Build and operate APIs with quality and security using the combined capabilities of Kong and Traceable
Cloud native application development relies heavily on APIs. APIs have proven themselves as a scalable and efficient way to capture, deploy, and scale functionality. Consequently, APIs became a target for malicious actors to misuse. Therefore, building quality APIs with adequate security controls is essential.
Kong is the world’s most popular API gateway. Kong Konnect is a unified API platform. Traceable is a recognized leader in API security, providing a comprehensive API security platform in a cloud-first, API-driven world. The combination of Kong and Traceable capabilities will help play a role in building and running good quality APIs.
Good quality APIs
What may we consider to be a good quality API? The following table offers a potential API scorecard.

Good quality APIs are produced via an adequate API lifecycle.
Where to start?
Chances are good that most organizations already have plenty of APIs. In fact, there may be too many APIs of various quality and health states that are operational than the organization actually knows about. This is a problem — an API sprawl problem.
Ideally, organizations should be able to answer the following questions:
- How many APIs do we have?
- Where are these APIs?
- What is the quality of these APIs?
Once these questions are answered, a matrix emerges, it can look like this:

All APIs should be known and managed, as seen in the top left quadrant. However, not all organizations will have their APIs in this category. The term "managed" should not be up for subjective interpretation, it should be understood to mean "of good quality, secure, reliable, and constantly monitored and refined."
On the other end of the matrix on the bottom right are zombie APIs. These are APIs that are alive, but not actively maintained by any team, and are likely outdated and unmanaged, but somehow still running. These are a risk.
Unknown and Managed APIs, at the bottom left quadrant, are peculiar in that they have some level of management, a team perhaps looks after them, but they are not "official" as such. These are "rogue" APIs. They are another risk.
The top right quadrant has APIs in transition. This is a backlog that is prioritized in order to move APIs into the known and managed quadrant.
So what does it take to answer the questions listed above, and to take action once we know the answers? This is what the combination of Kong and Traceable are for.
API security aspects
If we were to treat APIs as assets, and by extension the functions and data they work with, then we quickly realize they must be protected against threats. Fortunately, there are basic aspects of security that we can, at minimum, ensure our APIs meet.
The How an API Gateway Secures APIs article does a good job of explaining this, and shows common protections that can be applied. Furthermore, readers familiar with the OWASP API Security Top 10, may view this presentation.
The role Kong plays
Kong, as an API gateway, is referenced in the aforementioned resources. The classic use case for an API gateway is depicted in the following diagram.

Here we see Kong and the mechanism by which API Consumers are able to make requests. By ensuring that our services may only be accessed through Kong, we're able to enforce a layer of security for our APIs. Kong will integrate with our IDPs, will log our transactions, allow us to have observability via metrics, and ensure we have consistent access to APIs.
This does not only apply to classic REST APIs as we know them. All APIs, possibly using gRPC, WebSockets, GraphQL, working with messaging & streaming systems, as well as LLM traffic, as seen in this diagram are all fair game for Kong.
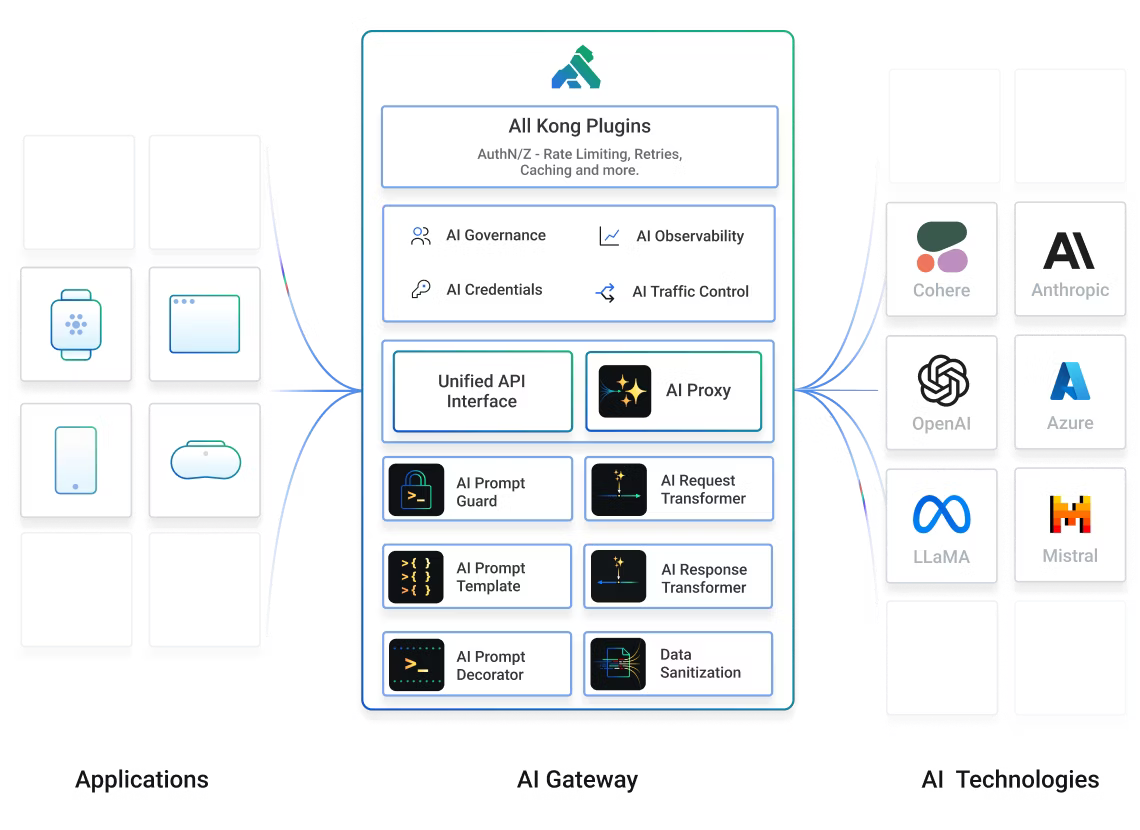
Kong Konnect takes this further by streamlining the deployment and configuration of multiple Kong instances across teams, and geographies. This diagram shows what a high-level deployment may look like:

With Konnect we are no longer doing just API management with an API Gateway. Konnect provides a developer portal, analytics, a service catalog, API product management, and mesh management, all in one platform with overlaid governance and APIOps. This is Unified API Lifecycle Management.
The role Traceable plays
Traceable is a security platform offering:
- API Discovery
- API Security Testing
- Threat detection
- Threat mitigation
Traceable is classified as a WAAP (Web Application and API Protection) solution. Traceable integrates with Kong both at the Gateway level, via the Traceable Plugin, as well as Konnect’s service catalog Traceable Integration.
Each of the capabilities Traceable offers complements Kong’s role well.
The Service Catalog integration permits API platform owners and operators to bring unmanaged API into compliance with Kong as their API Gateway. By importing such APIs into the catalog, they can be prioritized and implemented as Kong Services and Routes.
The Traceable Plugin further enhances Kong’s ability to offer dynamic security protections to APIs. This is possible as Traceable does sophisticated behavioral analytics to identify baseline traffic patterns, and therefore suspicious or unusual behavior across numerous consumers, API calls, and sessions.
API Discovery
Traceable’s platform through both agent and agentless approaches collects data from a variety of entities including, but not limited to:
- CI/CD pipelines such as Snyk, Github, Jenkins, and the like
- Web Application Firewalls, such as Cloudflare, F5 and the like
- Load Balancers: such as F5, HAProxy, Nginx and the like
The following diagram illustrates this further by highlighting instrumentation options via different approaches.

These integrations will help identify APIs, including zombie and rogue as well as known APIs, managed or not. This capability can therefore be a powerful tool to begin an API security audit.
The general architecture for this process is depicted in the following diagram.

The Tracing agent may run on any of the aforementioned integration points and makes the discovery data visible for action in the Traceable UI dashboard. The Tracing Agent does not have a direct connection to the Dashboard; it passes first through a Platform agent, which redacts any sensitive data. The Tracing Agent may further receive policies and rules which it may use to block, or allow requests, based on contextual traffic patterns and dynamic anomaly detections. Therefore the Tracing Agent plays a dual-purpose role.
It is sometimes a sobering meeting for stakeholders when the results of a Traceable scan are concluded, and the findings are shared, showing potentially serious, high-risk APIs with inadequate protections and unmitigated vulnerabilities.
API security testing (AST)
API security testing is an important part of an API lifecycle. Traceable’s platform offers AST capabilities to help identify vulnerabilities or weaknesses. The testing is based on the OWASP API Top 10, and informed by data traceable gleaned from traffic it observes. As such it supports a variety of security testing approaches. This nicely complements API quality testing via Insomnia, for example.
API Security and quality testing is an extensive topic on its own. In this article we will not go into further details, as we are largely concerned with the high level role that Kong and Traceable play.
Threat detection
The copious data that Traceable collects makes its way to an purpose-built API Security Data Lake where analytical and pattern detection algorithms are constantly on the lookout for anomalies. Once detected, and considered a threat, they are surfaced for administrators to take action. Administrators may also conduct their own querying to do further investigations.
Threat mitigation
In response to valid threats, security teams and administrators can take action, perhaps by altering traffic rules, enforcing policies in gateway, blocking IPs, or any other reasonable action to mitigate a threat.
We now visualize what a deployment may look like as it evolves to take advantage of the combined capabilities Kong Konnect and Traceable for API security.
We begin with a theoretical organization with the following evolving architecture.

The organization has two deployments. One is on-prem; the other is on AWS. Both deployments have a few APIs that the organization knows about, and they are exposing them both using an F5 load balancer for the on-prem deployment, and an ALB on the AWS deployment.
Use an API Gateway on AWS
The team managing APIs on AWS wants to reduce the cost of serving APIs while improving front-end latency, and to further standardize Authentication, Authorization, and Logging approaches. They use the Kong Gateway for this purpose and introduce some caching for frequently used APIs, along with some rate limiting. Along the way, the team integrates an Identity provider and begins collecting data for observability to get information about the frequency of API calls, their status codes, latency, and the users making the calls as well as some rudimentary details on the requests.

Use an API gateway on-prem
The project was a success, so the on-prem team decided to follow the same approach of using Kong. But they do not have, or need an IDP, as they rely on X.509 to authenticate and authorize consumers. Further, they do not have an on-prem observability stack.

Use Kong Konnect for both deployments
The on-prem team, similar to the API team working on AWS, experiences increased uptake for their APIs. Their work replicates the success of the AWS API team. The organization decides to standardize the management of the APIs through Kong Konnect, and formally produce API products, published to an API portal, and leverage the analytics to produce consolidated reports on APIs’ and applications’ health.

Use Konnect Service Catalog and Traceable API Discovery
Next, the team decides to begin populating all the relevant aspects of various APIs into Konnect’s service catalog. They realize that there is an integration with Traceable, which can discover APIs, and further highlight potential threats.

Bring standard API security with Kong Gateway via Konnect
Traceable’s API Discovery finds a handful of APIs are directly accessible both on-prem and on AWS. Some of these have minimal protections. After being added to the Service Catalog in Konnect, they were then moved to be managed by the Kong Gateway.

Add dynamic threat detection and mitigation with Traceable
The team was somewhat surprised by the finding that Traceable uncovered. They decided to further rely on Traceable’s plugin for Kong as an extra measure of dynamic protection.

Conclusion
The team is pleased with the progress they made. By using Kong Konnect, they brought a level of quality and governance to APIs, which then they were able to expand to all APIs in the realms they manage. From there, by using the Konnect Service Catalog, coupled with Traceable’s API Discovery and dynamic threat protection, the team feels more comfortable with the security of their APIs.
Yet, they understand their journey is far from over. The team plans to continue to invest in their API lifecycle, and will implement rigorous governance and regular security testing to ensure their APIs continue to run smoothly and securely.
Want to learn more about building and running secure APIs? Check out our upcoming webinar, Streamline and Secure API Management with Kong and Traceable.






















