Attacks estimated to surge 996% by 2030 — with the cost per breach rising to $14.5 million
APIs have revolutionized every industry. They fuel digital transformation and power the web, making up more than 83% of global internet traffic. And API adoption will only grow, with AI, Web3, and decentralization only further driving API usage and integration.
But these sometimes-overlooked enablers of connectivity and communication present a serious security challenge: APIs are increasingly in the crosshairs of cyber-attackers.
In this post, we'll look at the rising number (and cost) of API-related security incidents, and why APIs should be considered mission-critical infrastructure.
APIs are a leading attack vector
Gartner previously predicted that APIs were becoming the leading attack vector for web applications. And the headlines tell a similar story — with API-led cyberattacks leading to data breaches, customer data leaks, and lawsuits around the world.
- In Australia, the Optus breach impacted 40% of the country's populace and sparked government scrutiny of data security and management practices. Two weeks later, Telstra Health fell victim to an API-related hack.
- In the U.S., cyberattacks disrupted the critical infrastructure of one of the largest oil pipelines, leading the White House to release an executive order mandating zero-trust security for organizations with significant national security relevance.
The rise of API attacks
In the Kong eBook Leading Digital Transformation: Best Practices for Becoming a Secure API-First Company, we worked with Kong data analysts and outside economists to develop research to get a better look at the risk around poorly managed APIs in the coming years.
Some highlights of the research are below.
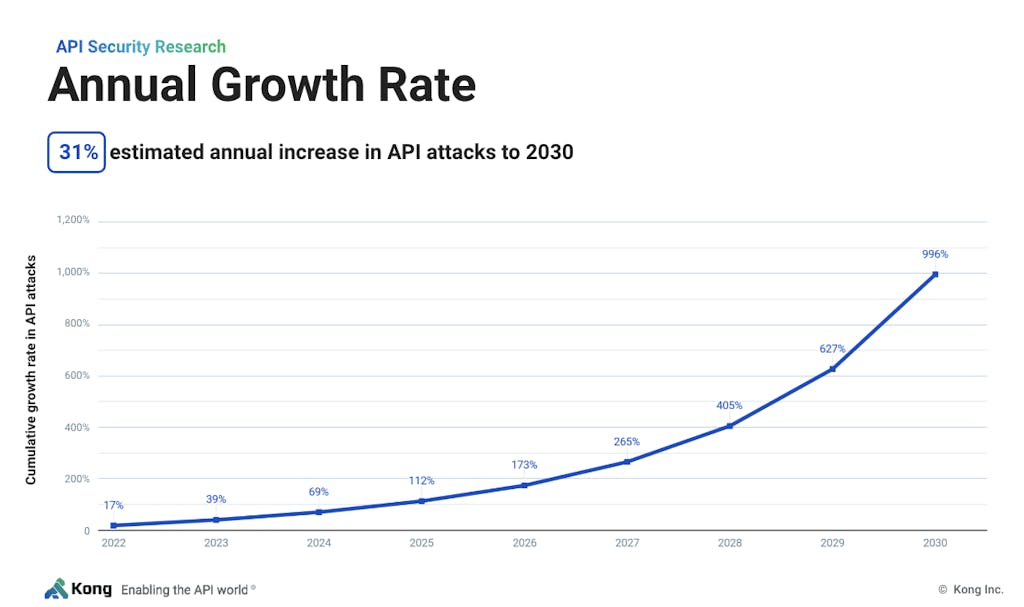
A surge of API attacks is predicted over the next decade
Between 2021 and 2030, we project a surge of 996% in API attacks. This signifies an explosion in the frequency and severity of API-related cyber threats. An average annual increase of 31% in API attacks over this decade is projected.
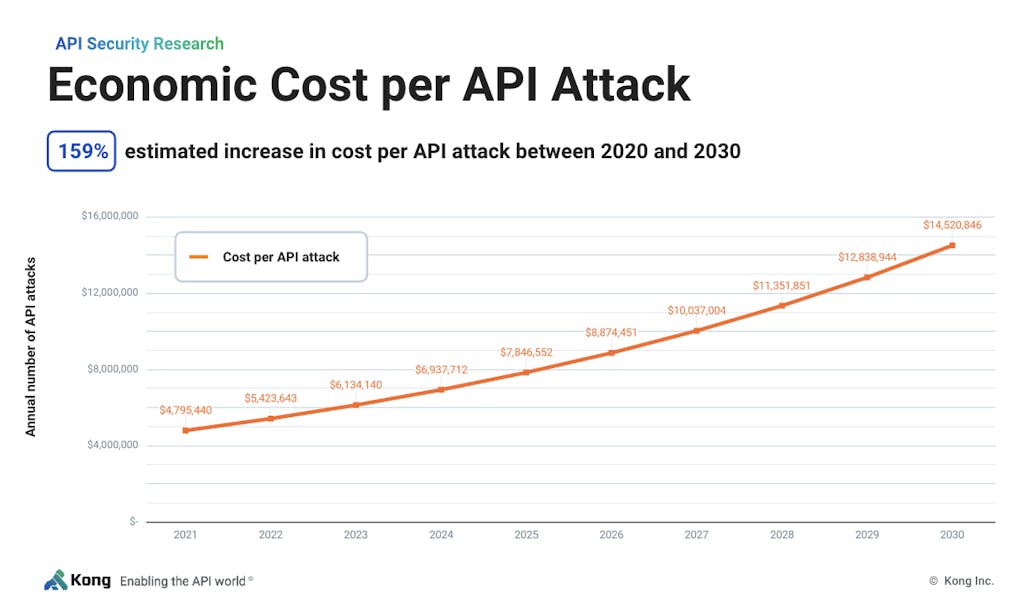
The cost of breaches to increase 95% by 2030
Not only will we see more API attacks, but we will see the cost of these attacks continue to grow as well. Today, the average cost for a security breach stands at $6.1 million, which accounts for remediation and lost value associated with damage to reputation.
Estimates in our study show that these costs are on an upward trend, and are predicted to increase 95% higher — to $14.5 million per breach — by 2030.
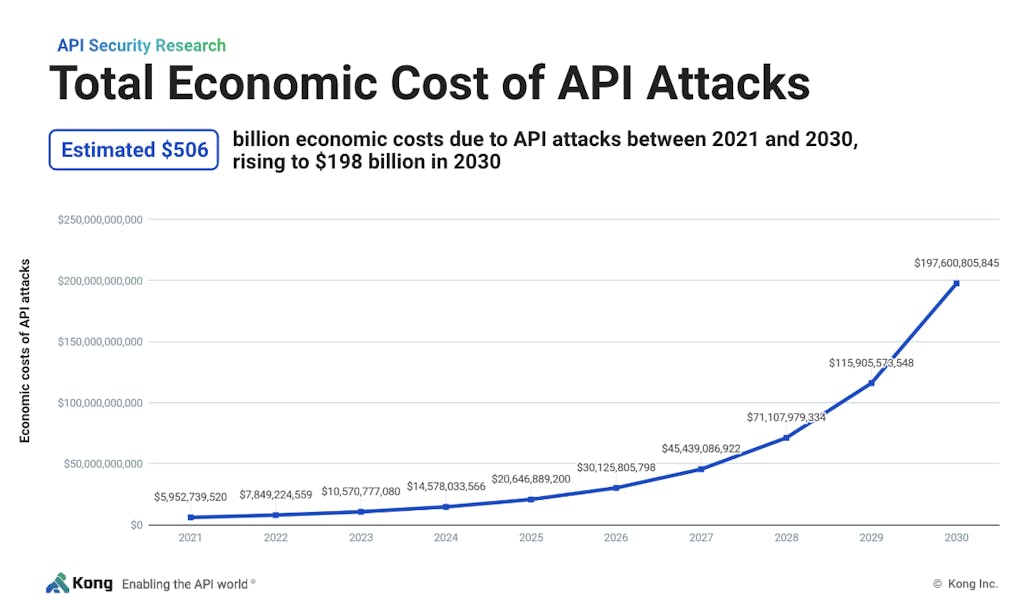
U.S. attacks to cost $506 billion this decade
In the United States alone, the economic cost of attacks is currently $10.6 billion per year. Our research projects the national cost to reach $198 billion within seven years, amounting to a cumulative cost of $506 billion this decade.
Are APIs really mission critical infrastructure?
So, are APIs really mission critical infrastructure?
Consider this: APIs are at the heart of everything an organization does and essential to every modern user experience — from user interfaces that delight customers to global partner networks that expand markets and drive revenue.
With this in mind, there's no doubt that APIs constitute mission critical infrastructure.
But even when APIs are recognized as mission critical, their infrastructure is often not accorded the same importance. This can lead to situations where attackers can identify and exploit discrepancies in API management and security, gaining system access and inflicting damage on enterprises and their customers.
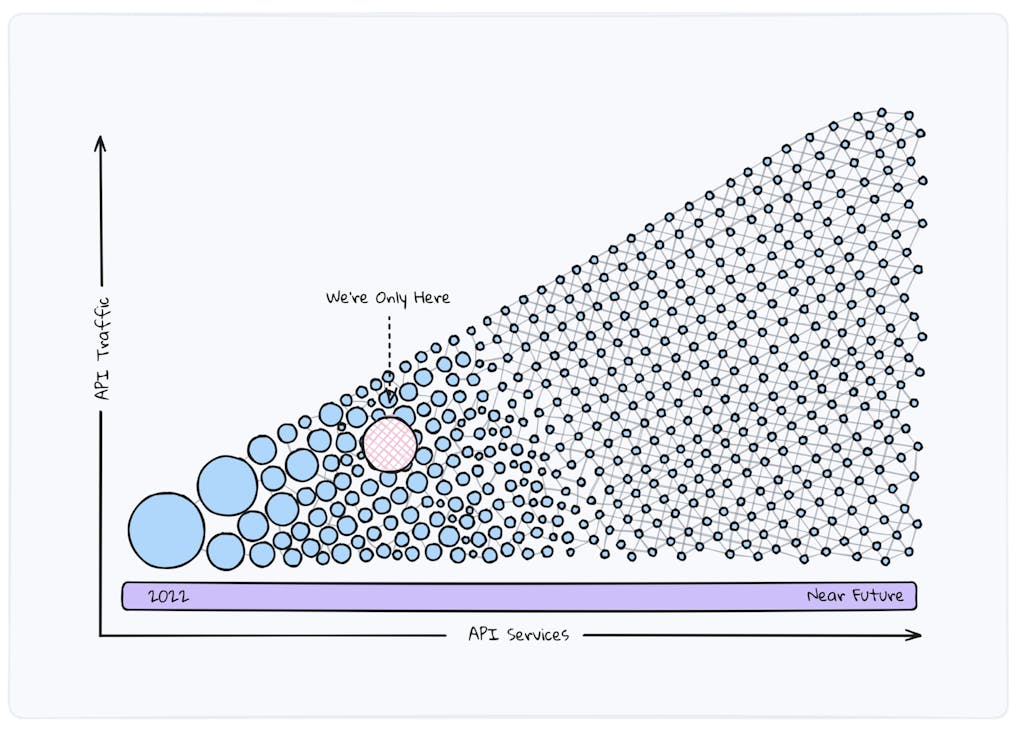
Technology leaders are expecting to build more APIs in the next five years, than all the APIs built until now. Are we prepared to manage this scale?
This inconsistency often stems from a well-intentioned but problematic decision: distributing API infrastructure ownership across multiple teams.
This approach aims to promote speed and autonomy, but it unintentionally triggers a chain reaction of adverse issues affecting internal systems and controls.
In practice, we can enable teams to move fast and take ownership of operational policies applied to the underlying API infrastructure without disseminating core infrastructure ownership. The ideal objective? To have teams act as "users" of API infrastructure — not "builders."
This becomes even more crucial when the organization is a national security asset — such as financial institutions or telecommunication companies — when API infrastructure should comply with the same rigorous standards and regulatory mandates as other corporate and operating functions. Regrettably, this compliance often falls short when infrastructure ownership is spread across teams.
How to build robust, reliable API infrastructure
Building a robust and reliable API infrastructure requires the establishment of an internal playbook that enables us to:
- Adopt consistent API controls across teams: Develop unified, robust, and secure API infrastructure that minimizes inconsistencies in API policy creation and enforcement.
- Enforce API security by default: Ensure security controls are in place across all teams and workflows, clarifying the organization-wide responsibility for API infrastructure.
- Foster speed and self-service: Encourage teams to innovate within an agile, self-service environment without compromising on consistency, security, or corporate responsibility.
- Promote accountability and responsibility: Cultivate a culture of API accountability, mirroring the responsibility inherent in other organizational areas. There must always be clear ownership of API infrastructure, with accountability upheld consistently.
The ultimate goal? To maintain continuous control over the API infrastructure that drives our organization’s present and future. This can be achieved responsibly, ensuring that teams remain productive and agile. But without the right practices in place, an organization’s ability to scale and expand its API portfolio is reduced — potentially exacerbating problems over time.
For a deep dive into each of these areas and a walkthrough of how to build a framework for establishing modern API practices within your organization, download the Kong eBook Leading Digital Transformation: Best Practices for Becoming a Secure API-First Company.
Conclusion
Most organizations today grasp the importance of APIs, but too few fully recognize that APIs absolutely constitute mission critical infrastructure that demands the appropriate management. As seen with recent API cyberattacks, insufficiently secured and managed APIs can result in severe damage to an organizations reputation and harm to customers.