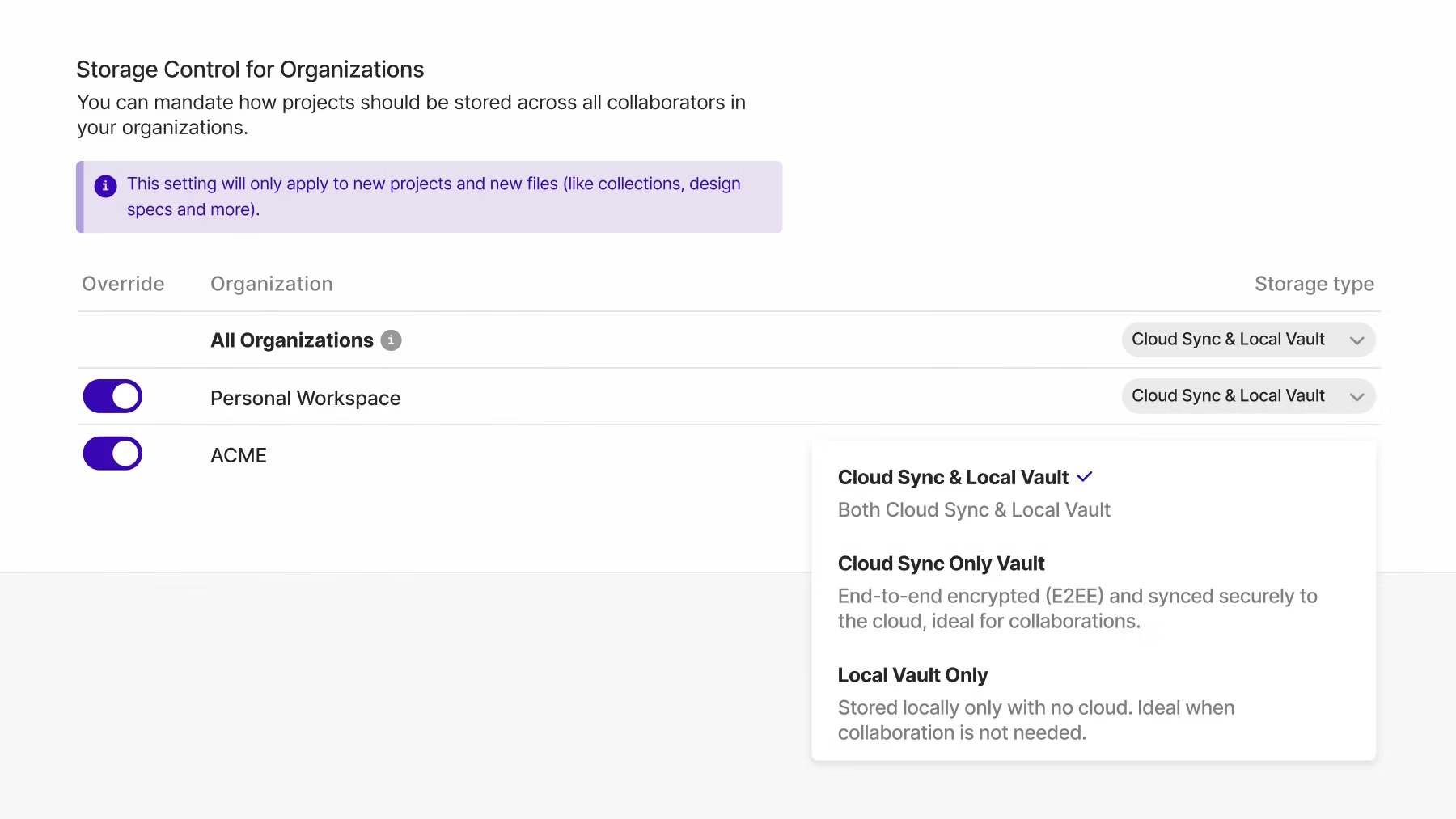
Have full control over where your Insomnia data is stored.
Opt-in to end-to-end encryption for the cloud
For those who choose to store their data in the cloud, with Insomnia you can opt-in to having your data encrypted end-to-end on the client side. This means that all encryption keys are generated locally, all encryption is performed before sending any data over the network, and all decryption is performed after receiving data from the network.
At no point in the sync process can the Insomnia servers, or an intruder, read or access your sensitive application project data.
Choose training and support from a team of API security experts
At the end of the day, a good product is truly only as effective as the quality of the team that backs it.
Insomnia is owned and operated by Kong, and when you choose Kong, you get access to the same world-class team that supports the most adopted, battle-tested, and secure API platform — backed by great documentation, 24/7 support, and industry-leading expertise to help you securely govern APIs from design to deprecation.
Get started today
See Insomnia in action here and reach out to our team to learn more.










