We are truly excited to release Kong Mesh 1.2 today and introduce three new security capabilities that make it the most secure enterprise service mesh available today.
Kong Mesh is built on open source Kuma which Kong created in 2019 and has since donated it to the CNCF. Kuma is a universal control plane for service mesh that is based on Envoy. Its breakthrough architecture was developed to solve real-world customer issues, enabling it to run across multiple clusters, in every cloud and every application runtime.
Why Kuma?
We think of Kuma as an extensible and flexible service connectivity overlay that discovers and connects services automatically, including over hybrid Kubernetes and VM services.
By leveraging this unique design, Kong Mesh 1.2 brings the following unprecedented out-of-the-box security to our customers' services:
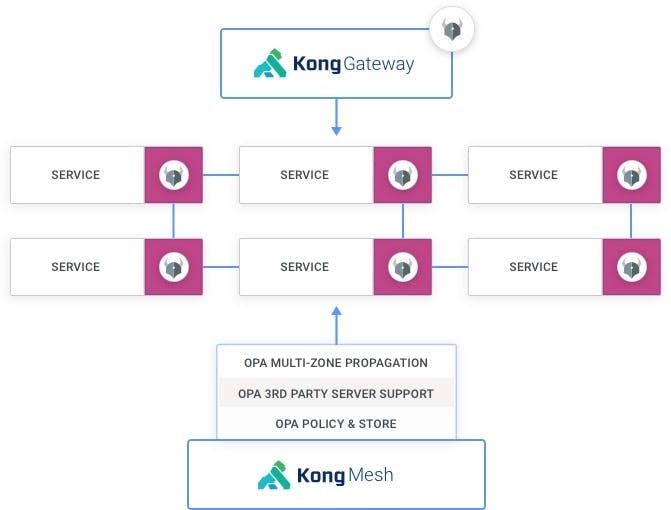
Native Integration With OPA Within the Service Mesh
Kong Mesh 1.2 is the first and only service mesh that is natively integrated with Open Policy Agent (OPA) as a first-class citizen, now a graduated CNCF project. This makes Kong Mesh the easiest product in the entire industry to deploy OPA across every application in our organization. For developers, this is like service mesh security nirvana!
- There are no additional OPA agent sidecars to deploy and manage. Kong Mesh enables customers to leverage OPA's policy engine out of the box across both Kubernetes and VMs without having to deploy an additional sidecar by providing embedded OPA support in the data plane process, therefore enormously simplifying day-2 operations.
- Out of the box, customers can implement standardized authentication and authorization rules via a native “OPA Policy” that will be consistently applied across workloads, regardless of language, platform, etc. This solves a big challenge companies face today, making it fast and easy to do so. Kong Mesh will be in charge of propagating automatically the OPA policies across every zone, cloud and cluster while still allowing users to connect to remote OPA servers like Styra to manage their OPA policies.
- Kong Mesh's native OPA support, combined with the existing OPA support in Kong Gateway, provides organizations with a standardized way to implement AuthN/Z across the full stack, from gateway to service mesh, and across both Kubernetes and VMs.
"Open Policy Agent solves authorization problems across the cloud native stack, including microservice API protection, Kubernetes admission control, CICD pipelines, public cloud configuration and database query access controls," said Tim Hinrichs, CTO of Styra and co-creator of OPA. "OPA is especially well-suited for microservice API authorization because it provides extremely fast, context-aware authorization decisions using policies that are decoupled from the microservice itself — so security, compliance, operations and dev teams can collaborate to implement, review and update policies without changing underlying services or application code."
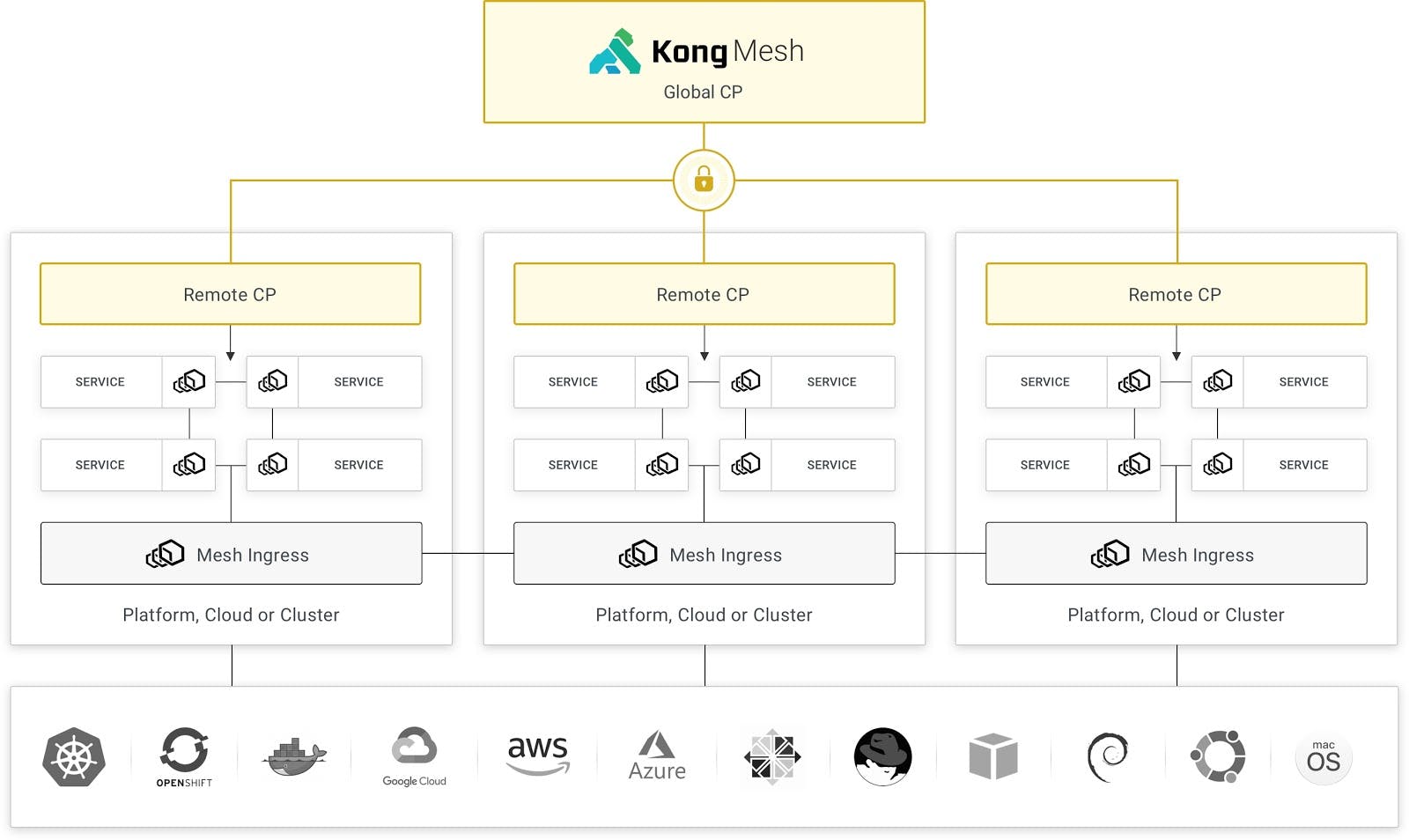
Enhanced Security for Multi-Zone Service Mesh
Historically, Kong Mesh has leveraged Kuma’s multi-zone support to enable distributed service mesh use cases. These distributed service meshes are typically clusters that exist between on-premises data center environments, cloud providers, VPCs or even separation based on workload runtime (like Kubernetes or VM).
With Kong Mesh 1.2, we’re enhancing that multi-zone functionality by providing an enterprise authentication mechanism between the global and remote control planes. This functionality extends the KDS (Kuma Discovery Service, the xDS-based API that connects the global and the remote control planes together) to support additional authentication capabilities within the architecture and enables enterprise teams to support global use cases while improving the security footprint within the service mesh control plane.
Native FIPS 140-2 Support
As the service mesh design pattern grows in adoption within workload environments, there’s a growing focus on compliance for the underlying service mesh platform. For Envoy-based service meshes, this compliance with the Federal Information Processing Standard (FIPS) has been challenging to achieve. Today, we are happy to announce that Kong Mesh ships with FIPS 140-2 compliance out of the box on every official distribution, including Kubernetes and VMs.
The inclusion of FIPS 140-2 compliance out of the box, as well as automated third-party Certificate Authority support (through HashiCorp Vault), Traffic Permission policies and native Open Policy Agent support establish a foundation of zero-trust within an organization's service connectivity platform.
Day-0 Security Compliance
These capabilities make Kong Mesh the easiest way to accelerate day-0 security compliance across the entire organization - preventing breaches and data loss, as well as increasing the security posture of the organization as a whole.
"Honestly, I am not sure how we ran our day to day without Kong Mesh before," said Aaron Weikle, CEO and founder of MS3. "We used to use MuleSoft to drive MS3's day-to-day business, but we were constantly battling issues with observability when customers would send in dirty data as well as understanding where issues arise or where delays would occur. In addition, the concept of zero-trust wasn’t possible with MuleSoft, and Crypto Miners at one point were able to gain access to our API platform. With Kong and Kong Mesh, we have established a tight-knit zero-trust platform with certificate rotation that makes it nearly impossible to penetrate and keeps our business and services running smoothly, saving a ton of operation dollars chasing issues that before we just couldn’t pinpoint."
Technology teams know that a security breach is only one-click away and can happen to anyone, instantly wrecking an organization's reputation and putting customers, partners and staff at risk. The new release of Kong Mesh fundamentally changes the way service mesh is secured and eliminates the drudgery typically associated with advanced security and zero-trust models.
To learn more about Kong Mesh 1.2 and our Kong Konnect platform, schedule a demo today!










