When speaking with our customers, and particularly with platform teams, we repeatedly hear about how difficult it is to discover and govern all the services and APIs that actively run on their infrastructure.
In ever-expanding and changing environments, platform teams often grapple with the challenge of monitoring and managing the creation and termination of services across numerous disparate application teams. This lack of visibility can lead to inefficiencies and potential conflicts as the scale of operations increases. Additionally, staffing churn makes it hard to keep up with which services exist and who their corresponding owners are. This challenge is generally referred to as API sprawl and stems from a lack of centralized API oversight across teams and business units.
Organizations that aren’t able to keep an ongoing track of what APIs and services exist inevitably have shadow APIs, undiscovered and unmanaged APIs. These APIs may have been developed with good intent, and by skirting organizational governance and controls, they may have had perceived value as a quick solution. Yet left unchecked, they introduce a range of risks and inefficiencies.
What are the risks associated with shadow APIs?
Shadow APIs often bypass standard security reviews and protocols and may expose sensitive data or create unnecessary vulnerabilities in the service. Even though they may be known by a development group or line of business, these APIs may not undergo continuous security testing, data compliance controls, or patching, increasing threat vectors such as data breaches or unauthorized access.
Kong forecasts the number of annual API attacks will grow 548% by 2030. This means every single API endpoint running in your infrastructure is an opportunity for attack by bad actors.
Security aside, the presence of shadow APIs can still pose serious compliance and operational risks. These APIs were most likely not built following organizational standards and introduce inconsistencies in data handling, compliance, and alignment with regulatory requirements. Lack of controls may result in non-compliant practices, which can open up organizations to legal ramifications that may include fines and costly remediation.
These security and compliance risks are on top of the inefficiencies created in collaboration barriers when assets are unknown to organizations, resource waste in the creation of redundancies in functionality, and add maintenance burdens of service that are more likely to become abandoned over time.
That said, maintaining an up-to-date inventory of live services and all their various dimensions typically requires a significant amount of manual work from platform teams.
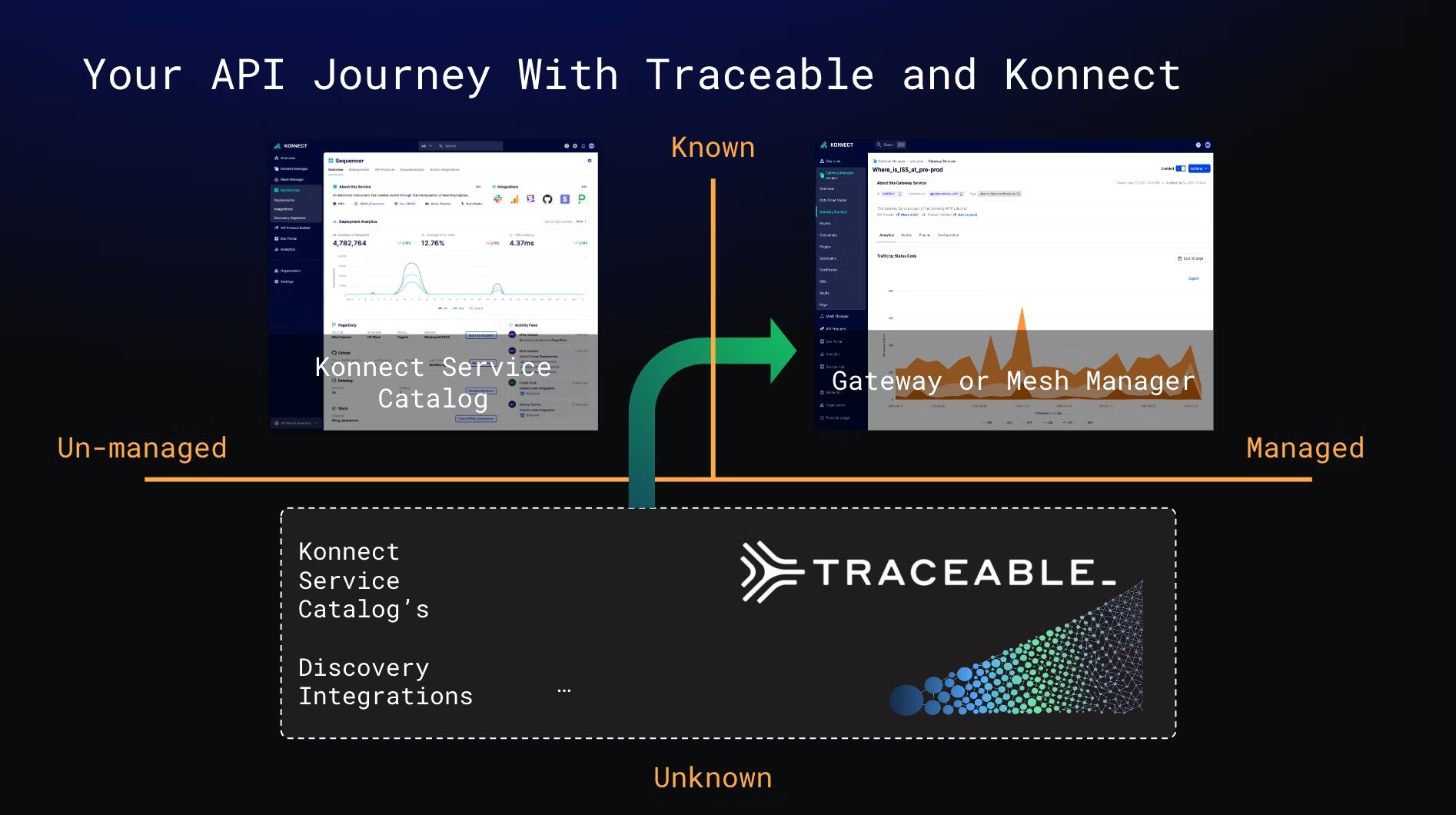
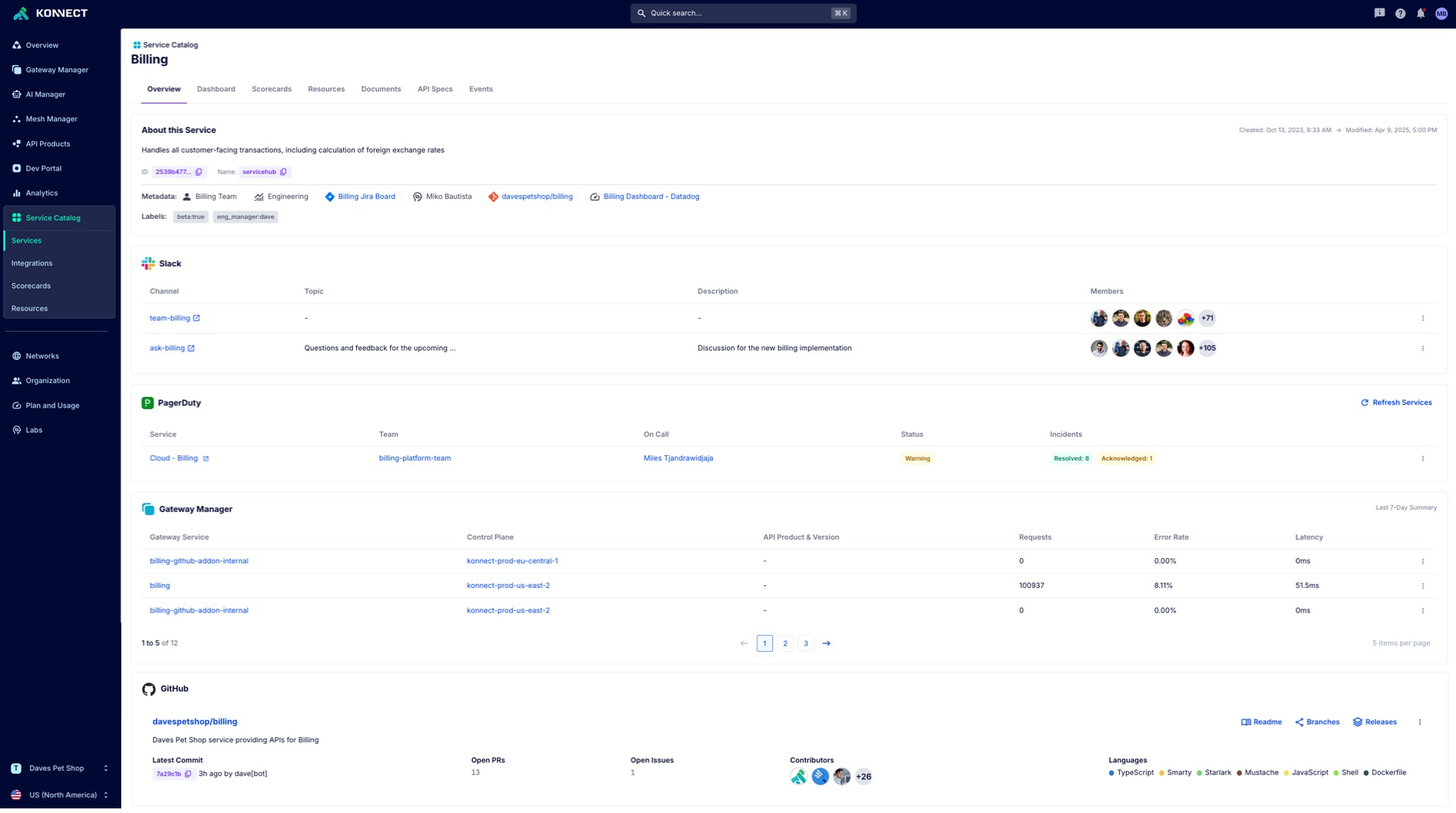
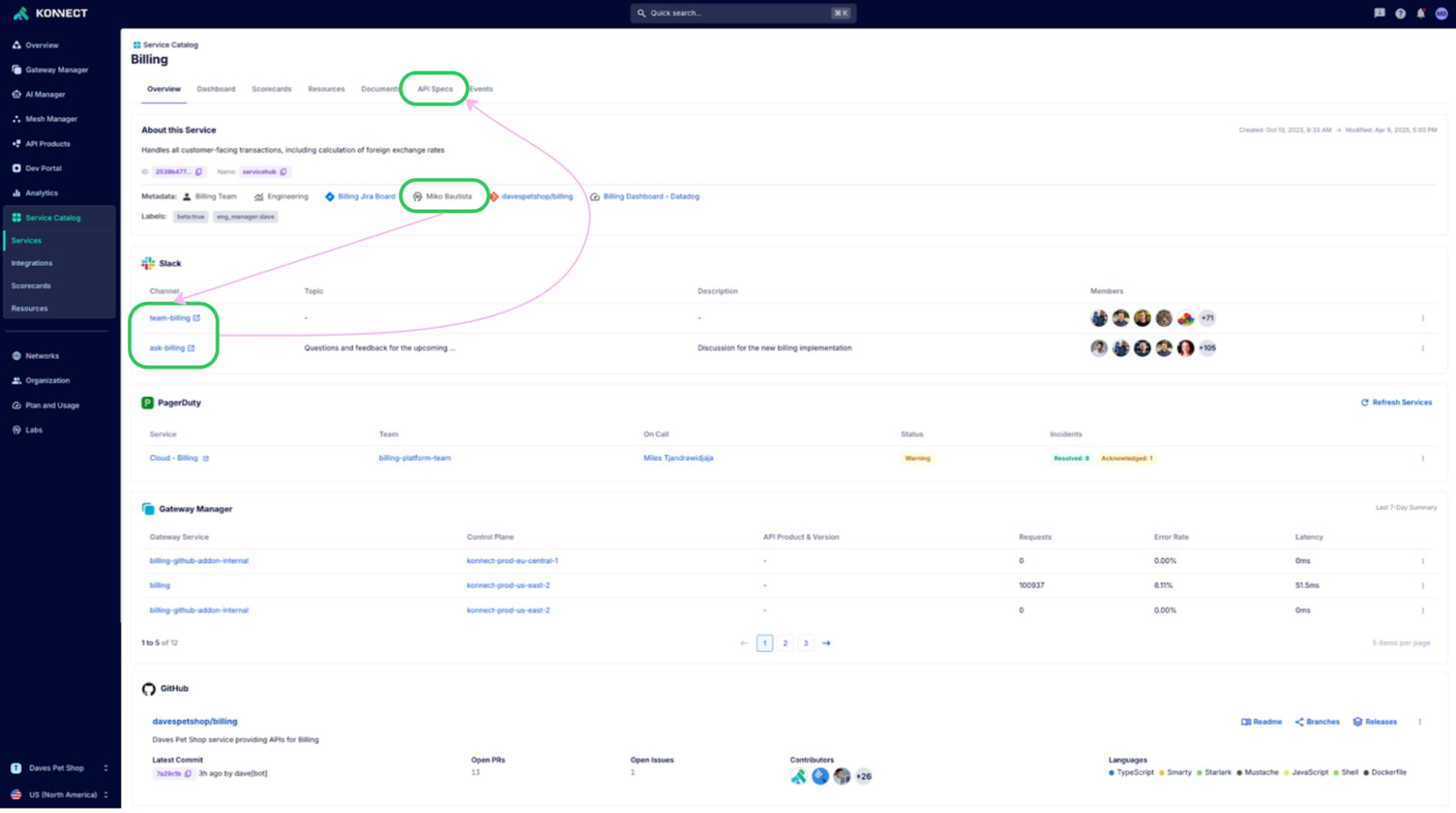
With Kong Konnect Service Catalog, you can automatically discover running services and APIs through infrastructural integrations and auto-populate the catalog as services, APIs, and other critical data get discovered and updated in real-time.