CORS Framework Deep Dive
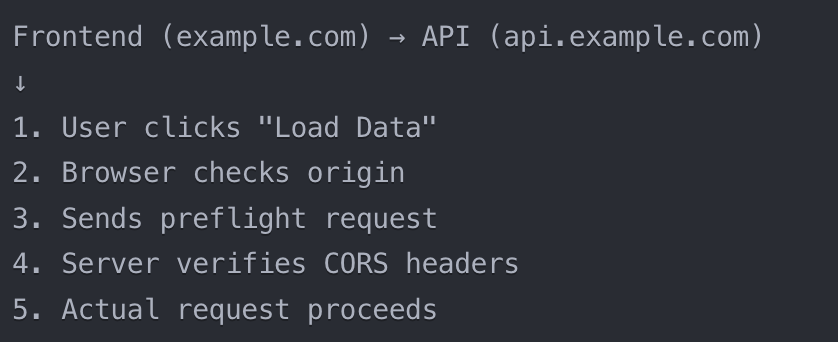
Now, let's look closely at the technical details of the CORS framework. We will discuss different types of CORS requests and check the headers involved.
Understanding these points will help you set up CORS the right way. It will also help you fix problems during development. When you know these details, you can make sure your web application works well with outside resources, giving users a smooth experience.
Simple vs Preflight Requests
CORS uses two kinds of requests to handle access across different origins: simple requests and preflight requests. Knowing the difference between these two requests is important for safe and effective cross-origin communication.
Simple requests are basic requests that meet certain criteria, making them safer. They usually use common HTTP methods like GET and POST and have limited custom headers, which follow the CORS standards. Because these requests are seen as safe, they don't need a preflight check.
Preflight requests are different. They happen when the browser thinks a request might change data on the server or use complex headers or methods. For example, if the request uses methods like PUT, DELETE, or custom headers that aren't allowed by the CORS settings, it will trigger a preflight request. This serves as a check where the browser asks the server for permission before making the actual request.
Here are the common situations that bring up preflight requests:
- HTTP methods other than GET, HEAD, or POST
- Content-Type headers that are not application/x-www-form-urlencoded, multipart/form-data, or text/plain
- Custom headers that are not in the CORS-safelisted request-headers
CORS uses certain HTTP headers to manage how different sites talk to each other. These headers help the browser and the server communicate. They set rules about what actions are allowed and how data can be shared.
The key CORS header is the Access-Control-Allow-Origin header. It tells the server which sites can access its resources. The server can set this header to a specific site, like https://www.example.com, or use a wildcard (*). However, using a wildcard is usually not safe because it lets everyone in.
There are other vital CORS headers too, like Access-Control-Allow-Methods, Access-Control-Allow-Headers, and Access-Control-Allow-Credentials. These headers decide which HTTP methods can be used (like GET, POST, and PUT), which custom headers are okay, and if credentials such as cookies or authorization headers can be included with the request.
Common CORS Use Cases and Solutions
CORS setups can be easy, but depending on the level of complexity your needs are, it can become increasingly more complicated. They can do anything from handle simple requests to manage sensitive data with authentication. It is important to identify your specific needs and know the different situations and their solutions, so it becomes easier to use CORS in various development spaces.
In this section, we will look at some typical situations. We will begin with a simple CORS setup. Then, we will move to more complex cases that include authenticated requests. By reviewing these examples, developers can learn how to configure CORS well. This will help them meet their needs and keep cross-origin communication safe.
Basic CORS Setup
Setting up CORS for simple requests is usually easy. Most of the time, you need to configure the server to add the Access-Control-Allow-Origin header to its replies. This header shows which origins can access the server's resources.
For example, to allow requests from a specific site like https://www.example.com, the server should add this header:
Access-Control-Allow-Origin: https://www.example.com
To let requests from any origin, which is not safe, the server can use a wildcard:
Access-Control-Allow-Origin: *
Just adding the header is not enough. The server also needs to let the specific HTTP methods that are used in the request. The web server software, like Apache or Nginx, usually manages this based on its settings.
Handling Authenticated Requests
Handling authenticated requests with CORS can be tricky. The browser must send credentials like cookies or authorization headers to check who you are. By default, browsers do not send these credentials with cross-origin requests unless they are told to do so.
To allow this, the server must add the Access-Control-Allow-Credentials header and set it to true in its response. This tells the browser that the server is ready to accept credentials and will manage them safely.
Access-Control-Allow-Credentials: true
Also, when the server responds to a request with credentials, it needs to clearly list the origin in the Access-Control-Allow-Origin header. Using wildcards is not allowed here. This step ensures that credentials only go to trusted origins.
Even if CORS is set up properly, keeping sensitive data safe depends on strong authentication methods on the server side.
Error Scenarios
Despite careful setup, it's common to face CORS errors during development. These issues often happen because of differences in the CORS headers sent between the browser and the server or incorrect settings on either side. Knowing the usual error types and their reasons can help you find and fix them quickly.
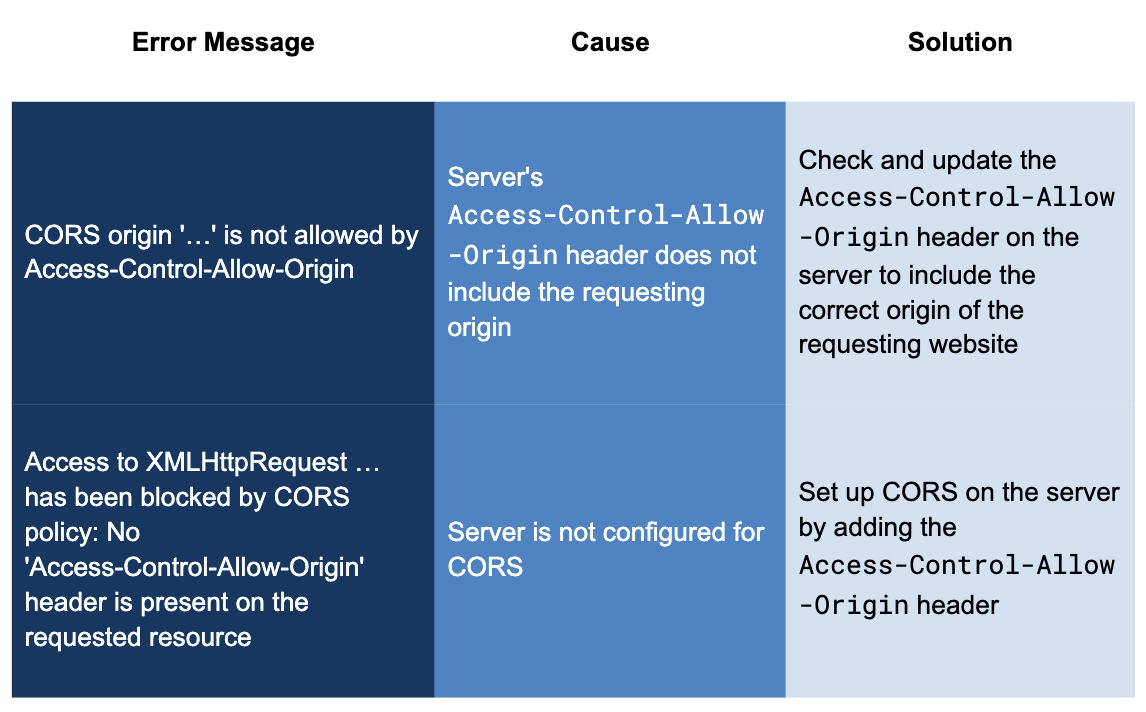
A common error you might see is "CORS origin '…' is not allowed by Access-Control-Allow-Origin." This message means that the server's Access-Control-Allow-Origin header does not include the origin of the website making the request. This may happen because the server's CORS settings are too strict or because the origin request is wrong.
Another frequent error is "Access to XMLHttpRequest … has been blocked by CORS policy: No 'Access-Control-Allow-Origin' header is present on the requested resource." This error shows that the server is not set up for CORS at all.
Cross Origin Security Implications
CORS itself is not a threat, but if it is not set up correctly, it can create security problems. Poor CORS settings might weaken the Same-Origin Policy, which could let unauthorized users access your resources.
Keep in mind that CORS is mainly enforced by the browser. It controls how browsers manage requests from different origins. However, it cannot stop bad clients from sidestepping these rules and making direct requests to the server. This means you should not depend only on CORS for security.
CORS Role in Security
CORS is not a security tool by itself, but it is important for improving security in web applications. It controls access from different origins. Its main job is to stop harmful websites from misusing safe websites in cross-origin requests.
One major advantage of CORS is that it helps reduce risks from Cross-Site Scripting (XSS) weaknesses. By allowing only certain origins to access a website’s resources, CORS can stop attackers from using stolen cookies or session tokens from an XSS attack on a weak site. This makes it harder for them to make unauthorized requests to the targeted site.
It's very important to know that CORS needs to be set up correctly to work well. If the settings are too relaxed, like using wildcards in the Access-Control-Allow-Origin header, it can remove the security benefits and make your application exposed to weaknesses. So, following the best security practices and testing your CORS setup properly is very important.
Common Mistakes
One common mistake when setting up CORS is using the Access-Control-Allow-Origin header with a wildcard (*). This is popular but risky, especially for apps with sensitive information. It allows any domain to access your app. This breaks the origin policy and makes your app open to attacks.
Another mistake is not stating the allowed HTTP methods and headers. If you rely on default settings or skip specific methods, you may expose your app to Cross-Site Request Forgery (CSRF) attacks.
Also, not properly checking user input for CORS headers can lead to problems. Bad users might find ways to add harmful origins or change header values. This could help them get around your CORS security. To reduce this risk, you need to validate and clean input carefully.
CORS Implementation Checklist
Successfully using CORS takes thought for both the front end and back end. The details may change depending on your app and tech stack, but there are some general tips that can help make your CORS setup work well and safely.
This checklist shows important things to think about in both front end and back end work. This will help your CORS run correctly and avoid problems with access and security risks.
Frontend Considerations
From the frontend side, making client web applications that connect with external APIs means you need to understand how CORS works on the client side. Most of the CORS setup happens on the server side, but frontend developers must pay attention to some details to avoid problems.
First, make sure that the API requests from your client application include the right headers. Most modern JavaScript frameworks and libraries take care of CORS preflight requests automatically. Still, it's important to check that the correct Origin header is sent with each request. This header tells the server where the request originates.
Second, if your application uses cookies or authentication headers, check that the server allows credentials. You usually do this by setting the withCredentials property to true when making AJAX requests with fetch or XMLHttpRequest. Lastly, test your setup thoroughly with different browsers and devices to make sure everything works the same way on various platforms.
Backend Implementation
Implementing CORS securely and effectively depends on how well you set up your server. You must make your server respond correctly to cross-origin requests. It is important that only allowed sites can access your resources.
First, configure your web server software like Apache or Nginx. You can also use server-side frameworks that already have CORS support. The main part of this setup is to add the right CORS headers, especially the Access-Control-Allow-Origin header. This header tells which sites are allowed.
If your application handles sensitive data and needs user login, you should set the Access-Control-Allow-Credentials header to true. This is necessary if you want to allow credentials such as cookies or authorization headers. But be careful with this setting and check user inputs carefully to avoid security issues. Strong server-side authentication and authorization are key to keeping your data safe. Remember, CORS is meant to support already existing security measures, not replace them.
Let’s Recap
CORS represents a critical balance between security and functionality in modern web development. While it may initially seem like a hurdle, especially during development, CORS serves as an essential security mechanism that protects users and applications from potentially malicious cross-origin requests. By following the best practices outlined in this guide, developers can implement CORS configurations that maintain security without sacrificing functionality. Remember that CORS is just one piece of a comprehensive security strategy – it works best when combined with other security measures like proper authentication, input validation, and secure communication protocols. As web applications continue to become more distributed and interconnected, mastering CORS will remain an essential skill for web developers who want to build secure, efficient, and user-friendly applications.
Frequently Asked Questions
What exactly is CORS?
CORS, which stands for Cross-Origin Resource Sharing, is a way for a web browser to ask for resources from a server that is on a different domain. This means that the server is not the same as the one where the browser loaded the page. It uses special HTTP headers to show what is allowed between the browser and the server.
What's the difference between CORS and API keys?
CORS and API keys have different jobs. CORS, which stands for Cross-Origin Resource Sharing, is a system in the browser. It manages who can access resources from different places. On the other hand, API keys help with authentication. They help identify the application making the request. API keys are not linked to any one specific origin.
Why do I need CORS if I have authentication?
Authentication checks who you are. CORS, which stands for Cross-Origin Resource Sharing, manages access from other websites. Even if you have authentication in place, you still need CORS. It allows approved sites to use resources on your server.
Do I need CORS for my mobile app?
CORS is a security feature used by browsers. Mobile apps that make HTTP requests directly do not follow the same rules as web browsers. Therefore, CORS does not apply to them.