Enterprise-grade service mesh for
development and governance
Connect, manage, and secure workloads across any environment and platform. Reduce developer time to value by managing boilerplate work for retries, service-to-service encryption, chaos engineering and service discovery.

Modern environments get complicated.
Kong simplifies things.
Apply consistent security standards and governance across all services and locations from a single control plane.
Achieve uptime goals with intelligent failover and deep observability.
Deploy confidently and efficiently with a single solution anywhere you want to run.
Why Kong Mesh?
Kong Mesh simplifies cross-zone connectivity, security, observability, and compliance for Platform Operators, and reduces time to value for your developers.
More time
developing, less
worrying about
infrastructure
- Use Mesh features to handle retry logic, observability and chaos engineering at the platform layer.
- Seamlessly integrate with CI/CD pipelines and eliminate drift with declarative configuration.
- Speed up time to value with a mesh built to operate everywhere from day one.
Deploy microservices confidently
- Consistently apply authentication, API security, and traffic control policies across all services in one-click.
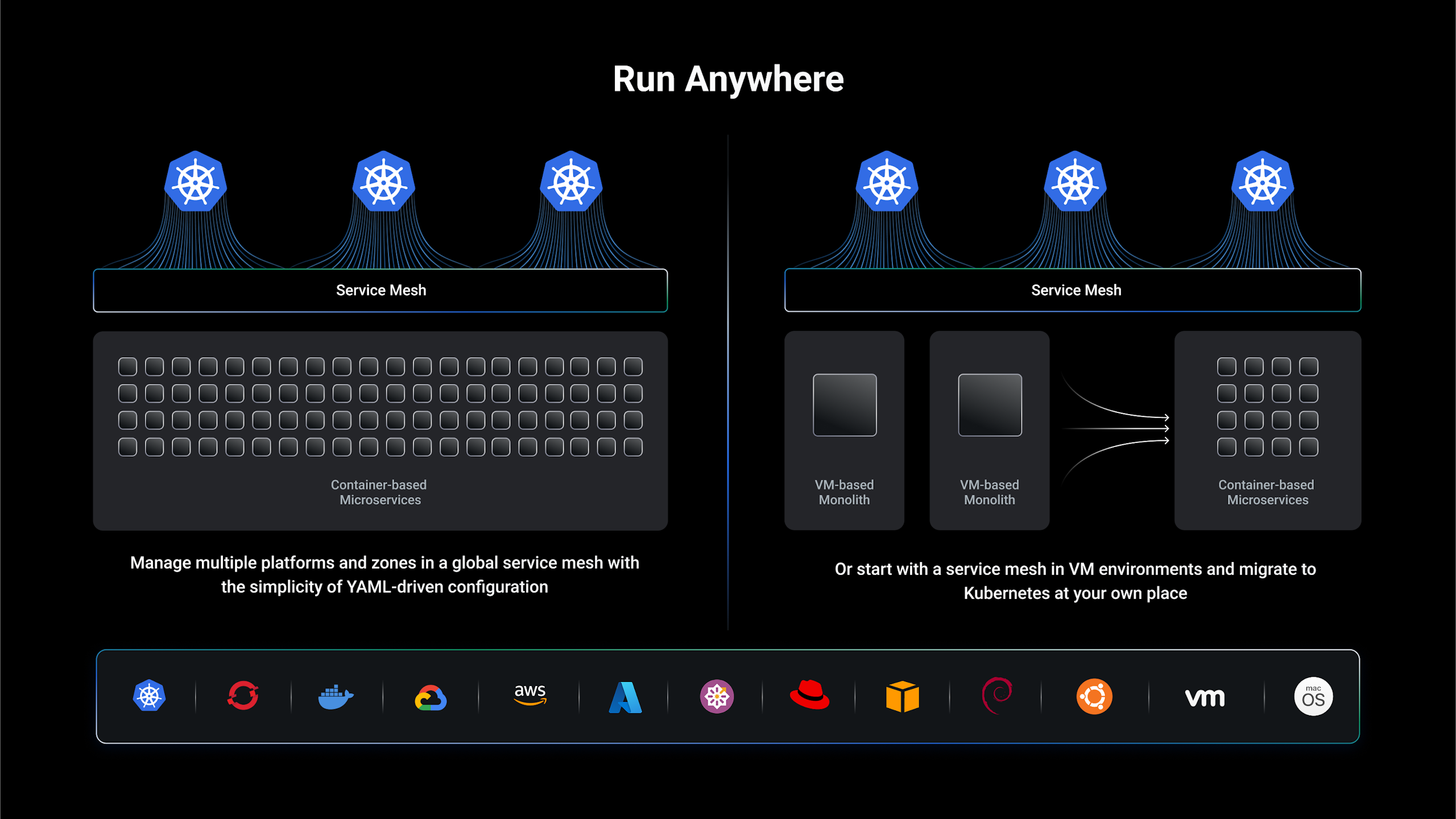
- Deploy Kong Mesh anywhere: on Kubernetes, in the cloud, on-premises, with containers or on virtual machines.
Reduce complexity
- Gain one-click control across service mesh environments with out-of-the-box policies for connectivity, observability, and security.
- Easily install and manage through Kong Konnect — the industry’s first unified SaaS control plane.
“Kong Mesh’s ease of use and built-in automation capabilities offer an alternative to some complex open-source solutions that are difficult to deploy and manage.” GigaOM Radar for Service Mesh 2023
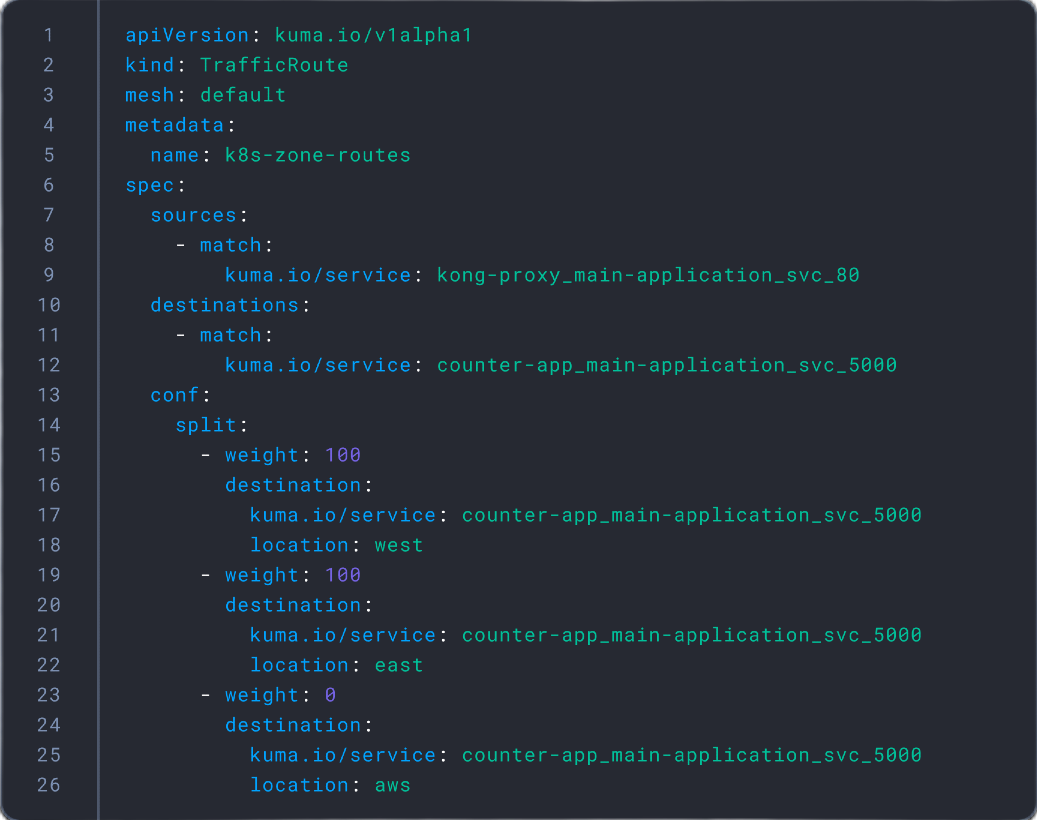
Ensure continuity
- Speed up reliability testing with a Circuit Breaker policy to test failures in a controlled manner.
- Reduce risk when you enable locality aware routing to route traffic effortlessly across multiple Kubernetes clusters or environments and roll out upgrades without disruption.
Zero-trust security across all Mesh deployments
- Achieve Zero Trust by default with authentication, authorization, and encryption technologies with a couple of clicks or a single command line entry.
- Get time back and reduce errors with automated security deployments and updates. Eliminate tedious, error-prone manual tasks by leveraging built-in configuration management.
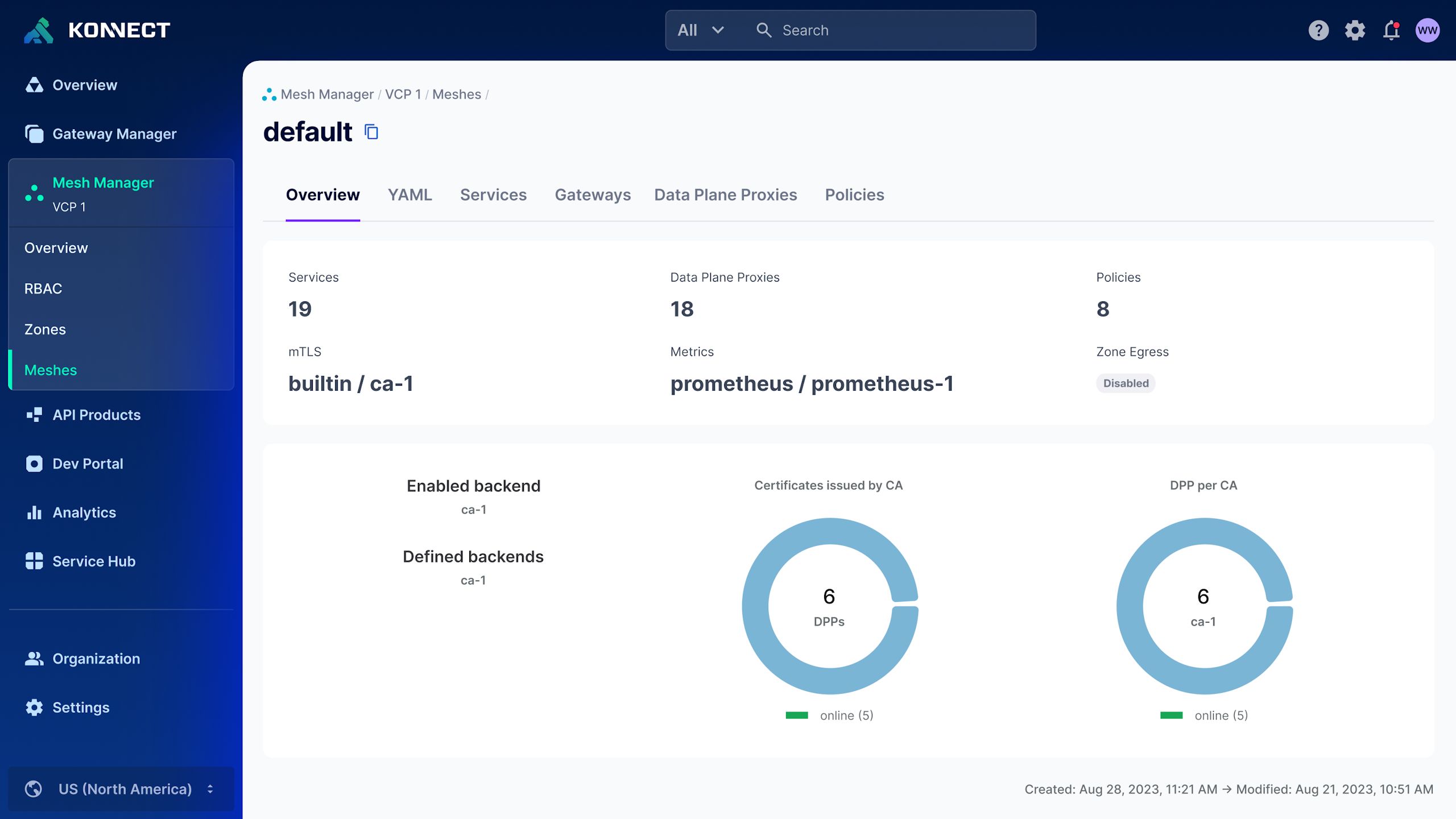
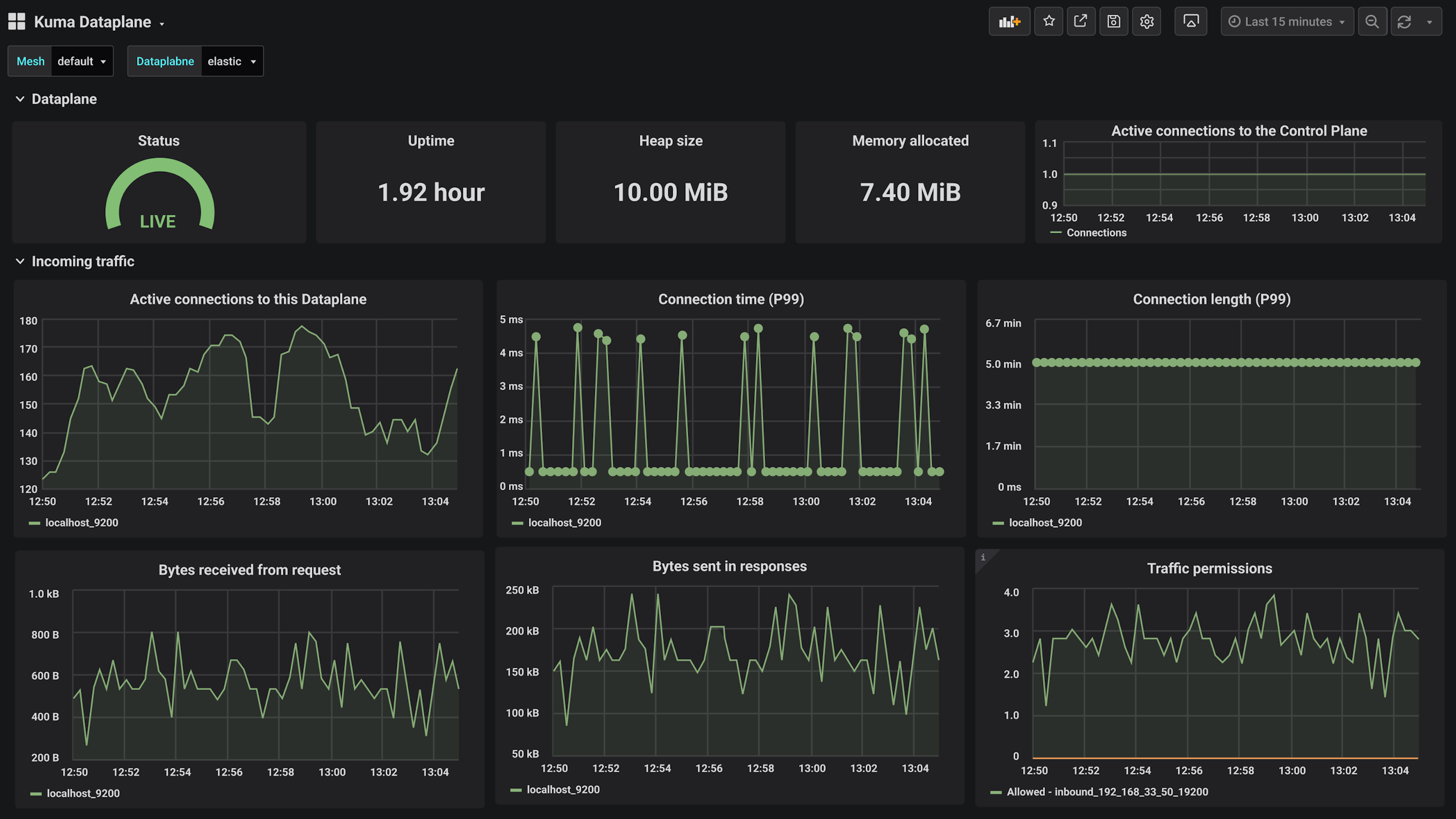
Gain real-time visibility into all services
- Gain deep insights into application usability with metrics such as error rate and latency for each service.
- Improve your security posture with a centralized management plane that aids in the secure deployment, timely audit, and application of security updates.





Customers on Kong Mesh
[With Kong] we created a scalable, highly reliable platform for our web applications that has a security-first mindset.
We chose Kong Mesh because we needed a solution that allows our customers to support Kubernetes and virtual machines, while providing an easier path to migrating between the two.
Transactions per second
...Kong Mesh is a critical aspect of our architecture, for both zero-trust security and observability and monitoring.
Resources
Get started with Kong Mesh
See how you can leverage Kong Mesh to connect, manage, and secure digital experiences — across any environment or platform.