Security Challenges in the Microservices Architecture
The demand for digital transformation has accelerated, with 62% of technology leaders sharing that they fear they are at risk of being displaced by competitors who innovate more quickly.  Enterprises are increasingly transitioning from monolithic to microservices architecture, with the goal to accelerate application development, speed up innovation and reduce time to market.
Enterprises are increasingly transitioning from monolithic to microservices architecture, with the goal to accelerate application development, speed up innovation and reduce time to market.
While a microservices architecture offers numerous advantages, it also introduces a unique set of security challenges. When we asked technology leaders about the main challenges they expect to face or have already faced when deploying microservices, security issues came out on top. The reason for this: complexity resulting from managing security for dozens, sometimes hundreds, of distributed components per application that are all communicating via APIs. It's no surprise these gaps in API security represent such a significant threat.
The traditional one-size-fits-all security approach falls short since each service may have its own security requirement based on its functionality. For example, in an application, you may need to expose only some microservices to external clients and not all of them. Writing custom code to secure each of these services is not a scalable security strategy. API and service connectivity and security now become critical as the backbone of your modern applications. Enterprises need to ensure their applications are consumable and reliable while also being secure and observable.
Kong Konnect, the only end-to-end service connectivity platform, provides universal service connectivity and management and empowers application teams to provide consistent security, comprehensive visibility and data protection across APIs and services.
Kong Provides Defense in Depth
As an overview, Kong Konnect provides multiple layers of defense against attacks, executed through its connectivity runtimes and functionality modules. The platform offers connectivity and security at the edge as well as within the application's services. We'll cover these aspects of the platform in detail in the sections below.
In the real world, your microservices need to interact with one or more external clients such as a web server, application or an IOT device. This direct client-to-microservice communication means exposing the APIs for each microservice. The Kong API gateway sits at the edge of your application and offers several security and connectivity benefits. The Kong Gateway:
- Provides a central platform for implementing security best practices, applying them consistently and efficiently to all your APIs
- Simplifies access to the application for external clients
- Restricts the consumers of your application from directly interacting with your underlying services
When it comes to connectivity and security within the application's services, you can leverage one of the Konnect runtimes - Kong Mesh. With Kong Mesh, enterprises can accelerate initiatives like zero-trust and GDPR with native mesh policies, improving the speed and efficiency of every application team.

Out-of-the-Box Security Plugins
Kong Konnect provides some powerful authentication and security plugins that integrate seamlessly with your deployments.
For example, Yahoo! Japan, relies on Kong Konnect to secure their 15,000 services with plugins that centralize the authentication and authorization functionalities. Some of those key out of the box plugins are:
- Open ID connect: allows you to verify the identity of your end-users without taking on the responsibility of storing and managing passwords
- Mutual TLS (mTLS) authentication: allows you to ensure that traffic is secure and trusted in both directions between a client and server
- IP restriction and Bot detection: you can easily restrict access to bad actors by whitelisting or blacklisting IP addresses and keep your application free operating and immune from DoS or DDoS attacks
At Kong, we are committed to information security frameworks and have achieved certifications and attestations of compliance against international and domestic standards such as SOC 2, Type 2.
The Kong Konnect platform enables security by design - it offers security features such as role-based access control (RBAC) policies, audit logs, encryption policies and more. The diagram below describes how data flows in a typical Konnect deployment.
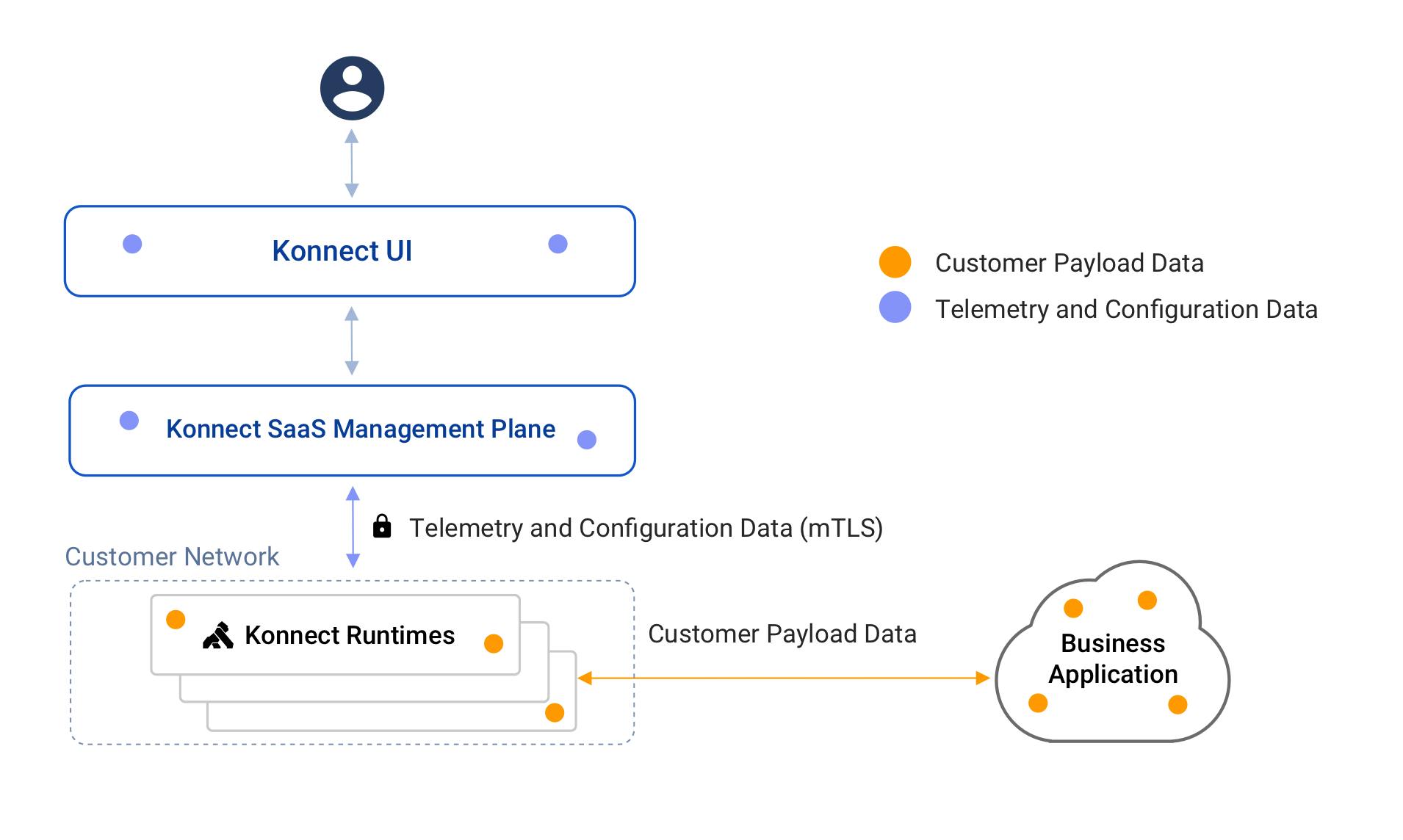
Figure 1: Konnect Data Flow Diagram
The Konnect SaaS management plane only collects the telemetry and configuration data required to manage and monitor the runtimes. Encryption is one of the key means to keep your data secure. The Konnect platform provides encryption using mTLS to ensure the data is safe during transit. The customer payload data remains within the customer network and is never accessed by the Konnect SaaS management plane. Additionally, enterprises can configure RBAC policies to secure access to the Konnect platform.
Embark on Your Journey Towards Secure Microservices
The benefits of transitioning to microservices are immense; however, it needs to be done without compromising on your security posture. Kong enables enterprises to confidently embark on their journey towards secure microservices. With its powerful platform, state-of-the-art runtimes, out-of-the-box security plugins, adaptive monitoring and compliance features, Kong empowers you to intelligently segment your network and ensures that your services have multiple layers of security.
All aboard!