What Are Virtual Machines (VMs)?

What are Virtual Machines (VMs)? A virtual machine (VM) is a fully-fledged, standalone operating environment running on a physical computer. Unlike the host computer it's running on, a VM is not a physical machine, thus the designation of "virtual".
An Introduction to Hybrid and Multi-Cloud Connectivity

As the cloud industry matures, its no longer a question of if youre in the cloud, but how many clouds youre in. Most businesses now realize that there isnt a one cloud fits all solution and have shifted towards a hybrid or multi-cloud model. Hybrid
10 Ways Microservices Create New Security Challenges

Why are Microservices Security Risks?
Traditional security was simple. One perimeter. Few entry points. Clear boundaries.
Microservices shattered this model. Now organizations manage hundreds of independent services. The average number of API calls
Kong Mesh 2.11: Reduced Privileges, Improved Support for AWS ECS

We’re at it again, bringing more incremental improvements to Kong Mesh! Built on top of Kuma, Kong Mesh brings much-needed simplicity and production-grade tooling. Kong Mesh is built for smooth operations with platform teams in mind, providing secu
Mesh to the Rescue of API Gateways for Cross-Cloud Connectivity

Many organizations struggle with managing API gateways across multiple cloud environments. In this blog post, we'll explore how Kong Mesh can solve these challenges and enable seamless cross-cloud connectivity. The challenge of multi-cloud API gatew
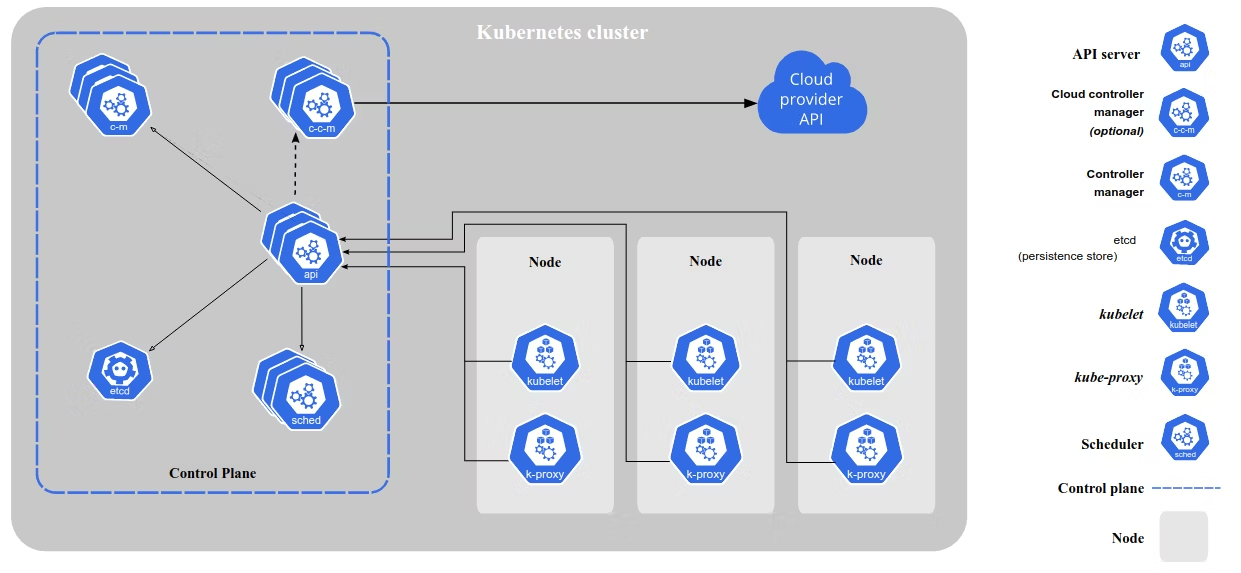
Using Service Mesh Within Your Kubernetes Environment

Container technologies are always evolving — and we're not talking Tupperware here. Over the past years, service mesh has emerged as a crucial component for managing complex, distributed systems. As organizations increasingly adopt Kubernetes fo
Staying Agile on VMs and Kubernetes With Service Mesh
Over the past ten years, Clubhouse and other innovative startups built software quickly. They started from scratch and blew past their incumbents. But the fact of the matter is that speed is no longer a differentiator. Everyone can move quickly. W