Today, we’re excited to announce the release of Kong Gateway 2.8, which further simplifies API management and improves security for all services across any infrastructure. This announcement demonstrates Kong’s continued commitment to our customers and community by providing a next-generation service connectivity platform to intelligently broker information across modern architectures.
Both the open source and commercial editions of Kong Gateway version 2.8 are available now from your favorite distribution channels.
Secrets Management (Beta) EnterpriseOSS
First up in the Kong Gateway 2.8 release is a new feature set called secrets management, currently offered as a beta.
Before we get started, let's define what we mean by "secret." In this context, a secret is a sensitive piece of information required for proper gateway operations. Secrets may be part of the core gateway configuration, e.g., database connection information, or part of gateway configuration associated with APIs serviced by the gateway. Some of the most common types of secrets include:
- Privileged account credentials
- Passwords
- X.509 Certificates
- API keys
Move from "Secret Sprawl" to Centralization
With Kong's secrets management, customers can leverage their own centrally managed secret management infrastructure. This facilitates adherence to IT security policies and ensures sensitive information necessary for gateway operations is up-to-date and mastered by appropriate stakeholders.
Improve Overall Security Posture
With Kong's secrets management feature, operators and developers can now work independently when developing, testing and deploying APIs. As operators bring more infrastructure online (e.g., new databases) to support evolving application needs, sensitive information is first added to the centralized secret manager (e.g., HashiCorp Vault) according to IT Security governance requirements. These secrets are then referenced as variables in the Kong Gateway configurations, making the Kong deployment more portable and secure.
With secrets management configured, Kong Gateway data planes will request secrets from third-party secrets managers such as AWS Secrets Manager and Hashicorp Vault, and resolve the secret values on the data planes. By using a simple variable with an intuitive syntax, developers can reference secrets in declarative configs, OpenAPI specifications and CI/CD pipelines to dereference secret values ephemerally at runtime only where they are needed, i.e., Kong data planes.
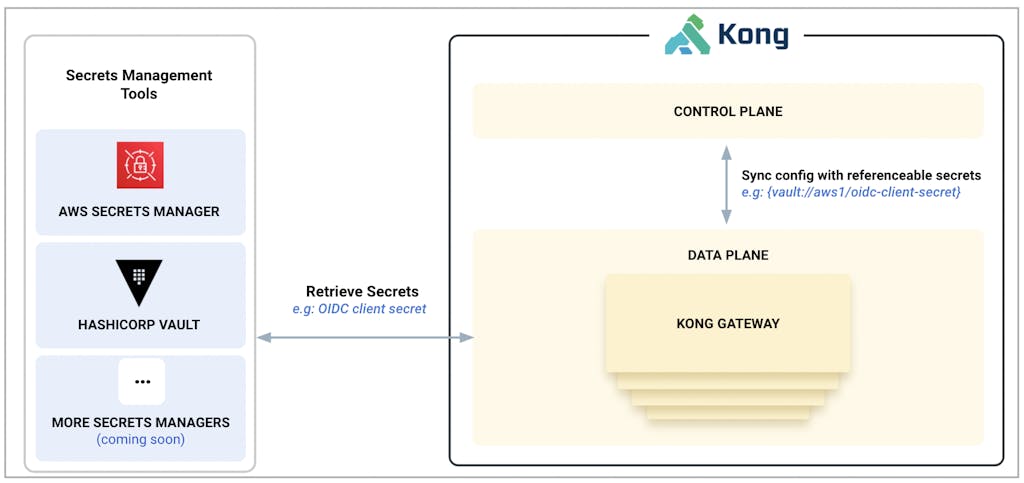
Diagram 1- Secrets Management Reference Architecture
With Kong's new secret management capabilities, mission-critical keys used throughout Kong's API management lifecycle and gateway deployments are centrally managed, auditable and kept safe from unauthorized use. This secrets management feature includes the following capabilities:
- Use pre-built "Connectors" to AWS Secrets Manager & Hashicorp Vault, and even use environment variables for accessing and storing secrets.
- Reference secrets using a simple and intuitive variable used throughout Kong configurations.
- Automatically resolve secrets on Kong data planes whose secret values only exist in memory and are obfuscated throughout the deployment.
Secrets management in Kong Gateway 2.8 is currently available as a public beta. Both AWS Secrets Manager and Hashicorp Vault integrations are available to Enterprise customers. For more information detailing the availability and functionality, check out the documentation here.
New Filtering/Sorting Feature in Kong Manager Enterprise
Kong Manager is the ideal user experience for API developers and operators to monitor and manage their Kong Gateway deployments. A more streamlined Kong Manager user experience means you spend more time solving your business challenges and less time managing Kong deployment architecture. All of the Kong Manager's features, including the new filtering/sorting capabilities described here, are available to Enterprise customers.
As the needs of your organization’s application development grow, so does the number of APIs. The new filtering and sorting feature improves the operator and developer experience in Kong Manager, making it incredibly easy to find exactly what you need as quickly as possible.
Kong Manager now includes a "Filter" tab for each of the gateway entities, including Services, Routes, Consumers, Plugins, Upstreams, etc. For every entity, you can find exactly what you are looking for by filtering the list of resources by name, whether they are enabled or disabled, protocol, host, path or Id. For example, you can now find Services quicker by filtering on the host of your upstream services.
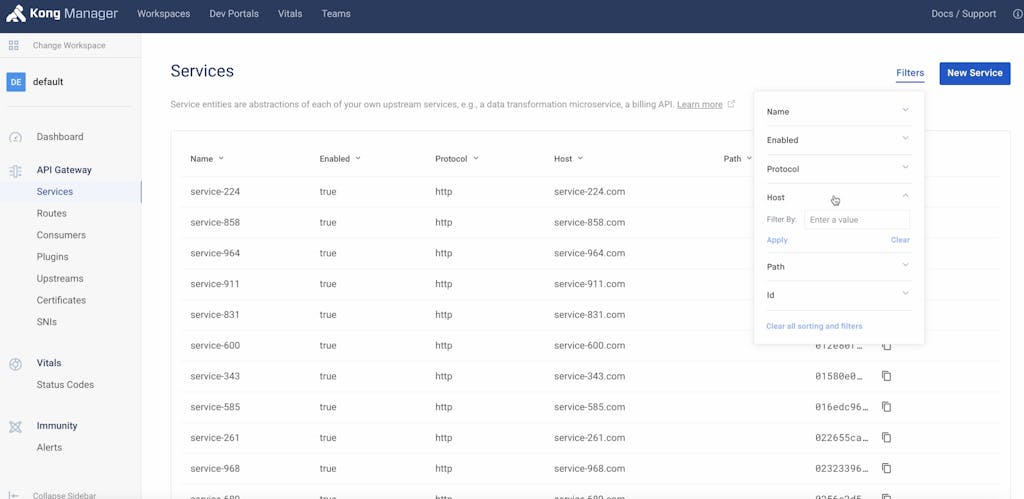
Diagram 2- Filtering by Host for Services
Mutual TLS for the Forward Proxy Advanced Plugin Enterprise
The Forward Proxy Advanced plugin allows Kong to connect to intermediary transparent HTTP proxies instead of directly to the upstream_url when proxying requests upstream. This is useful in environments where Kong sits in an organization's internal network, the upstream server is available via the public internet, and the organization proxies all outbound traffic through a forward proxy server.
In Kong Gateway 2.8, the Forward Proxy Advanced plugin now allows for Mutual Transport Layer Security (mTLS) authentication between the gateway and upstream server, which means the connection is strongly authenticated and thus more secure even when an HTTP proxy is between them. The Forward Proxy Advanced plugin facilitates mTLS authentication between these two parties, while the transparent HTTP proxy simply relays the communication. By using Kong Gateway and the Forward Proxy Plugin, you can ensure your APIs have secure methods of authentication across network topologies traversing the internet.
Additional Release Highlights
On the plugin front, we've added a few new features:
As a separate and notable release, decK received enhancements in v1.11, which improved the declarative configuration experience:
- First, decK now supports default values for core entities as well as plugins with the help of the Schemas endpoint. Overall, this will reduce the complexity when working with config files needed to manage the Kong Gateway.
Second, an `–online` flag has been added to the validate command which will perform validation against the Kong API without affecting the state of the Kong Gateway. Using the flag will help in catching configuration issues before attempting to setup your gateway via `deck sync`.
Get Started With Kong Gateway 2.8 Today
For a full list of features, fixes and updates, please see the available CHANGELOG for Kong Gateway here and Kong Gateway OSS here.
Get started with Kong Gateway 2.8 today - both the commercial and open source editions are available as a free download! If you have Kong Gateway installed already, upgrading to 2.8 is easy - check out our upgrade guide. Don't forget to let us know what you think on Kong Nation!
Stay tuned for our upcoming blog post, where we will discuss more on Kong Gateway 2.8 secrets management capabilities.










