Our latest release of Kong Konnect augments the security and compliance of the offering through enhanced authentication capabilities.
Through the rest of this post, we’ll walk you through each of these features and explore what’s new in this Kong Konnect release.
Kong Konnect Personal Access Tokens
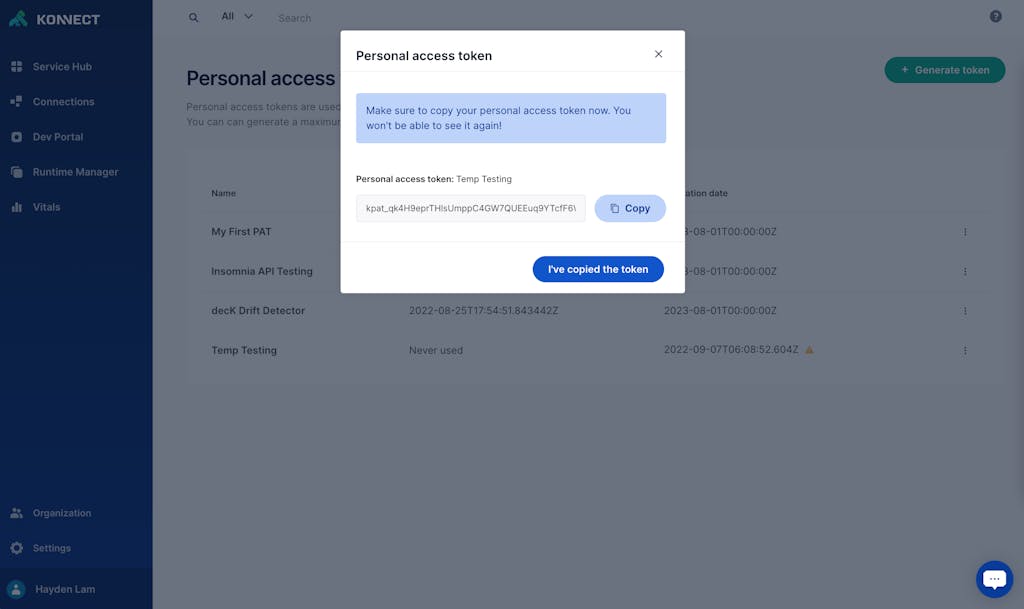
Figure 1: Kong Konnect Personal Access Tokens
The introduction of the Kong Konnect personal access token (PAT) allows users to generate an alternate set of credentials that can be used to authenticate decK for Kong Konnect.
As a result, organizations that have Single Sign-On enabled are able to utilize personal access tokens to bypass the need for usernames and passwords completely. PATs also serve as the preferred way to securely authenticate automated tooling and custom integrations.
Users are able to create, manage and revoke their PATs from the personal access token page. This menu can also be found by clicking on the user’s profile on the bottom left navigation.
- Access Control – PATs are tokens that belong to and represent the owner of the token. Therefore, the roles and permissions of the PAT are inherited from the roles granted to the user or via the user’s team membership.
- Token Expiration – PATs are long-lived tokens with a configurable expiration date of up to 12 months token lifetime.
- Token Rotation – Each Kong Konnect user is allowed up to 10 PATs. This allows the users to manage unique credentials for different use cases and rotate tokens as necessary.
PATs with decK for Kong Konnect
In the decK v1.14 and above, personal access tokens can be used to authenticate decK for Kong Konnect by passing the PAT in the </span><span style="font-weight: 400;">--konnect-token {PAT} flag.
Example:
The PAT can also be passed in via an environmental variable using the DECK_ prefix.
Example:
Federated Authentication with OpenID Connect
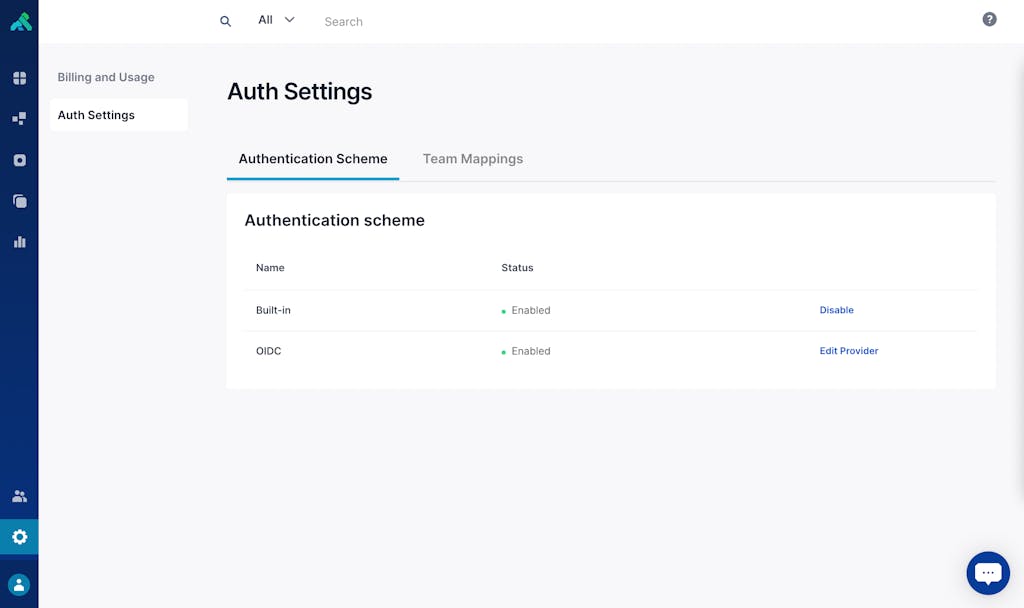
Figure 2: Auth Settings in Kong Konnect
During Kong Summit 2021, we announced the availability of Okta support in Kong Konnect for administrative Single-Sign-On (SSO) and for portal application registration. Today we are excited to announce that Kong Konnect supports integration with federated identity management supporting OpenID Connect (OIDC) standard. This means organizations can integrate Kong Konnect with several OIDC identity management providers (IdP) such as Okta, Keycloak, PingFederate, Azure Active Directory, Microsoft Active Directory and more.
Organizations have the option to toggle each authentication scheme independently, which allows three states to exist: Built-in auth only, SSO only or both enabled. This allows greater integration with existing IT infrastructure as well as support for service accounts should the need arise.
If SSO is enabled with an OIDC provider, the Team Mappings option allows users who belong to an IdP group to be automatically mapped to a Konnect Team via their group claims. Users who log in to Kong Konnect with a verified group claim will have their team memberships replaced with that configured in the Team Mappings tab.
Combined, the OIDC-SSO and the Team Mappings allow additional users to be automatically provisioned in Kong Konnect and their access automatically granted once the integration with the IdP is configured.
Start your journey with Kong Konnect today
To learn more about Kong Konnect refer to our documentation here and schedule a personalized demo today. Kong Konnect is also is available for a 30-day free trial. We look forward to your feedback on these latest features of Kong Konnect.
To get an immersive experience of our products, including the latest news and announcements in Kong Konnect, join us for Kong Summit. Check out Kong Summit 2022 schedules, speaker list, and registration info.