Today we’re excited to announce the release of Kong Mesh and Kuma 2.0. With this new major release, we’re announcing the first availability of our next-generation policies, in addition to new eBPF capabilities.
2.0 is also significant as we have unified the version scheme between Kong Mesh and Kuma. Previously, Kuma versions had an n-1 version naming convention when compared with Kong Mesh. This was mainly for legacy reasons, so we're happy to unify the versions and eliminate a minor source of confusion for customers and the community.
In order to take advantage of the latest and greatest in service mesh, we strongly suggest upgrading to Kong Mesh 2.0. Upgrading is easy through kumactl or Helm and doesn't require any special steps (despite being a major release).
Notable features:
- Added support for eBPF into both our CNI and init container configurations. Using eBPF can improve the performance of traffic flow latency by up to 12%.
- Added the first 3 next-generation policy updates:
- MeshTrafficPermission
- MeshTrafficLog
- MeshTrafficTrace
- Workloads on AWS ECS can now use IAM service identity to obtain Mesh bootstrap tokens.
- Multiple improvements to the UI as part of an ongoing effort to simplify and enrich the functionality of our admin dashboard. Specifically in 2.0 we're releasing:
- New YAML / JSON search and syntax highlighting for policies and Envoy configuration dumps
- Filtering and column customization capabilities for Data Plane Proxies
- Simplified, more intuitive navigation structure
- We have added the ability to configure auditing for all RBAC (Role-Based Access Control) and policy actions.
- Improved our Datadog integration to record ingress and egress requests as separate services, allowing for easier debugging.
- It is now possible to configure the specific TLS versions and ciphers that are supported by the control-plane / API server.
- Users are now able to configure multiple UIDs to be ignored by traffic redirection (useful to workaround some issues with systemd-resolver).
- Increased logging capabilities when using iptables for traffic redirection.
For more details, reference the Kong Mesh Changelog.
eBPF Support
eBPF is a technology gaining a lot of traction and popularity, especially in the cloud native world. We see many potential applications of eBPF for traffic flow, performance, and monitoring use cases. With this 2.0 release of Kong Mesh and Kuma, we’ve focused on some performance improvements and added the ability to replace iptables with eBPF for traffic redirection within the mesh.
We’re utilizing the Merbridge OSS project within our eBPF capabilities and are very excited that we’ve been able to contribute back to that library and become co-maintainers. We look forward to working more with the Merbridge team as we continue to explore different areas to include eBPF functionality in Kong Mesh and Kuma.
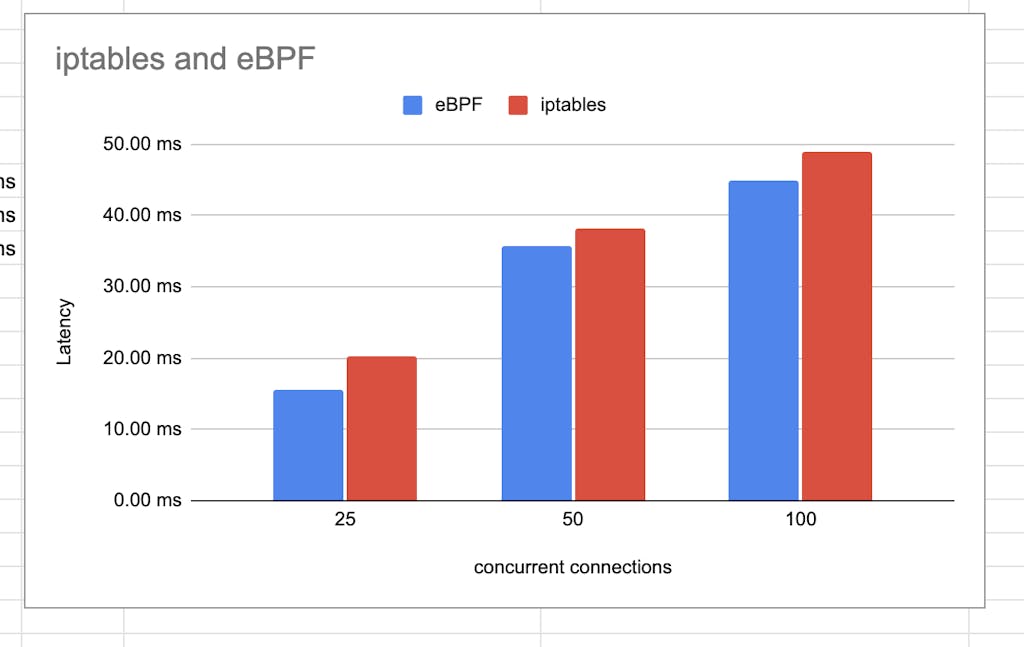
Figure 1: iptables vs eBPF latency comparison
Next Generation (2.0) Policies
In the last year or so, we’ve seen customer and user environments grow more complex, and teams leaning into self-service models with platform-defined sensible defaults.
To help with these use cases, we've begun re-designing the ‘next generation' of policies in Kong Mesh and Kuma. Some of these new policies will feature additional configuration options that don't exist today, and all of them will feature a new selector mechanism that makes it easy for multiple teams to apply policy at different levels of granularity with an application environment.
As shown in the sample below, the new selectors use a targetRef system (inspired by GatewayAPI) to select which meshes, services, data plane proxies, etc. are targeted by specific policies. Multiple rules can be specified in the same policy (as supported today) or many different policies can be created targeting different subsets. Our new policy system will merge these all together with the correct precedence rules before calculating and pushing the configuration out to the Envoy dataplane.
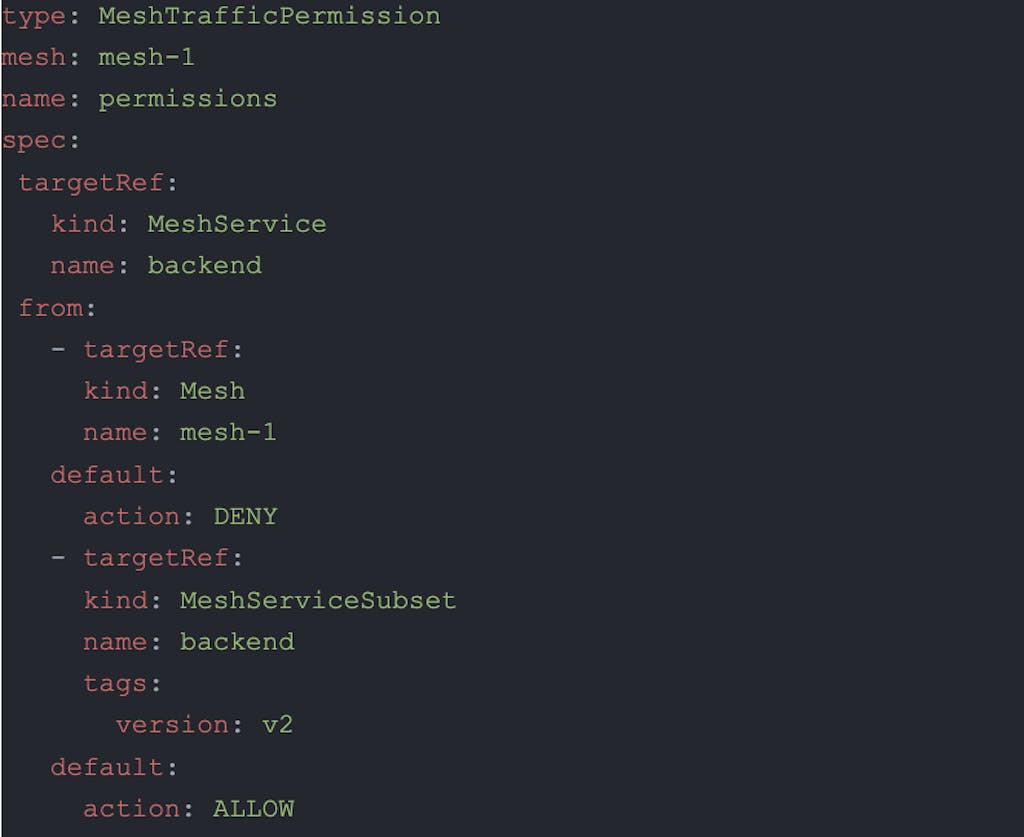
Figure 2 : Example of a next-gen MeshTrafficPermission policy
We’re going to be releasing new versions of all mesh policies over the coming few releases, and in 2.0 we’re pleased to announce that the following next-gen policies are implemented:
- MeshTrafficPermission
- MeshTrafficLog
- MeshTrafficTrace
Head over to the docs to check out how to use the new policies and selectors.
RBAC Audit
We released the ability to configure Role Based Access Control (RBAC) several versions ago, and in 2.0 we're continuing to enhance that feature by adding the ability to audit log any actions (policy updates, RBAC changes, etc.) that happen in Kong Mesh.
RBAC audit logging can be configured to send logs to a different sink to your regular application logs, ensuring the ability to keep these more security-focused events separated from standard output logs. We also emit these logs in a structured JSON format, allowing for easy indexing and search in your logging backend of choice.

Figure 3: Sample RBAC audit log entry
UI Improvements
In 2.0, we’re releasing the first stage of our complete UI renovation project. In today's version, you’ll see that the UI navigation has been simplified and made more intuitive to explore.
We’ve also revamped the service and data plane proxy list views, adding field filtering and customization capabilities. Additionally, after clicking a data plane proxy, you'll now be able to view a fully formatted and searchable Envoy configuration for better troubleshooting and visibility.
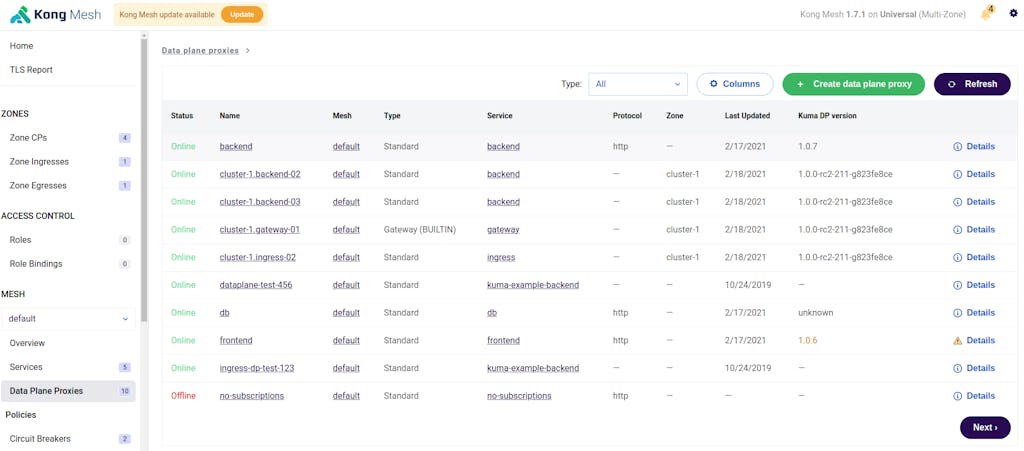
Figure 4 : New UI DPP view with filtering and column customization
We're excited about how the UI is looking and many more UI improvements are coming in the next few releases so stay tuned!
Get in touch to learn more about Kong Mesh and how to build an enterprise service mesh. You can also download Kong Mesh and get started for free.












