Kong Gateway Tutorial: Running With a GUI in <15 Minutes
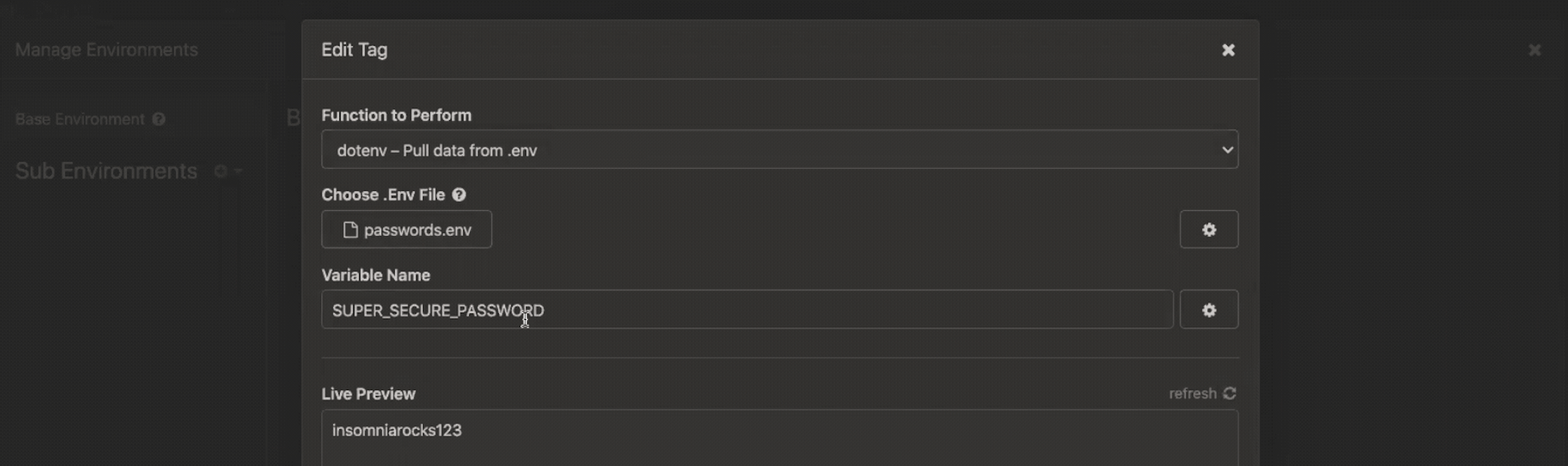
In this Kong Gateway tutorial, you'll learn how to: Keep in mind that these instructions are a starting point. You may need to change some of the steps to harden your environment when running in production. For more detailed information, visit our Kong Gateway documentation . One of the reasons…